Volatility
工具简介:
Volatility 是由 Volatility Foundation 开发和维护的免费内存取证工具,通常由蓝队内的恶意软件和SOC分析师使用,或作为其检测和监控解决方案的一部分。Volatility 是用 Python 编写的,由 Python 插件和模块组成,设计为分析内存转储的即插即用方式。
Volatility 适用于 Windows、Linux和 Mac OS,并且完全用 Python 编写。
版本
目前主流的有Volatility2和Volatility3两个版本
Volatility2
很完善的一个版本,各个插件都有,除了他的开发版本,还有他的编译版本,较为方便
Volatility3
处于一个刚开始的阶段,各方面不是特别完善
Volatility2的所有语法在 volatility3 中都发生了变化,这里我们学习最新的volatility3语法
下载地址
Volatility2:https://github.com/volatilityfoundation/volatility
Volatility3:https://github.com/volatilityfoundation/volatility3
这里优先使用git下载Volatility3
git clone https://github.com/volatilityfoundation/volatility3.git
Volatility3使用方法
使用上述命令clone项目后进入文件夹
使用命令
python3 vol.py -h
查看帮助
帮助菜单
python3 vol.py -h
Volatility 3 Framework 2.4.1
usage: volatility [-h] [-c CONFIG] [--parallelism [{processes,threads,off}]]
[-e EXTEND] [-p PLUGIN_DIRS] [-s SYMBOL_DIRS] [-v] [-l LOG]
[-o OUTPUT_DIR] [-q] [-r RENDERER] [-f FILE] [--write-config]
[--save-config SAVE_CONFIG] [--clear-cache] [--cache-path CACHE_PATH]
[--offline] [--single-location SINGLE_LOCATION]
[--stackers [STACKERS ...]]
[--single-swap-locations [SINGLE_SWAP_LOCATIONS ...]]
plugin ...
An open-source memory forensics framework
options:
-h, --help Show this help message and exit, for specific plugin options
use 'volatility <pluginname> --help'
-c CONFIG, --config CONFIG
Load the configuration from a json file
--parallelism [{processes,threads,off}]
Enables parallelism (defaults to off if no argument given)
-e EXTEND, --extend EXTEND
Extend the configuration with a new (or changed) setting
-p PLUGIN_DIRS, --plugin-dirs PLUGIN_DIRS
Semi-colon separated list of paths to find plugins
-s SYMBOL_DIRS, --symbol-dirs SYMBOL_DIRS
Semi-colon separated list of paths to find symbols
-v, --verbosity Increase output verbosity
-l LOG, --log LOG Log output to a file as well as the console
-o OUTPUT_DIR, --output-dir OUTPUT_DIR
Directory in which to output any generated files
-q, --quiet Remove progress feedback
-r RENDERER, --renderer RENDERER
Determines how to render the output (quick, none, csv, pretty,
json, jsonl)
-f FILE, --file FILE Shorthand for --single-location=file:// if single-location is
not defined
--write-config Write configuration JSON file out to config.json
--save-config SAVE_CONFIG
Save configuration JSON file to a file
--clear-cache Clears out all short-term cached items
--cache-path CACHE_PATH
Change the default path (/root/.cache/volatility3) used to
store the cache
--offline Do not search online for additional JSON files
--single-location SINGLE_LOCATION
Specifies a base location on which to stack
--stackers [STACKERS ...]
List of stackers
--single-swap-locations [SINGLE_SWAP_LOCATIONS ...]
Specifies a list of swap layer URIs for use with single-
location
Plugins:
For plugin specific options, run 'volatility <plugin> --help'
plugin
banners.Banners Attempts to identify potential linux banners in an image
configwriter.ConfigWriter
Runs the automagics and both prints and outputs configuration
in the output directory.
frameworkinfo.FrameworkInfo
Plugin to list the various modular components of Volatility
isfinfo.IsfInfo Determines information about the currently available ISF files,
or a specific one
layerwriter.LayerWriter
Runs the automagics and writes out the primary layer produced
by the stacker.
linux.bash.Bash Recovers bash command history from memory.
linux.check_afinfo.Check_afinfo
Verifies the operation function pointers of network protocols.
linux.check_creds.Check_creds
Checks if any processes are sharing credential structures
linux.check_idt.Check_idt
Checks if the IDT has been altered
linux.check_modules.Check_modules
Compares module list to sysfs info, if available
linux.check_syscall.Check_syscall
Check system call table for hooks.
linux.elfs.Elfs Lists all memory mapped ELF files for all processes.
linux.keyboard_notifiers.Keyboard_notifiers
Parses the keyboard notifier call chain
linux.kmsg.Kmsg Kernel log buffer reader
linux.lsmod.Lsmod Lists loaded kernel modules.
linux.lsof.Lsof Lists all memory maps for all processes.
linux.malfind.Malfind
Lists process memory ranges that potentially contain injected
code.
linux.mountinfo.MountInfo
Lists mount points on processes mount namespaces
linux.proc.Maps Lists all memory maps for all processes.
linux.psaux.PsAux Lists processes with their command line arguments
linux.pslist.PsList
Lists the processes present in a particular linux memory image.
linux.pstree.PsTree
Plugin for listing processes in a tree based on their parent
process ID.
linux.tty_check.tty_check
Checks tty devices for hooks
mac.bash.Bash Recovers bash command history from memory.
mac.check_syscall.Check_syscall
Check system call table for hooks.
mac.check_sysctl.Check_sysctl
Check sysctl handlers for hooks.
mac.check_trap_table.Check_trap_table
Check mach trap table for hooks.
mac.ifconfig.Ifconfig
Lists network interface information for all devices
mac.kauth_listeners.Kauth_listeners
Lists kauth listeners and their status
mac.kauth_scopes.Kauth_scopes
Lists kauth scopes and their status
mac.kevents.Kevents
Lists event handlers registered by processes
mac.list_files.List_Files
Lists all open file descriptors for all processes.
mac.lsmod.Lsmod Lists loaded kernel modules.
mac.lsof.Lsof Lists all open file descriptors for all processes.
mac.malfind.Malfind
Lists process memory ranges that potentially contain injected
code.
mac.mount.Mount A module containing a collection of plugins that produce data
typically found in Mac's mount command
mac.netstat.Netstat
Lists all network connections for all processes.
mac.proc_maps.Maps Lists process memory ranges that potentially contain injected
code.
mac.psaux.Psaux Recovers program command line arguments.
mac.pslist.PsList Lists the processes present in a particular mac memory image.
mac.pstree.PsTree Plugin for listing processes in a tree based on their parent
process ID.
mac.socket_filters.Socket_filters
Enumerates kernel socket filters.
mac.timers.Timers Check for malicious kernel timers.
mac.trustedbsd.Trustedbsd
Checks for malicious trustedbsd modules
mac.vfsevents.VFSevents
Lists processes that are filtering file system events
timeliner.Timeliner
Runs all relevant plugins that provide time related information
and orders the results by time.
windows.bigpools.BigPools
List big page pools.
windows.callbacks.Callbacks
Lists kernel callbacks and notification routines.
windows.cmdline.CmdLine
Lists process command line arguments.
windows.crashinfo.Crashinfo
windows.devicetree.DeviceTree
Listing tree based on drivers and attached devices in a
particular windows memory image.
windows.dlllist.DllList
Lists the loaded modules in a particular windows memory image.
windows.driverirp.DriverIrp
List IRPs for drivers in a particular windows memory image.
windows.driverscan.DriverScan
Scans for drivers present in a particular windows memory image.
windows.dumpfiles.DumpFiles
Dumps cached file contents from Windows memory samples.
windows.envars.Envars
Display process environment variables
windows.filescan.FileScan
Scans for file objects present in a particular windows memory
image.
windows.getservicesids.GetServiceSIDs
Lists process token sids.
windows.getsids.GetSIDs
Print the SIDs owning each process
windows.handles.Handles
Lists process open handles.
windows.info.Info Show OS & kernel details of the memory sample being analyzed.
windows.joblinks.JobLinks
Print process job link information
windows.ldrmodules.LdrModules
windows.malfind.Malfind
Lists process memory ranges that potentially contain injected
code.
windows.mbrscan.MBRScan
Scans for and parses potential Master Boot Records (MBRs)
windows.memmap.Memmap
Prints the memory map
windows.mftscan.MFTScan
Scans for MFT FILE objects present in a particular windows
memory image.
windows.modscan.ModScan
Scans for modules present in a particular windows memory image.
windows.modules.Modules
Lists the loaded kernel modules.
windows.mutantscan.MutantScan
Scans for mutexes present in a particular windows memory image.
windows.netscan.NetScan
Scans for network objects present in a particular windows
memory image.
windows.netstat.NetStat
Traverses network tracking structures present in a particular
windows memory image.
windows.poolscanner.PoolScanner
A generic pool scanner plugin.
windows.privileges.Privs
Lists process token privileges
windows.pslist.PsList
Lists the processes present in a particular windows memory
image.
windows.psscan.PsScan
Scans for processes present in a particular windows memory
image.
windows.pstree.PsTree
Plugin for listing processes in a tree based on their parent
process ID.
windows.registry.certificates.Certificates
Lists the certificates in the registry's Certificate Store.
windows.registry.hivelist.HiveList
Lists the registry hives present in a particular memory image.
windows.registry.hivescan.HiveScan
Scans for registry hives present in a particular windows memory
image.
windows.registry.printkey.PrintKey
Lists the registry keys under a hive or specific key value.
windows.registry.userassist.UserAssist
Print userassist registry keys and information.
windows.sessions.Sessions
lists Processes with Session information extracted from
Environmental Variables
windows.skeleton_key_check.Skeleton_Key_Check
Looks for signs of Skeleton Key malware
windows.ssdt.SSDT Lists the system call table.
windows.statistics.Statistics
windows.strings.Strings
Reads output from the strings command and indicates which
process(es) each string belongs to.
windows.svcscan.SvcScan
Scans for windows services.
windows.symlinkscan.SymlinkScan
Scans for links present in a particular windows memory image.
windows.vadinfo.VadInfo
Lists process memory ranges.
windows.vadyarascan.VadYaraScan
Scans all the Virtual Address Descriptor memory maps using
yara.
windows.verinfo.VerInfo
Lists version information from PE files.
windows.virtmap.VirtMap
Lists virtual mapped sections.
yarascan.YaraScan Scans kernel memory using yara rules (string or file).
The following plugins could not be loaded (use -vv to see why):
volatility3.plugins.windows.cachedump, volatility3.plugins.windows.hashdump,
volatility3.plugins.windows.lsadump
常见命令:
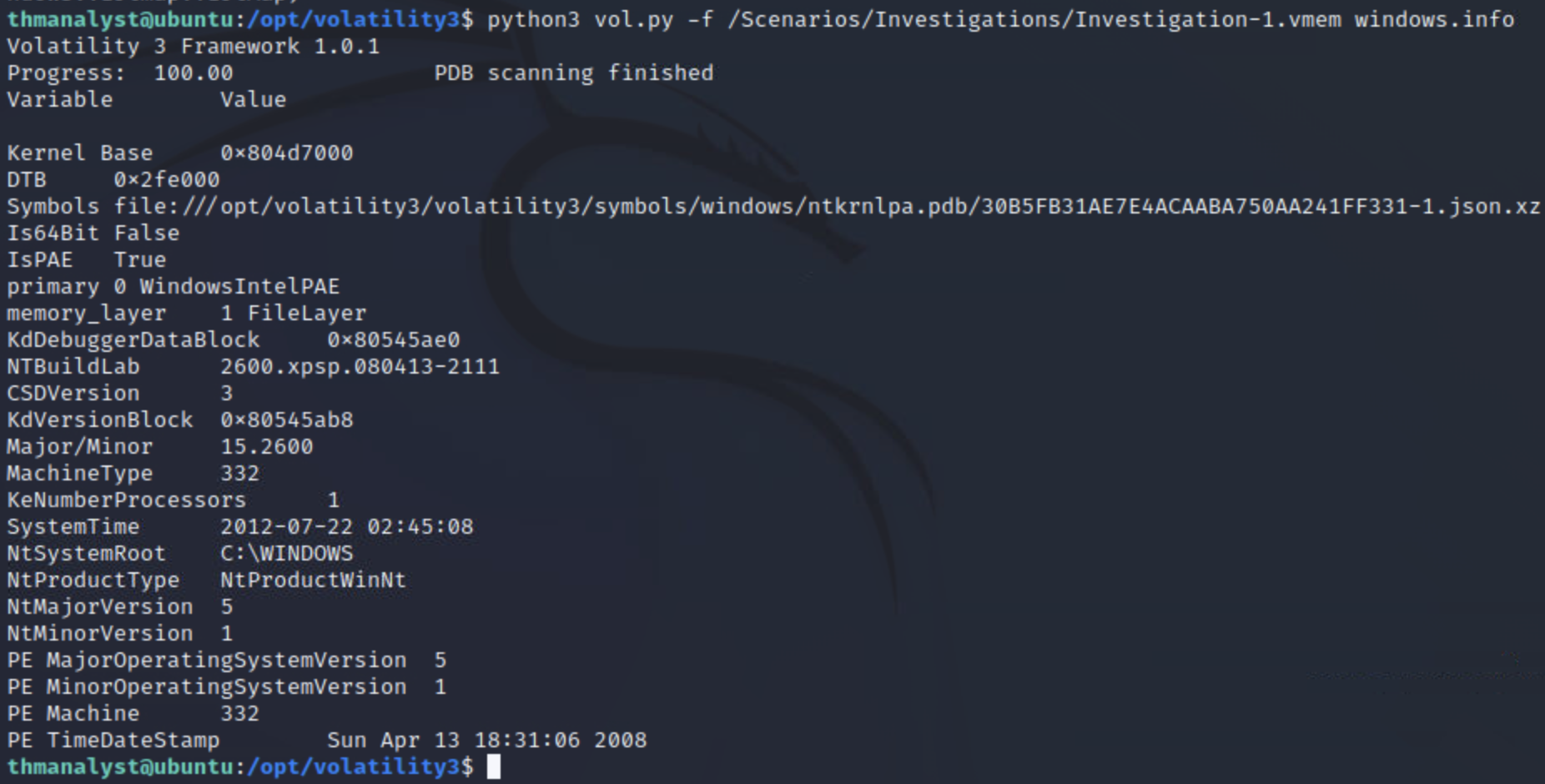
识别主机的相关信息
python3 vol.py -f 镜像文件 windows.info/linux.info/mac.info
Volatility3 弃用了Volatility2中最常用的imageinfo命令,如果我们仍然想从内存转储中提供有关主机的信息,则需要改用windows.info/linux.info/mac.info 命令
实例:使用windows info命令获取主机信息
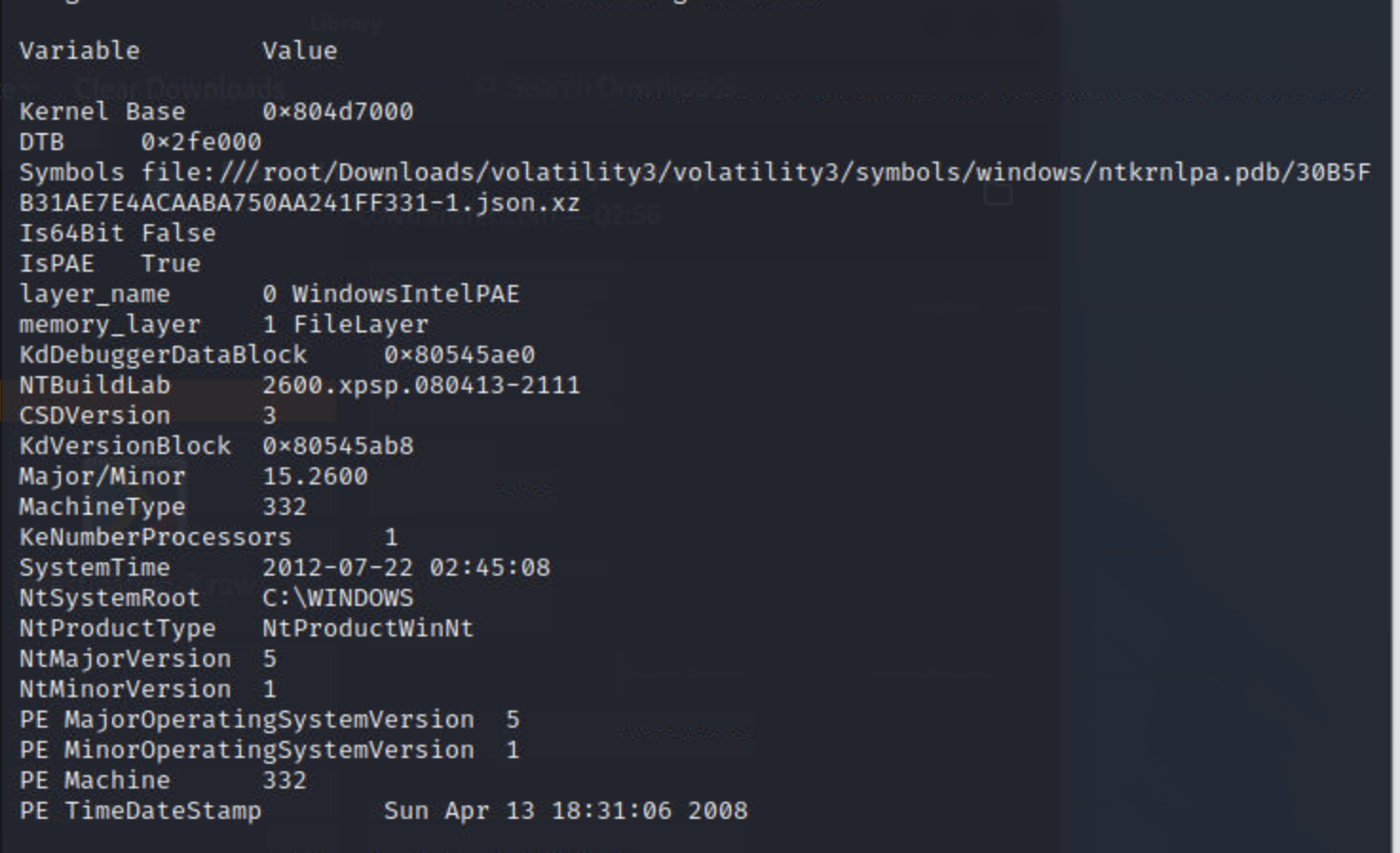
列出进程和连接
Volatility3 中的五个不同插件允许您转储进程和网络连接,每个都使用不同的技术。在此任务中,当涉及到对手使用的规避技术时,我们将讨论每种技术及其优缺点。
pslist
列出进程的最基本方法是使用pslist; 该插件将从跟踪内存中进程的双向链表中获取进程列表,相当于任务管理器中的进程列表。该插件的输出将包括所有当前进程和终止进程及其退出时间。
命令:
python3 vol.py -f <file> windows.pslist
实例:
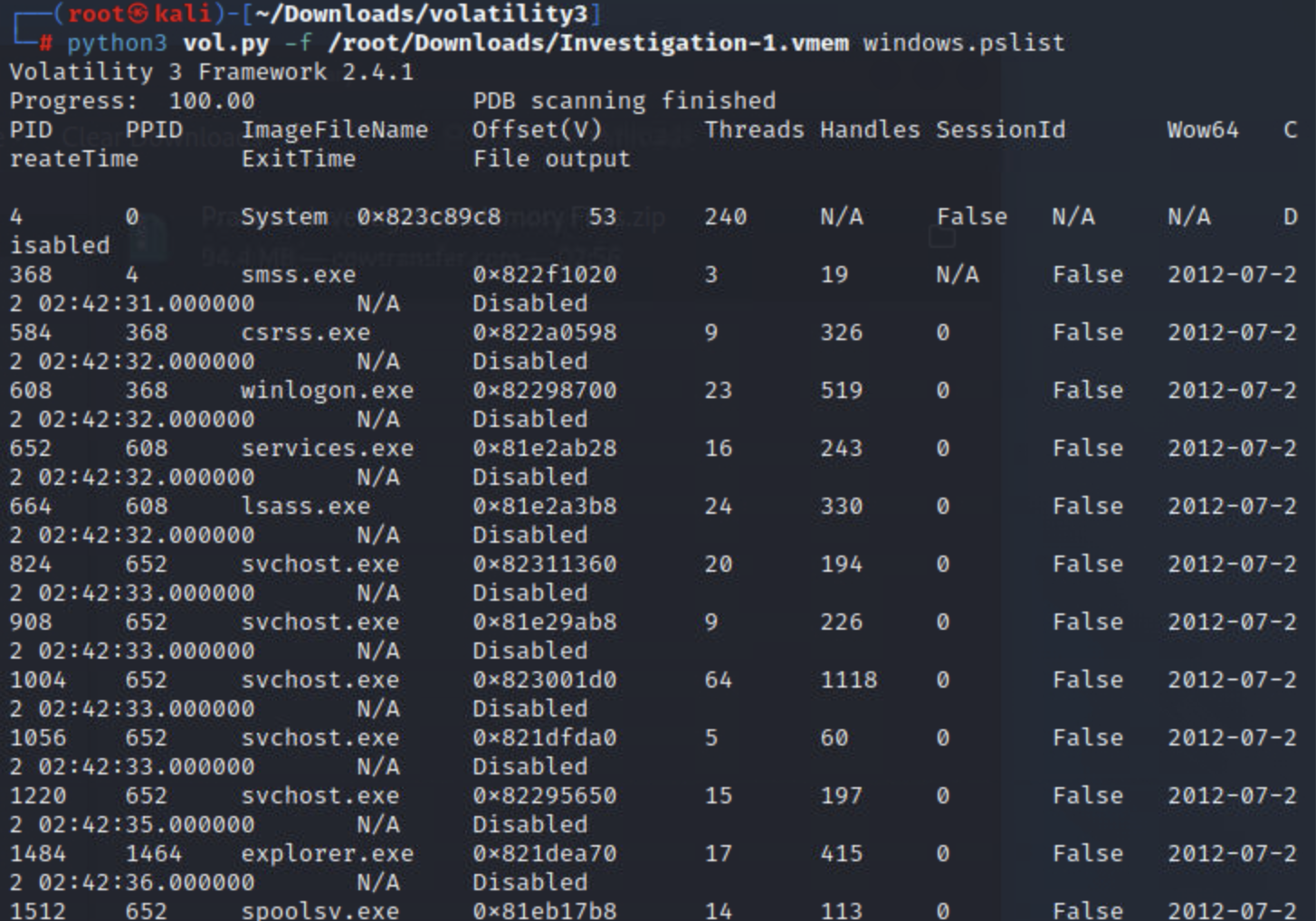
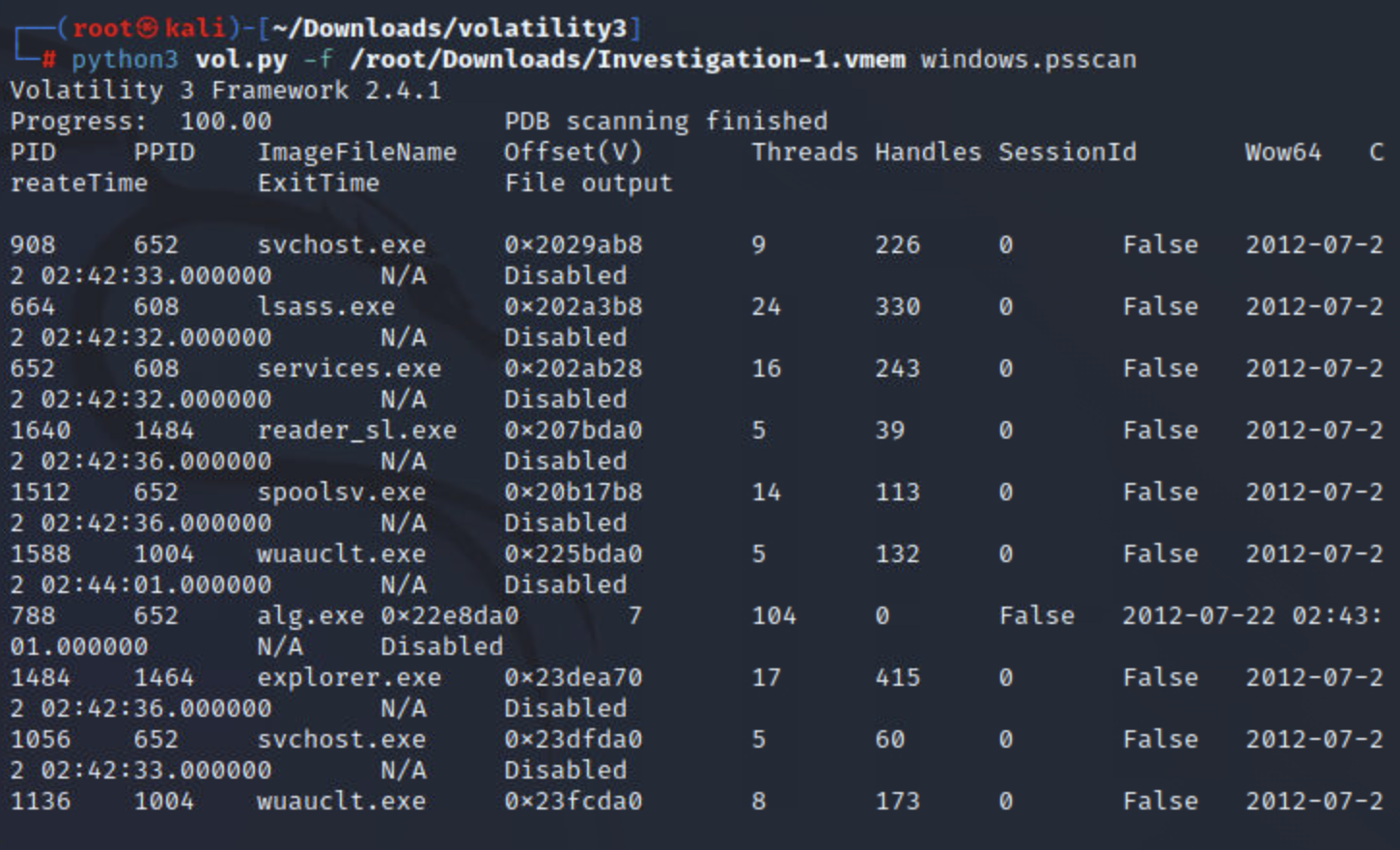
psscan
某些恶意软件(通常是 Rootkit)会试图隐藏它们的进程,并从列表中取消链接。通过从列表中取消链接,您在使用时将不再看到他们的进程pslist。为了对抗这种规避技术,我们可以使用psscan这种列出进程的技术将通过查找匹配的数据结构来定位进程_EPROCESS。虽然这种技术可以帮助规避对策,但它也可能导致误报。
命令:
python3 vol.py -f <file> windows.psscan
实例:
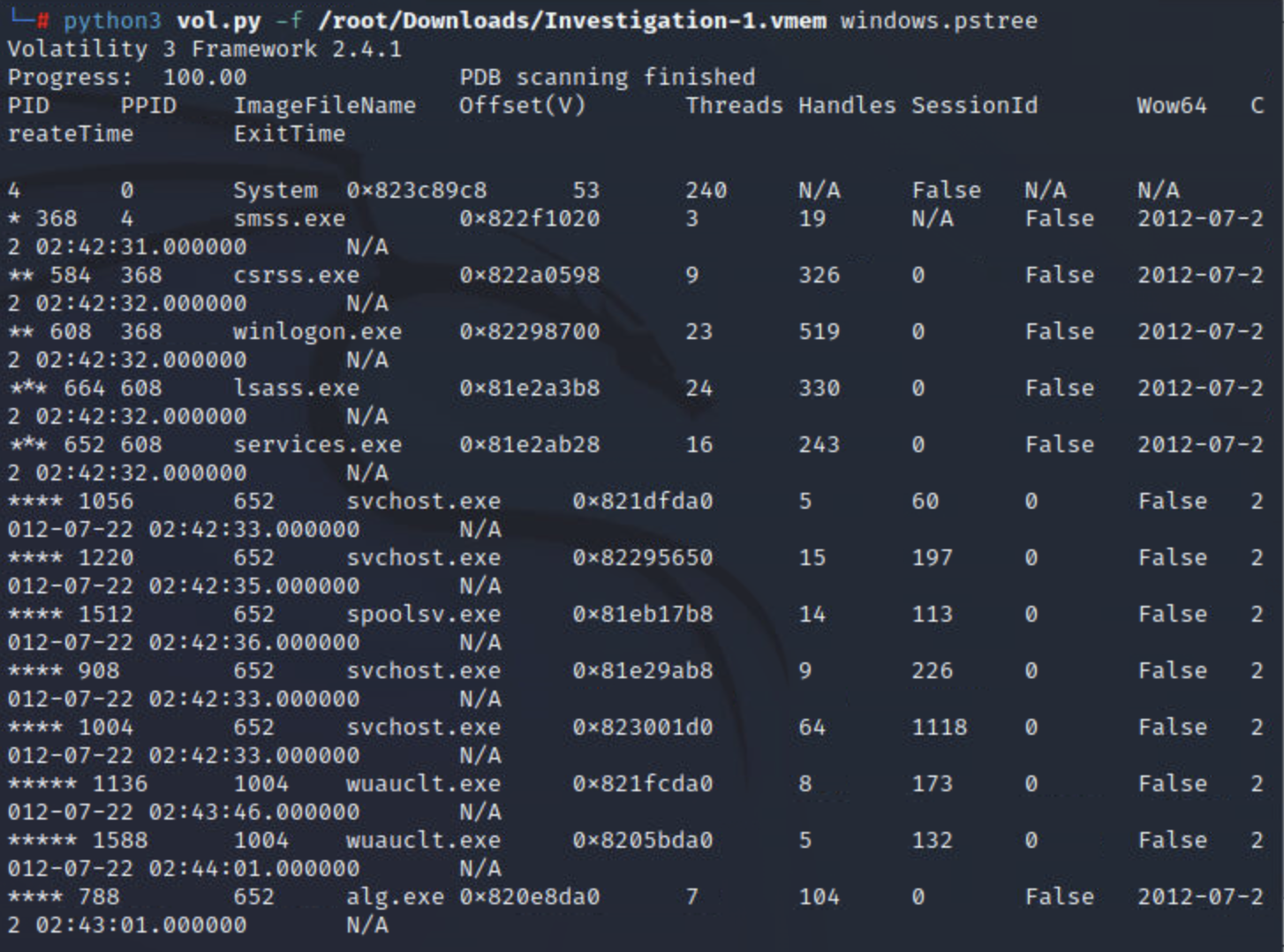
pstree
进程插件pstree没有像最后两个插件那样提供任何其他类型的特殊技术来帮助识别逃避;但是,此插件将根据其父进程 ID 列出所有进程,使用与pslist. 这对于分析师获取流程的完整故事以及提取时可能发生的情况很有用。
命令:
python3 vol.py -f <file> windows.pstree
实例:
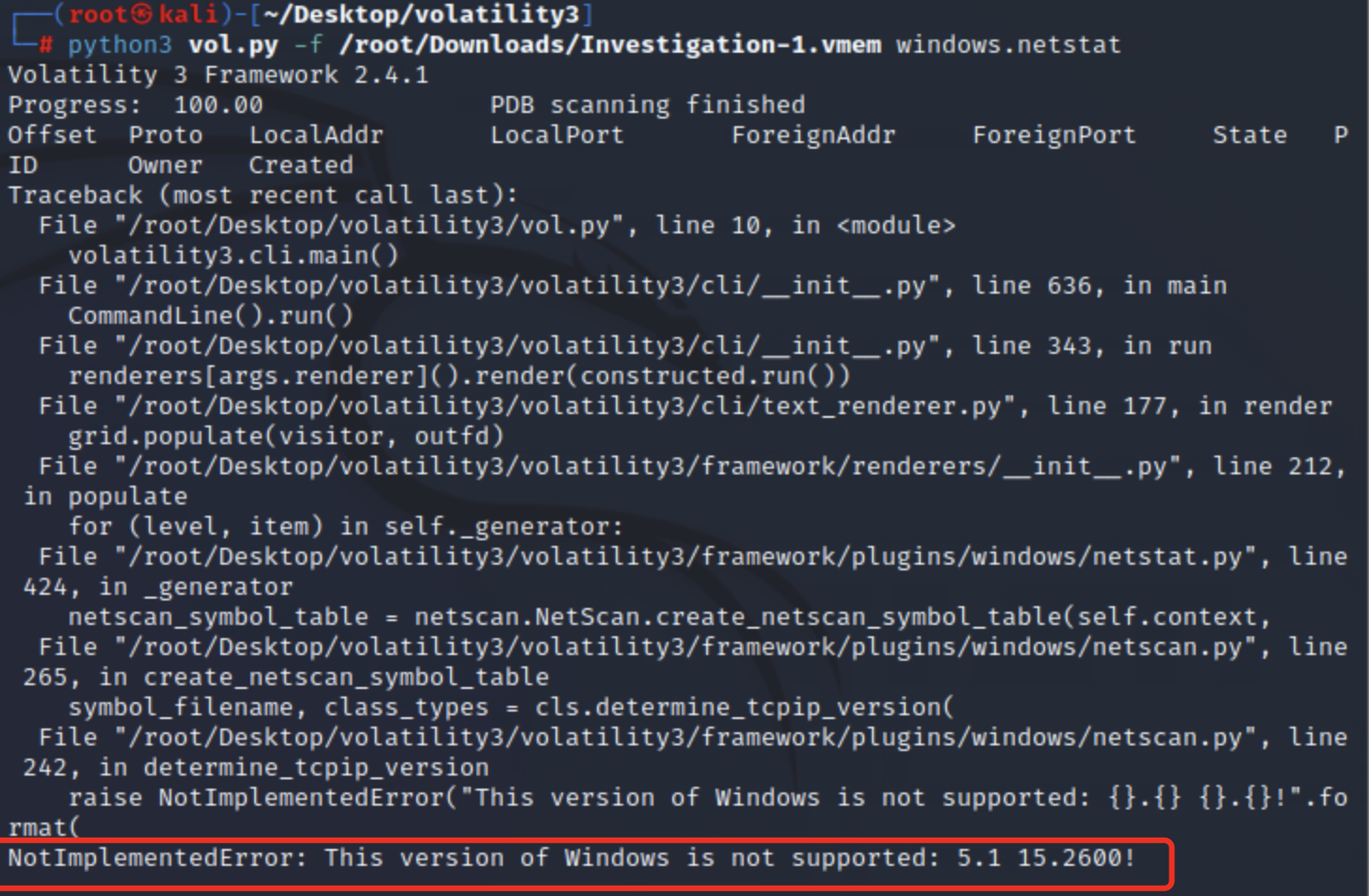
netstat
netstat可以尝试识别具有网络连接的所有内存结构,但是可能非常不稳定,尤其是在旧的 Windows 版本中
命令:
python3 vol.py -f <file> windows.netstat
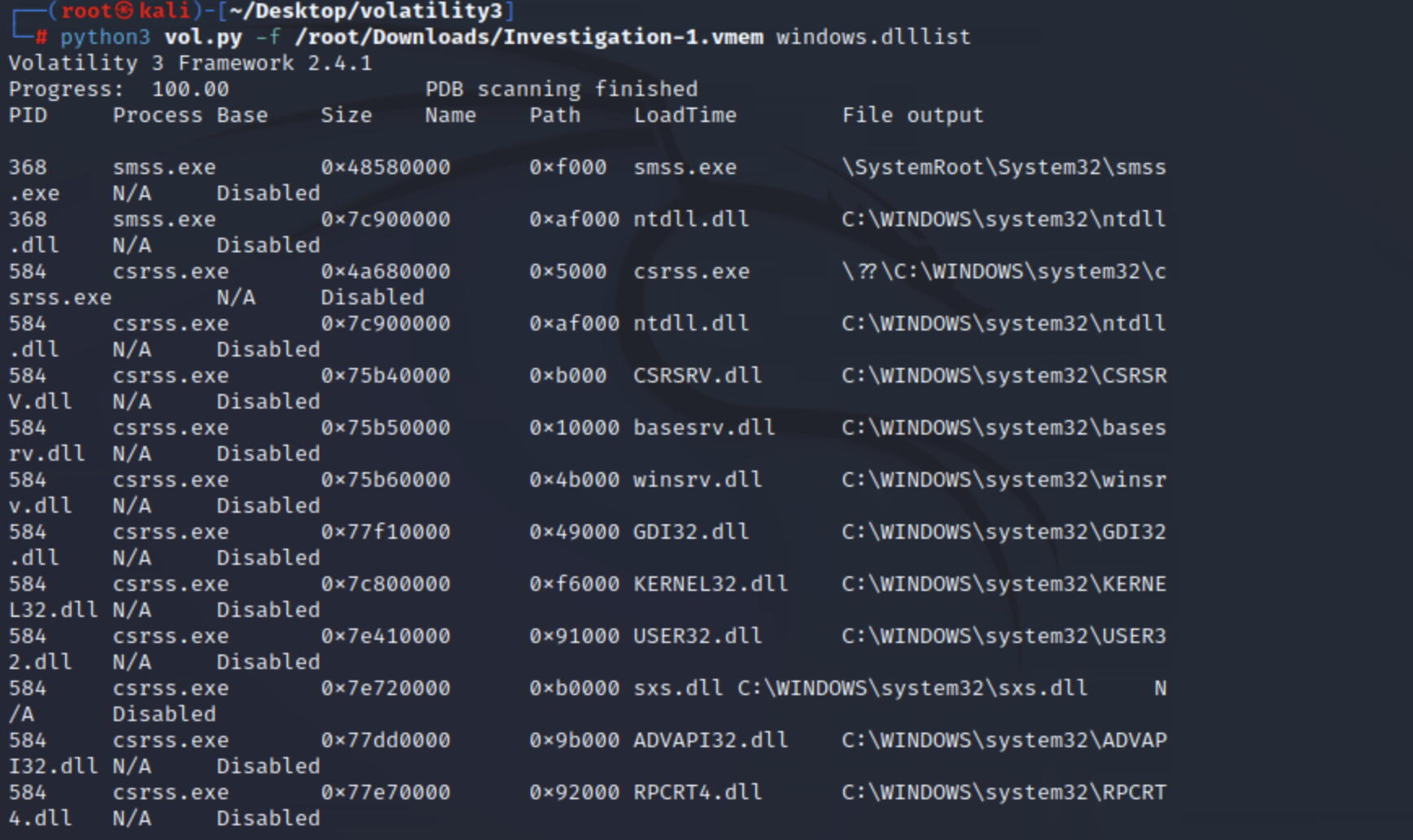
dlllist
该插件将列出提取时与进程关联的所有DLL 。一旦您进行了进一步的分析并可以将输出过滤到特定的 DLL,这可能会特别有用,该 DLL 可能是您认为系统上存在的特定类型的恶意软件的指标。
python3 vol.py -f <file> windows.dlllist
实例:
恶意进程追踪和检测
malfind
该插件将尝试识别注入的进程及其 PID,以及受感染区域的偏移地址和 Hex、Ascii 和反汇编视图。该插件通过扫描堆并识别设置了可执行位RWE or RX和/或磁盘上没有内存映射文件(无文件恶意软件)的进程来工作。
根据malfind识别的内容,注入的区域会发生变化。MZ 标头是 Windows 可执行文件的指示符。注入的区域也可以指向需要进一步分析的 shellcode。
命令:
python3 vol.py -f <file> windows.malfind
实例:
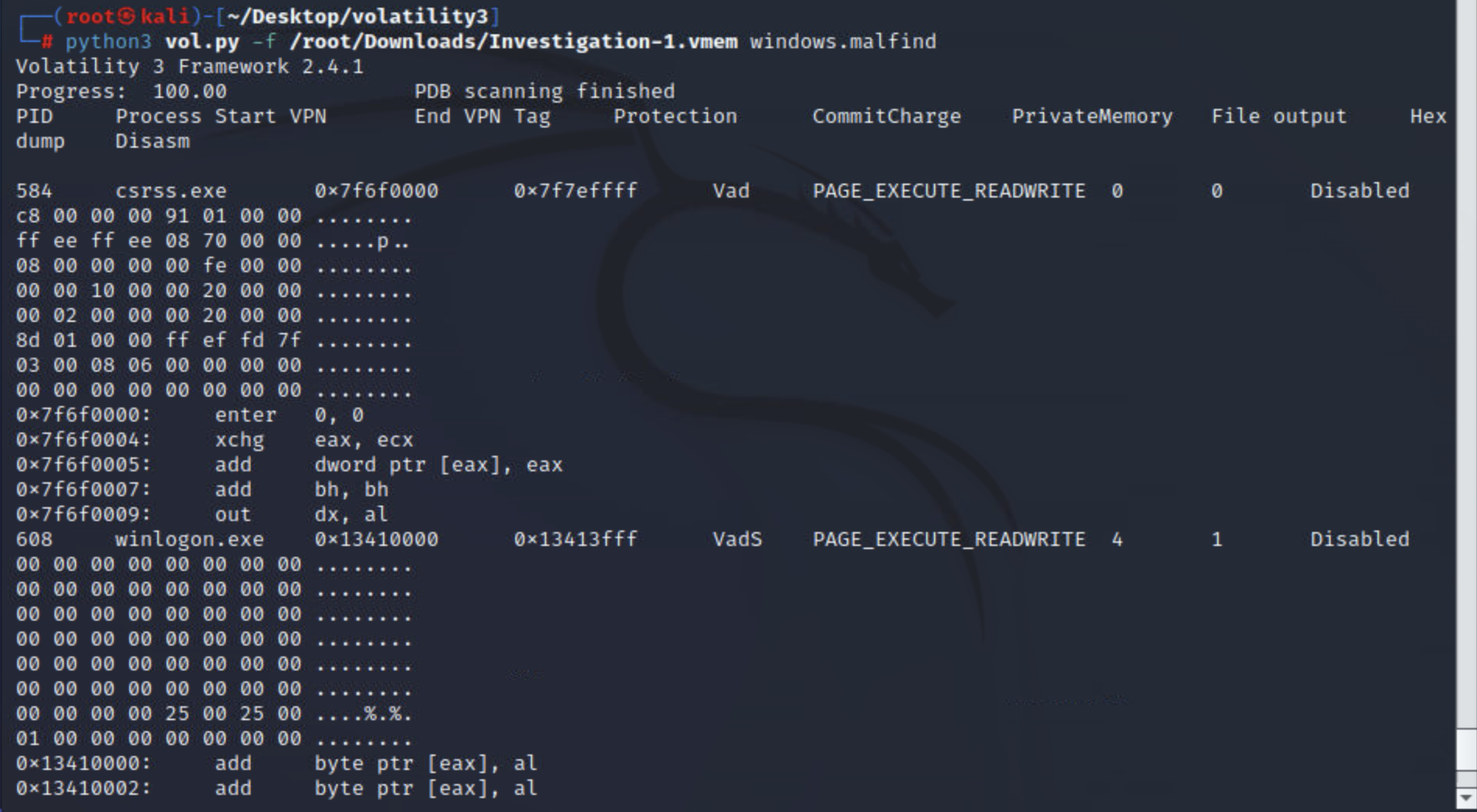
yarascan
yarascan将针对规则集搜索字符串、模式和复合规则。您可以使用 YARA 文件作为参数或在命令行中列出规则。
命令:
python3 vol.py -f <file> windows.yarascan
高级内存取证
ssdt
该ssdt插件将搜索挂钩并输出其结果。合法的应用程序可以使用挂钩,因此由您作为分析师来识别什么是恶意的。简要概述什么是 SSDT 挂钩:SSDT代表系统服务描述符表; Windows 内核使用此表来查找系统功能。攻击者可以挂接到此表并修改指针以指向 rootkit 控制的位置。
可能有数百个表条目ssdt将被转储;然后,您将不得不进一步分析输出或与基线进行比较。建议在调查最初的妥协并将其作为您的主要调查的一部分进行处理后使用此插件。
命令:
python3 vol.py -f <file> windows.ssdt
实例:
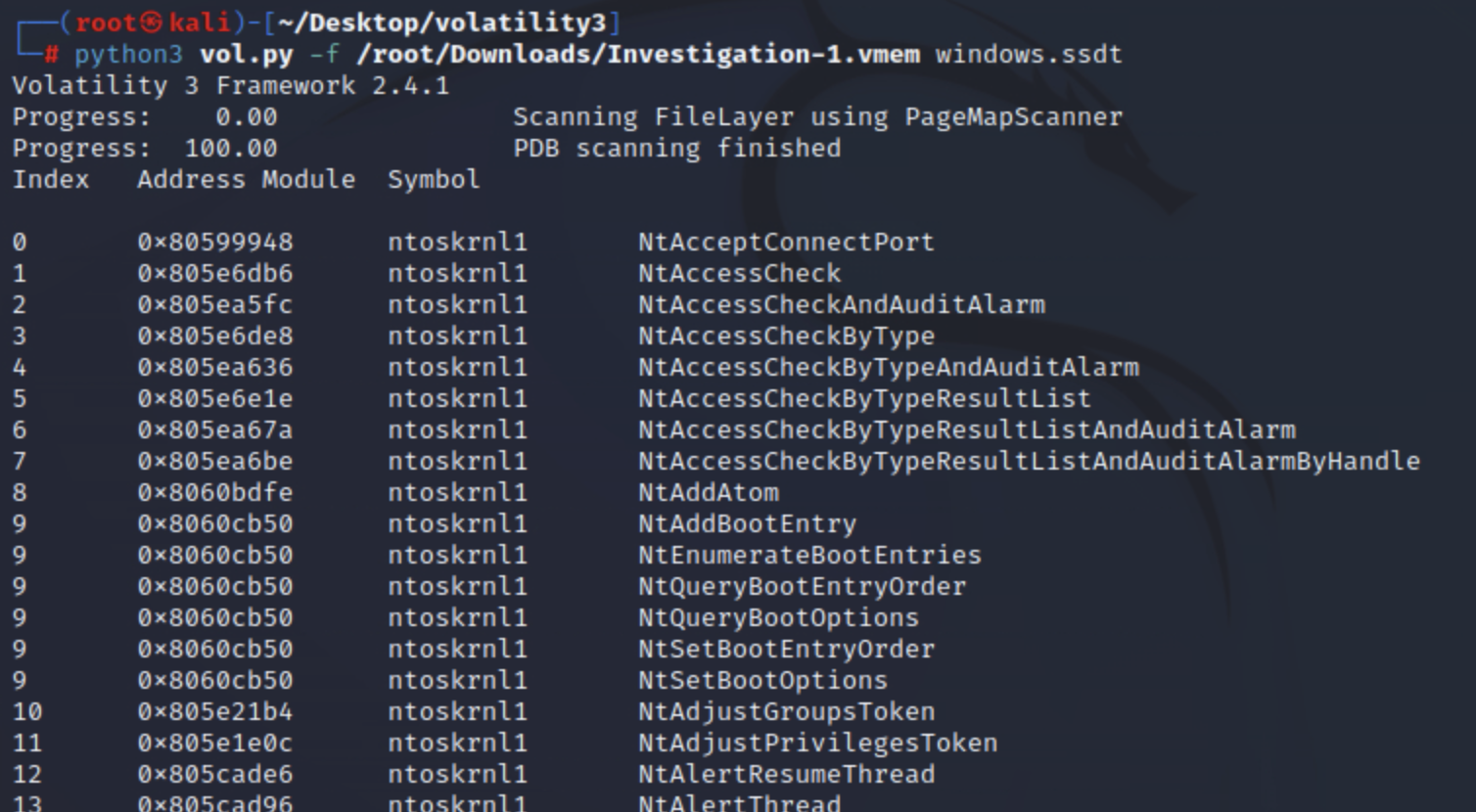
Volatility 提供了两个插件来列出驱动程序。
modules
该modules插件将转储已加载内核模块的列表;这对于识别活动的恶意软件很有用。但是,如果恶意文件正在等待或隐藏,此插件可能会错过它。
一旦您进一步调查并找到可用作搜索和过滤输入的潜在指标,最好使用此插件。
命令:
python3 vol.py -f <file> windows.modules
实例:
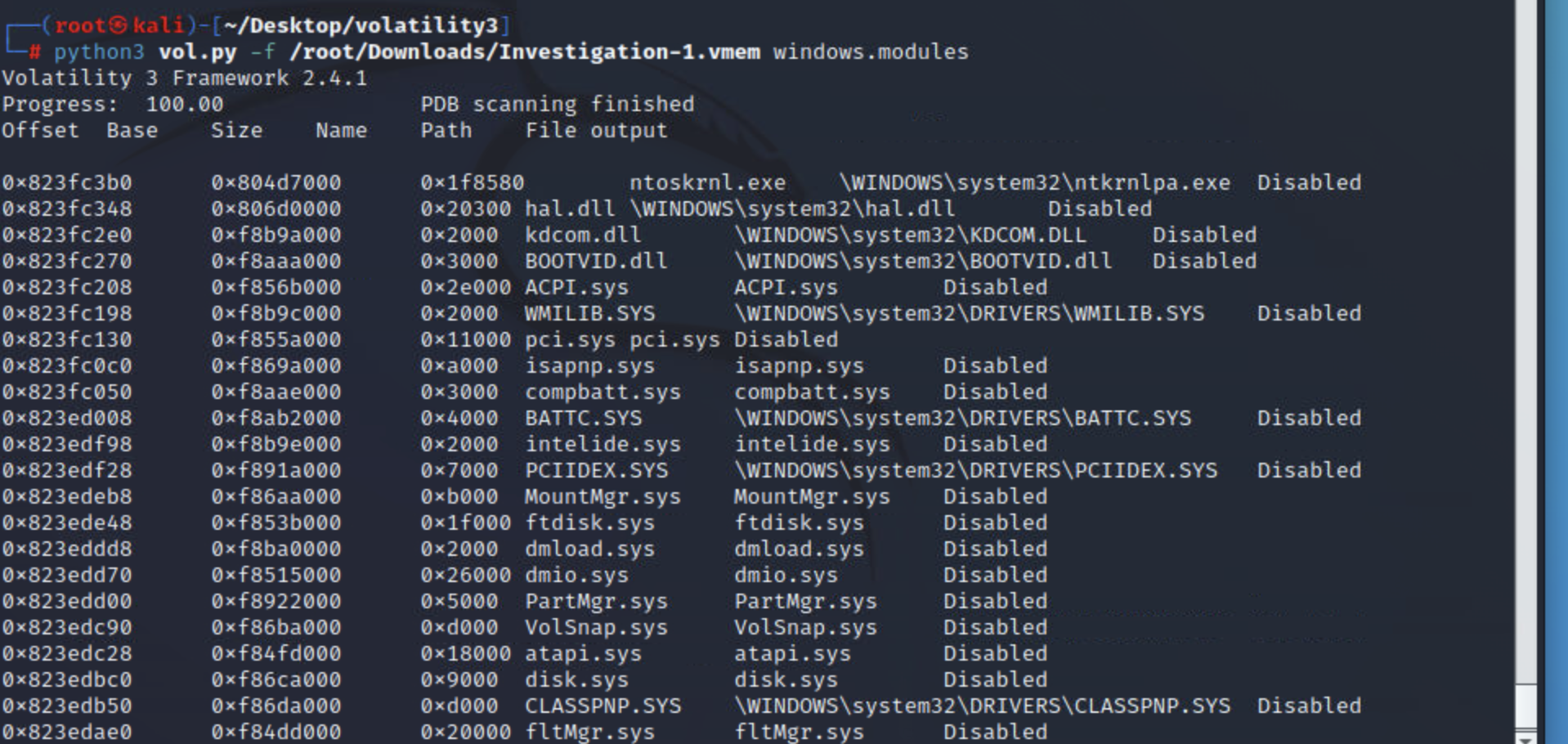
driverscan
该driverscan插件将在提取时扫描系统上存在的驱动程序。该插件可以帮助识别内核中modules插件可能遗漏或隐藏的驱动程序文件。
与上一个插件一样,再次建议在继续使用此插件之前先进行调查。也建议modules之前看一下插件driverscan。
命令:
python3 vol.py -f <file> windows.driverscan
实例:
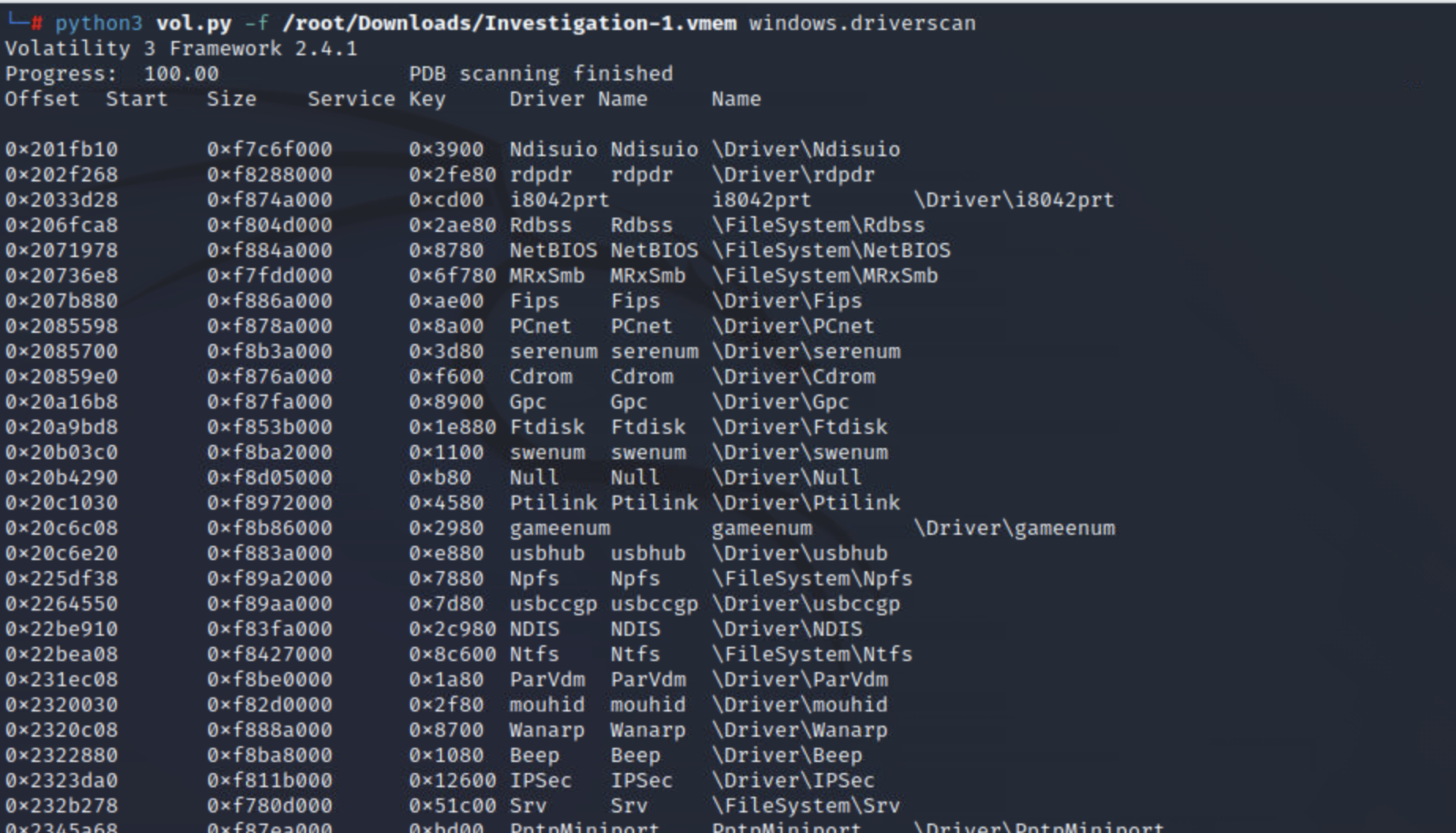
实操
开始实操
通过以上命令得知1,2两道题答案
第三小题:
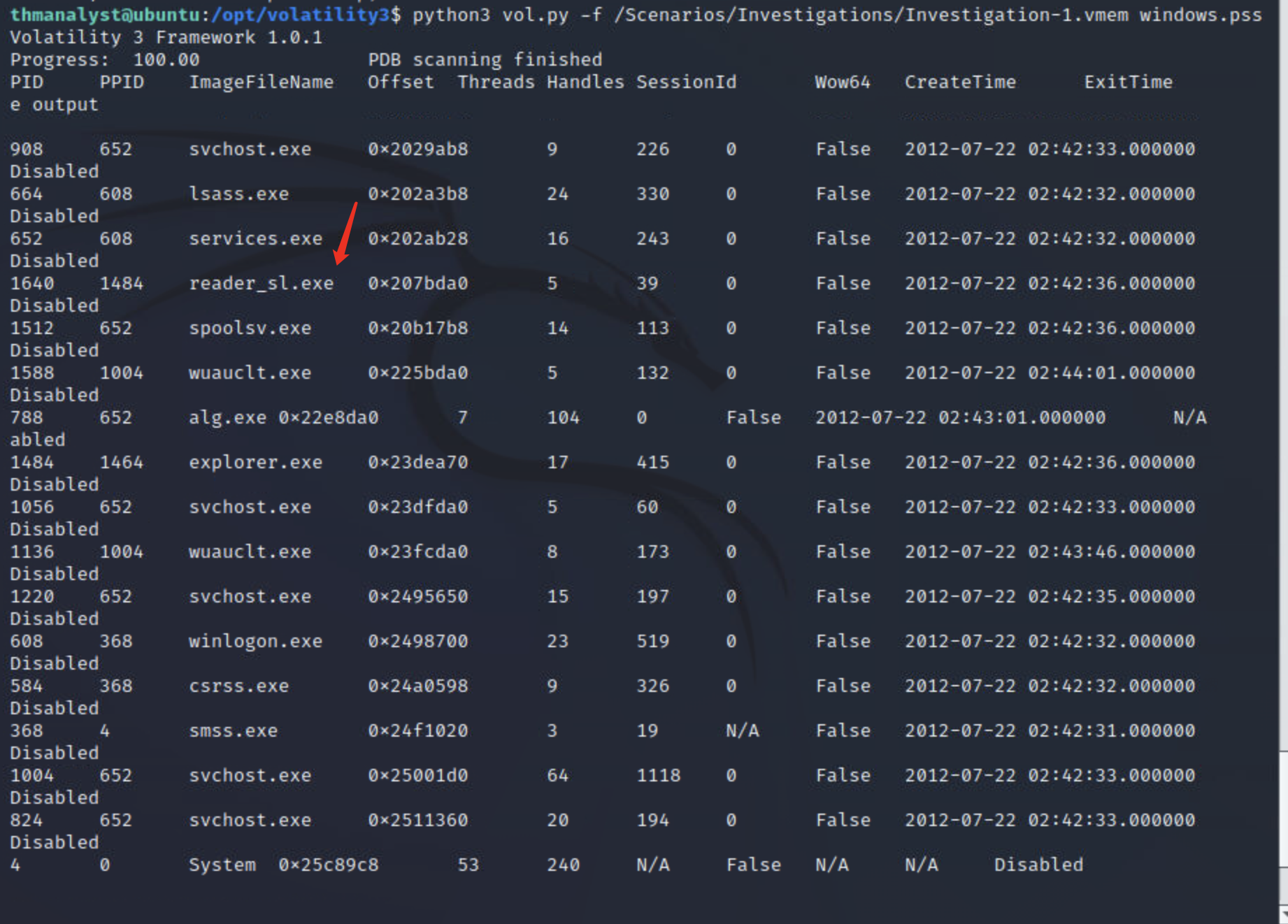
结合题目简介中的提示伪装成 Adobe 文档的银行木马
判断可疑进程为reader_sl.exe
第四,五,六小题:
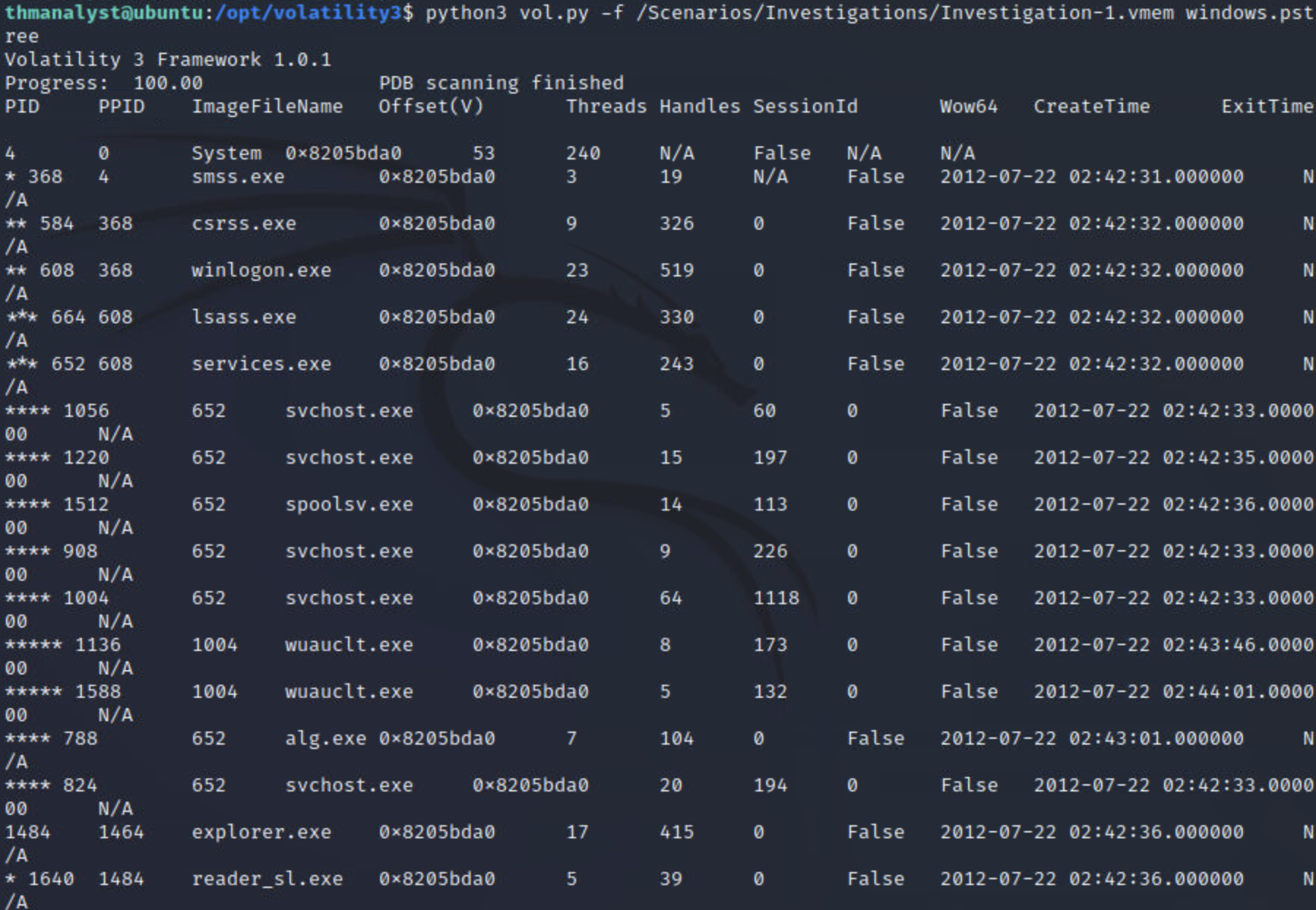
ppid代表当前进程的父进程ID
所以定位到父进程为explorer.exe
下面一个问题百度了下
在 volatility2 以及 volatility3 beta 版本中,允许使用 procdump 来转储进程,
但这一插件在新版本的 volatility3 中被取消,我们应该使用:
python vol.py -f mydump.vmem -o <out_path> windows.memmap.Memmap --pid <pid> --dump
进行转储(本地测试有时候会失败),或者使用:
python vol.py -f mydump.vmem -o <out_path> windows.pslist.PsList --pid <pid> --dump
如果不加 -o
这里我们用了下面一个命令转储
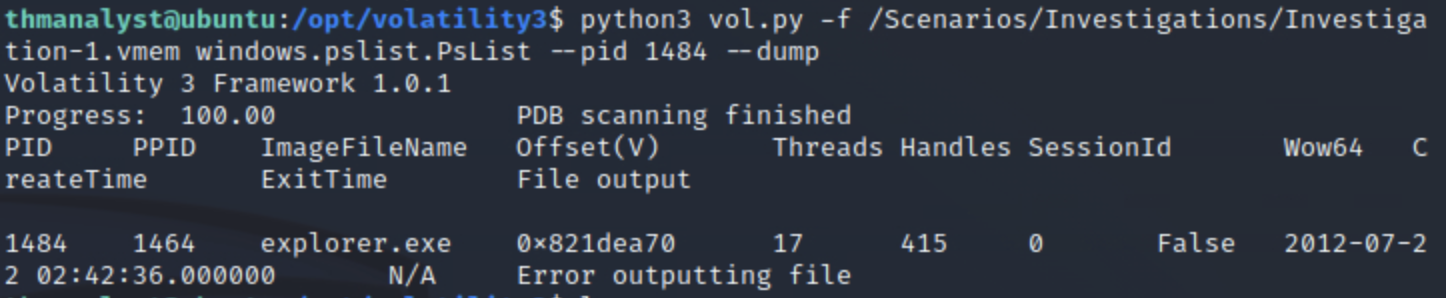
接着使用string命令检索关键字
strings dump.vmem | grep -i "user-agent"
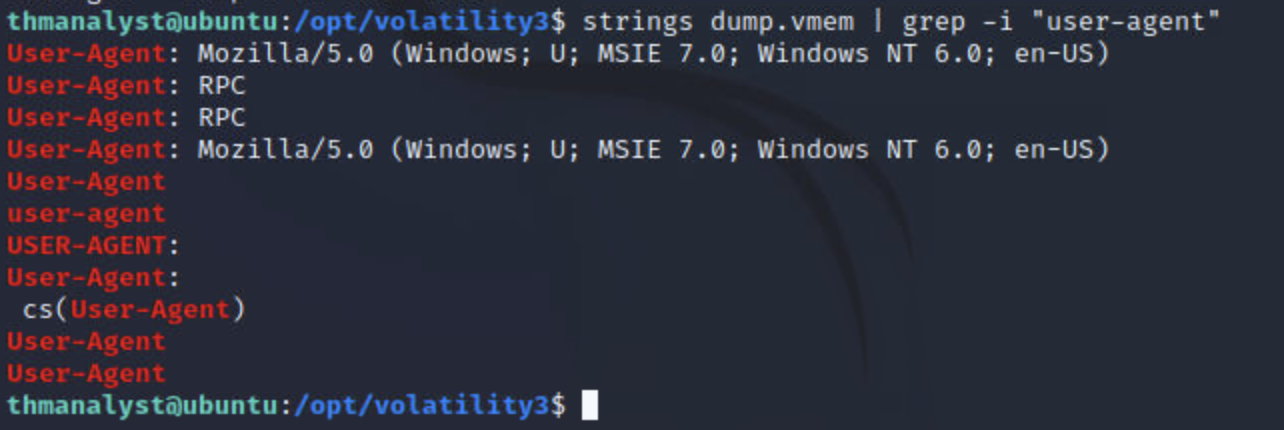
成功找到用户代理
下面一个问题,继续使用命令检索
strings dump.vmem | grep -i "Chase"
检索到大量关键字,证明存在
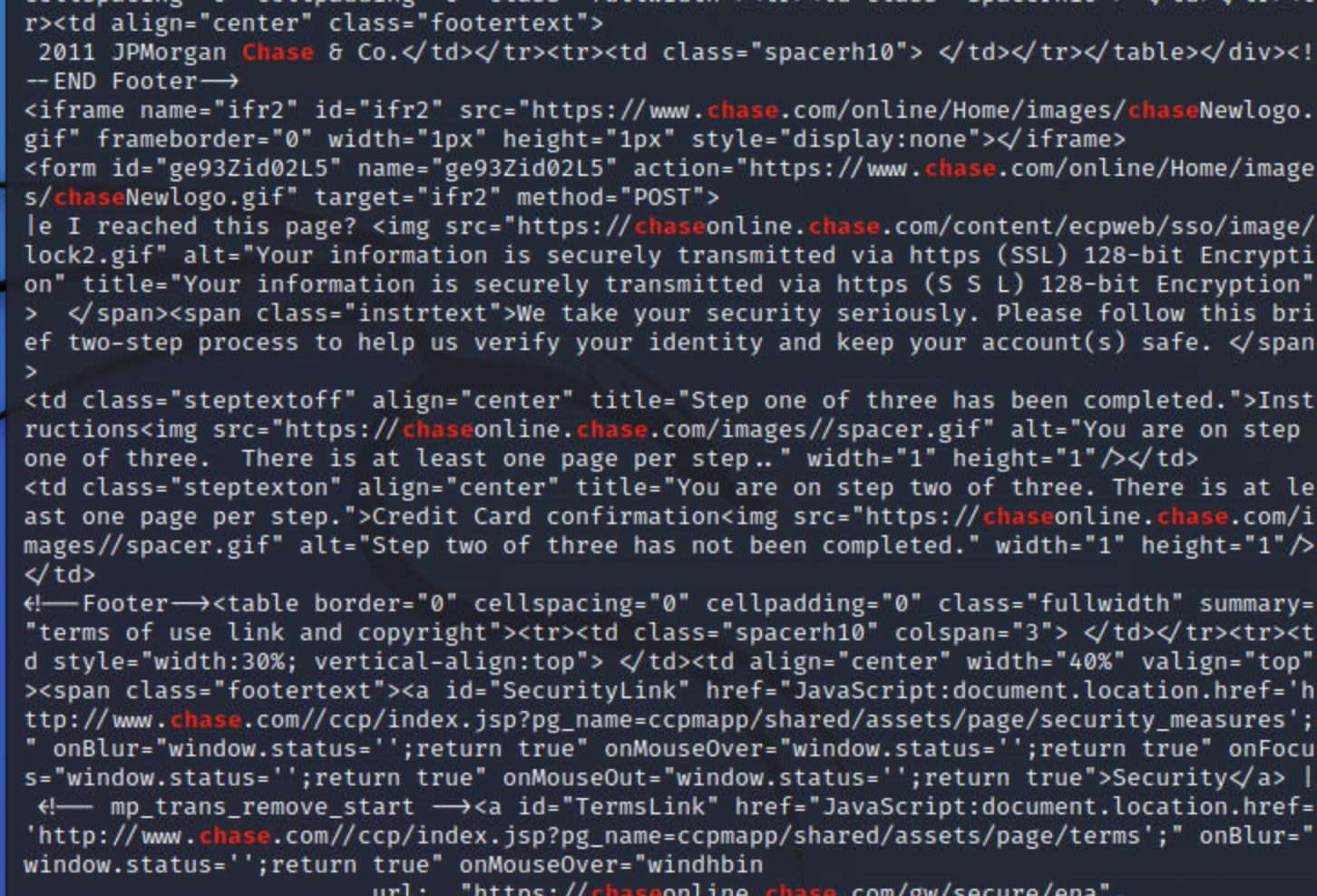
case 2
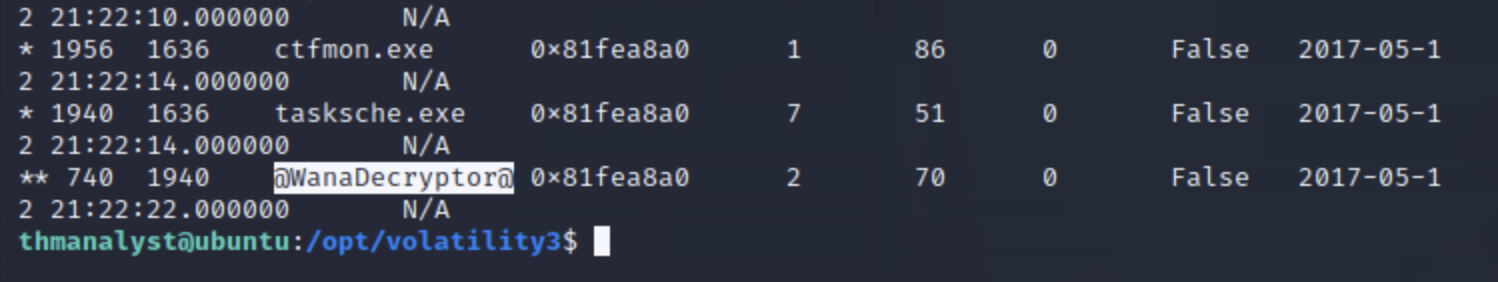
python3 vol.py -f /Scenarios/Investigations/Investigation-2.raw windows.pstree
找到pid740的进程

python3 vol.py -f /Scenarios/Investigations/Investigation-2.raw windows.dll | grep 740
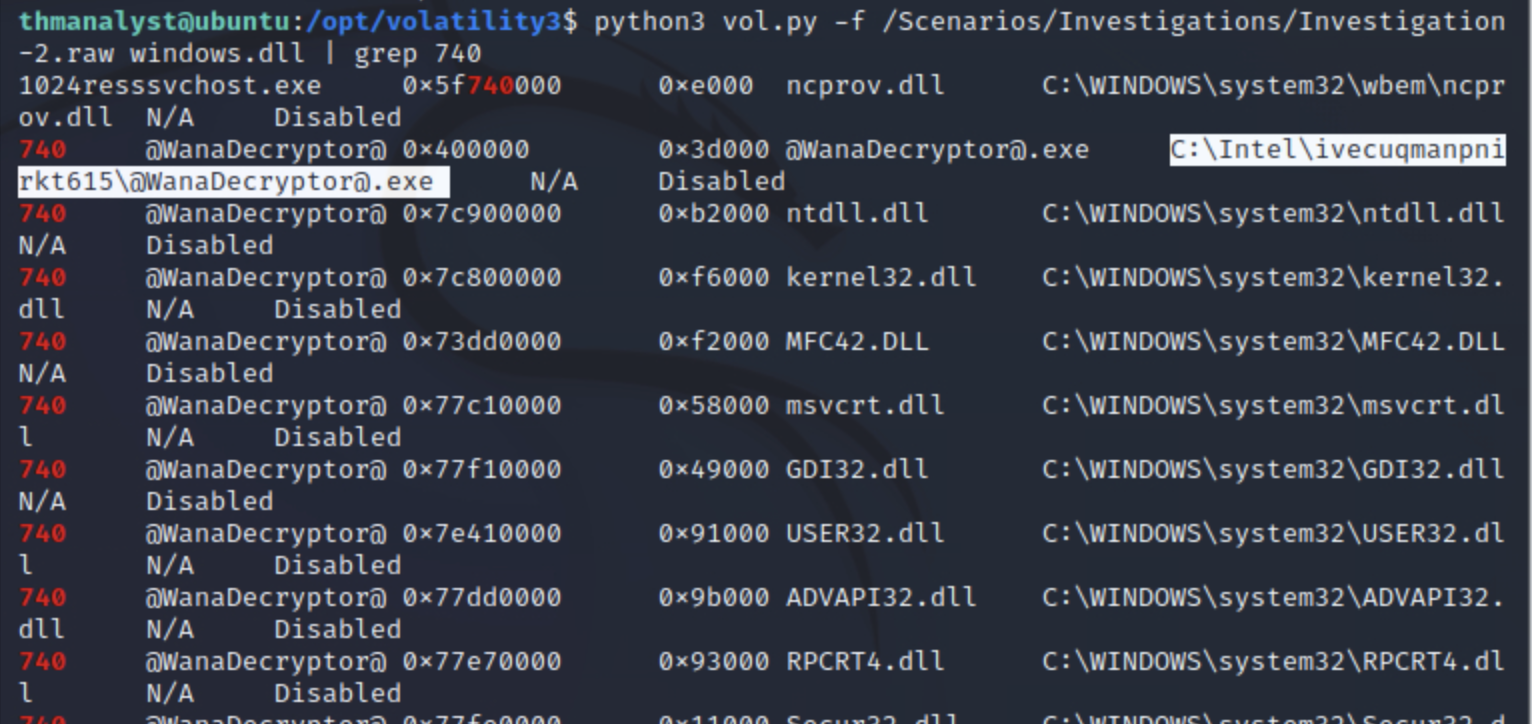
成功找到路径
python3 vol.py -f /Scenarios/Investigations/Investigation-2.raw windows.pstree
同样还是在
python3 vol.py -f /Scenarios/Investigations/Investigation-2.raw windows.pstree
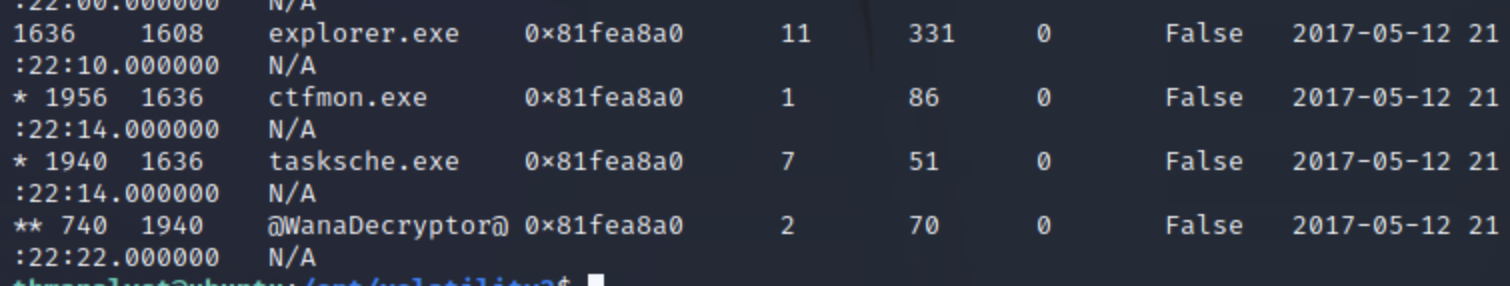

接下来一个问题谷歌了下
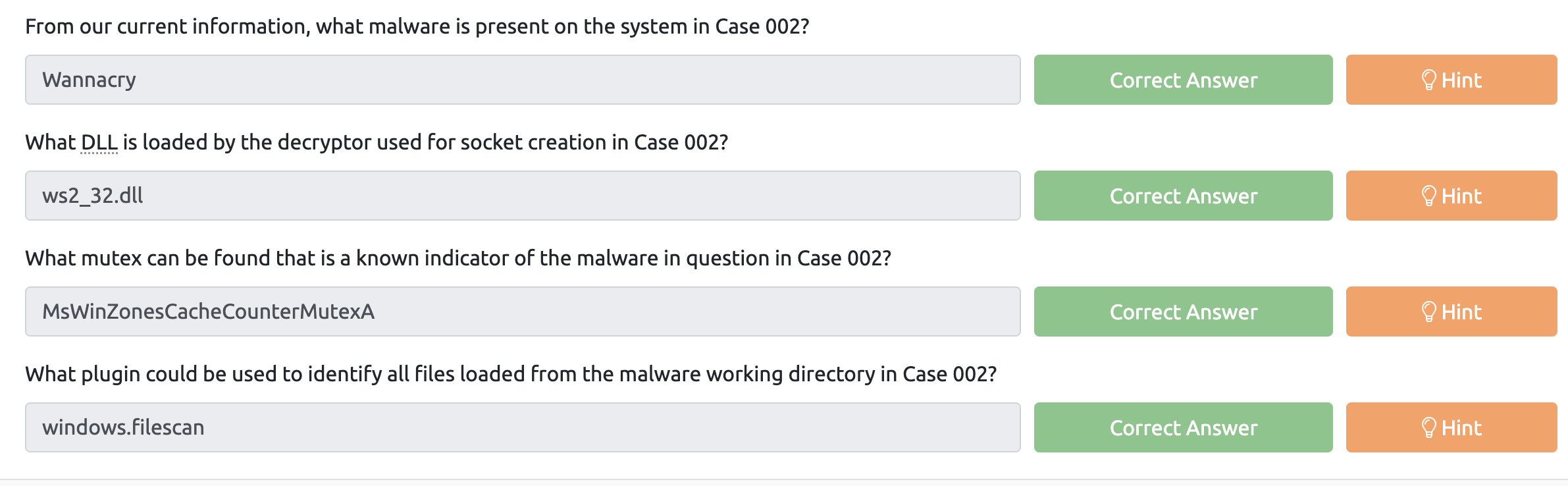
最后几道题目连分析带猜的
病毒详细分析见吾爱大佬分析文章:
https://www.52pojie.cn/thread-1573058-1-1.html

Comments NOTHING